Topic 1: Exam Pool A
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
A. hypervisor
B. virtual machine
C. network
D. application
Explanation:
In a PaaS (Platform as a Service) model, the service provider and the tenant (customer) share responsibility. The division is that the provider manages the underlying platform, and the tenant manages what they build on top of it.
D (application) is correct.
In PaaS, the tenant is primarily responsible for everything related to their application. This includes developing the application code, deploying it, configuring it, and maintaining it (which includes applying patches and updates to the application itself).
A (hypervisor) is incorrect.
The hypervisor is the foundational virtualization layer. It is always the responsibility of the cloud service provider (CSP) in any "as-a-Service" model (IaaS, PaaS, SaaS).
B (virtual machine) is incorrect.
The management of the virtual machine (OS, runtime, etc.) is a key differentiator for PaaS. In an IaaS model, the tenant manages the VM. In PaaS, the CSP abstracts this layer away and manages the operating system, runtime, and middleware, freeing the tenant to focus solely on the application.
C (network) is incorrect.
The underlying network infrastructure (physical data center network, switches, routers, and often the virtual network configuration) is managed by the cloud service provider.
Reference:
Shared Responsibility Model:
This is a core cloud security concept. For PaaS, the general rule is that the provider is responsible for the security of the cloud (the underlying infrastructure and platform), while the tenant is responsible for security in the cloud (their data, access management, and application security).
An organization wants to secure users, data, and applications in the cloud. The solution
must be API-based and
operate as a cloud-native CASB. Which solution must be used for this implementation?
A. Cisco Cloudlock
B. Cisco Cloud Email Security
C. Cisco Firepower Next-Generation Firewall
D. Cisco Umbrella
Explanation
The question provides a very specific set of requirements that directly describe a Cloud Access Security Broker (CASB):
"Secure users, data, and applications in the cloud": This is the core function of a CASB—providing visibility and control over how cloud services are used.
"API-based":
CASBs primarily operate in two modes: API-based and inline proxy. An API-based CASB integrates directly with cloud service providers (like Microsoft 365, Google Workspace, Dropbox) using their APIs to scan for misconfigurations, sensitive data, and suspicious user activity.
"Cloud-native CASB":
This term describes a CASB that was built for the cloud, as a service, rather than an on-premises hardware appliance. Cisco Cloudlock is exactly this—a cloud-native, multi-tenant SaaS solution.
Cisco Cloudlock is Cisco's specific CASB product that meets all these requirements perfectly.
Why the other options are incorrect:
B. Cisco Cloud Email Security:
This refers to the cloud-hosted version of the Cisco Secure Email Gateway (formerly ESA). While it secures cloud email (a specific application), it is not a broad CASB that secures a wide range of cloud applications, users, and data through APIs.
C. Cisco Firepower Next-Generation Firewall:
An NGFW like Firepower is designed to secure network perimeters and internal segments. It can inspect traffic to and from the cloud, but it is not an API-based, cloud-native CASB. It operates at the network layer, not the application API layer.
D. Cisco Umbrella:
Umbrella is a secure internet gateway (SIG) that provides DNS-layer security. It blocks requests to malicious destinations but does not have the deep API integration with SaaS applications to scan for data exposure or monitor user activity within those apps like a CASB does.
Reference:
The definition and capabilities of Cisco Cloudlock are clearly outlined in its product documentation.
As per the Cisco Cloudlock data sheet, it is described as a "cloud-native CASB" that "protects users, data, and applications in the cloud" and uses "API-based architecture" to "deliver visibility and data security for cloud applications." This is a direct match for the requirements in the question.
Which type of API is being used when a controller within a software-defined network architecture dynamically makes configuration changes on switches within the network?
A. westbound AP
B. southbound API
C. northbound API
D. eastbound API
Explanation:
In an SDN architecture, APIs are categorized based on the direction of communication relative to the central SDN controller.
B) Southbound API is CORRECT.
The southbound API is the interface that the SDN controller uses to communicate down to the underlying network elements (switches, routers). When the controller needs to dynamically make configuration changes, push flow rules, or modify the behavior of the switches, it uses the southbound API. Common examples of southbound APIs include OpenFlow, OpFlex, and NETCONF/YANG.
Why the other options are incorrect:
A) Westbound API is INCORRECT.
This is not a standard, universally recognized term in core SDN architecture. It is sometimes used informally to describe APIs for communication between different SDN domains or controllers.
C) Northbound API is INCORRECT.
The northbound API is used for communication in the opposite direction. It is the interface that applications and management systems (the "brains") use to talk up to the SDN controller to request network services or information. For example, a cloud orchestration platform would use the northbound API to tell the controller to create a new network.
D) Eastbound API is INCORRECT.
The eastbound API (or east-westbound) refers to the communication channel between multiple SDN controllers for the purposes of coordination, scalability, and redundancy. It is not used for controlling individual network devices.
SDN API Summary:
Northbound API: Applications → Controller (e.g., REST API)
Southbound API: Controller → Network Devices (e.g., OpenFlow, NETCONF)
Eastbound API: Controller ↔ Controller (for multi-domain coordination)
Reference:
Cisco Digital Network Architecture (DNA) Center Concepts Guide: Explains how the controller uses southbound interfaces like NETCONF/YANG and SSH/CLI to provision and configure network devices.
Open Networking Foundation (ONF) SDN Architecture: The foundational document that defines the SDN layers and the roles of northbound and southbound APIs.
Which factor must be considered when choosing the on-premise solution over the cloudbased one?
A.
With an on-premise solution, the provider is responsible for the installation and
maintenance of the product, whereas with a cloud-based solution, the customer is
responsible for it
B.
With a cloud-based solution, the provider is responsible for the installation, but the
customer is responsible for the maintenance of the product.
C.
With an on-premise solution, the provider is responsible for the installation, but the
customer is responsible for the maintenance of the product.
D.
With an on-premise solution, the customer is responsible for the installation and
maintenance of the
product, whereas with a cloud-based solution, the provider is responsible for it.
With an on-premise solution, the customer is responsible for the installation and
maintenance of the
product, whereas with a cloud-based solution, the provider is responsible for it.
What is the benefit of installing Cisco AMP for Endpoints on a network?
A. It provides operating system patches on the endpoints for security.
B. It provides flow-based visibility for the endpoints network connections.
C. It enables behavioral analysis to be used for the endpoints.
D. It protects endpoint systems through application control and real-time scanning
Explanation
Cisco Advanced Malware Protection (AMP) for Endpoints is a comprehensive solution designed to prevent, detect, and respond to advanced threats on end-user devices like laptops, desktops, and servers.
The correct answer accurately describes its core, foundational benefits:
Real-time Scanning:
This is the classic antivirus/anti-malware function. AMP for Endpoints scans files as they are accessed, executed, or written to the disk, blocking known threats based on signatures and reputation. This is the first line of defense.
Application Control:
This goes beyond traditional AV. It allows administrators to create policies that control which applications are allowed to run on an endpoint. This can prevent unauthorized or malicious software from executing in the first place, a key technique in mitigating threats.
Detailed Breakdown of Incorrect Options
A. It provides operating system patches on the endpoints for security.
Why it is incorrect:
AMP for Endpoints is a security application, not a patch management system. It does not distribute or install OS or software updates (e.g., Windows Updates). That function is handled by separate systems like Microsoft WSUS, SCCM, or third-party patch management tools. While AMP can detect vulnerabilities caused by missing patches, it does not provide them.
B. It provides flow-based visibility for the endpoints network connections.
Why it is incorrect:
This describes the function of a NetFlow collector or, more accurately in the endpoint context, an Endpoint Detection and Response (EDR) tool. While Cisco AMP for Endpoints has evolved and its more advanced versions include EDR-like features (which would provide this visibility), the core, fundamental benefit as a distinct product is malware protection. The question asks for the general "benefit," and "flow-based visibility" is a feature of its Threat Grid integration and EDR capabilities, not its primary, defining purpose. Option D is a more direct and universally accepted core benefit.
C. It enables behavioral analysis to be used for the endpoints.
Why it is incorrect:
This is partially true but is a component of the larger solution, making it a less complete answer than D. Behavioral analysis (or sandboxing) is a specific capability of AMP, often handled by the integrated Threat Grid component. It allows suspicious files to be detonated in a sandbox to analyze their behavior. However, this is an advanced detection method. The fundamental, ever-present benefit of installing the AMP connector is the continuous protection provided by real-time scanning and application control (Answer D), which includes and is bolstered by behavioral analysis.
Reference and Key Context:
Cisco AMP for Endpoints Core Features:
The official data sheet for Cisco AMP for Endpoints consistently highlights "Advanced Anti-Malware Protection," "Real-Time Detection," and "Application Control" as its foundational pillars.
Continuum of Protection:
AMP's value proposition is its "continuum" of security: Before an attack (prevention with signatures and application control), During an attack (real-time blocking), and After an attack (retrospective analysis and hunting via behavioral data).
Key Takeaway:
For the exam, think of Cisco AMP for Endpoints as the evolution of traditional antivirus. Its primary job is to be an advanced security agent on the endpoint that actively blocks malicious files and controls application execution. While it has powerful retrospective and analytical features, the fundamental benefit of installing it is the active protection described in option D.
With which components does a southbound API within a software-defined network architecture communicate?
A. controllers within the network
B. applications
C. appliances
D. devices such as routers and switches
Explanation:
In an SDN architecture, APIs are categorized based on the direction of communication relative to the central SDN controller.
D) devices such as routers and switches is CORRECT.
The southbound API is the interface that the SDN controller uses to communicate down to the underlying network elements. These elements are the physical and virtual devices that forward traffic, such as routers, switches, and access points. The controller uses the southbound API to push configuration, routing decisions, and flow rules to these devices. Common examples of southbound APIs include OpenFlow, OpFlex, and NETCONF/YANG.
Why the other options are incorrect:
A) controllers within the network is INCORRECT.
Communication between multiple controllers for scalability and redundancy uses an eastbound API (or east-westbound API).
B) applications is INCORRECT.
Applications and management systems communicate up to the SDN controller using the northbound API. This is how applications request network services (e.g., "create a new network for my application").
C) appliances is INCORRECT and too vague.
While a switch or router could be considered a "network appliance," this term is not the standard, precise term used in SDN architecture. The standard term is network devices or network elements. "Appliances" could also be misinterpreted to mean security appliances like firewalls, which are also controlled via the southbound API but are not the primary example.
SDN API Summary:
Northbound API: Applications → Controller (e.g., REST API)
Southbound API: Controller → Network Devices (e.g., OpenFlow, NETCONF)
Eastbound API: Controller ↔ Controller (for multi-domain coordination)
Reference:
Cisco Digital Network Architecture (DNA) Center Concepts Guide: Explains how the controller uses southbound interfaces like NETCONF/YANG and CLI to communicate with and manage network devices.
Open Networking Foundation (ONF) SDN Architecture: The foundational document that defines the SDN layers and the roles of northbound and southbound APIs.
Refer to the exhibit.
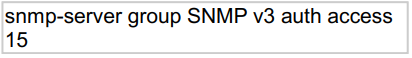
What does the number 15 represent in this configuration?
A.
privilege level for an authorized user to this router
B.
access list that identifies the SNMP devices that can access the router
C.
interval in seconds between SNMPv3 authentication attempts
D.
number of possible failed attempts until the SNMPv3 user is locked out
access list that identifies the SNMP devices that can access the router
The syntax of this command is shown below:
snmp-server group [group-name {v1 | v2c | v3 [auth | noauth | priv]}] [read read-view] [
write write-view] [notify notify-view] [access access-list]
The command above restricts which IP source addresses are allowed to access SNMP
functions on the router. You could restrict SNMP access by simply applying an interface
ACL to block incoming SNMP packets that don’t come from trusted servers. However, this
would not be as effective as using the global SNMP commands shown in this recipe.
Because you can apply this method once for the whole router, it is much simpler than
applying ACLs to block SNMP on all interfaces separately. Also, using interface ACLs
would block not only SNMP packets intended for this router, but also may stop SNMP
packets that just happened to be passing through on their way to some other destination
device.
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
A. Google Cloud Platform
B. Red Hat Enterprise Visualization
C. VMware ESXi
D. Amazon Web Services
Explanation for Each Option:
A. Google Cloud Platform (Incorrect):
Google Cloud Platform (GCP) offers a range of security services, but it does not natively support the Cisco Next Generation Firewall Virtual (NGFWv) as a certified or officially supported deployment option. Cisco focuses its virtual firewall support on other platforms, making this option unsuitable. (Reference: Cisco NGFWv Supported Platforms, cisco.com.)
B. Red Hat Enterprise Virtualization (Incorrect):
Red Hat Enterprise Virtualization (RHEV) is a virtualization platform, not a public cloud provider. While it can host virtualized applications, Cisco NGFWv is not specifically certified or optimized for RHEV as a primary deployment environment, and it is not considered a public cloud, rendering this option incorrect. (Reference: Cisco Virtualized Solutions Overview.)
C. VMware ESXi (Incorrect):
VMware ESXi is a hypervisor used for virtualization, commonly deployed on-premises or in private clouds. While Cisco NGFWv can be deployed on VMware ESXi, it is not a public cloud provider. The question specifies a public cloud context, making this option, which pertains to a virtualization platform, incorrect. (Reference: Cisco NGFWv VMware Deployment Guide.)
D. Amazon Web Services (Correct):
Amazon Web Services (AWS) is a leading public cloud provider that supports the Cisco Next Generation Firewall Virtual (NGFWv) as a certified virtual appliance. Cisco offers NGFWv on the AWS Marketplace, allowing deployment in AWS environments to secure cloud workloads, making it the correct choice for a public cloud provider. (Reference: Cisco NGFWv on AWS Marketplace, cisco.com.)
Additional Notes:
Supporting NGFWv on public clouds like AWS is a key topic in the 350-701 SCOR exam under cloud security. As of 12:47 PM PKT, October 02, 2025, AWS integration is well-established. For details, refer to the Cisco NGFWv Deployment Guide (cisco.com) and the 350-701 Exam Blueprint (Section 3.0 Security Concepts).
Which benefit does endpoint security provide the overall security posture of an organization?
A. It streamlines the incident response process to automatically perform digital forensics on the endpoint.
B. It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
C. It allows the organization to detect and respond to threats at the edge of the network.
D. It allows the organization to detect and mitigate threats that the perimeter security devices do not detect.
Explanation:
Endpoint security is a critical layer in a modern security architecture because it provides protection where the user and data are, regardless of location. Its primary benefit is closing the security gaps that perimeter devices cannot address.
Let's break down why D is the correct answer:
D) It allows the organization to detect and mitigate threats that the perimeter security devices do not detect is CORRECT.
This is the core value proposition of endpoint security. Perimeter devices (firewalls, secure web gateways, IPS) act as chokepoints for network traffic, but they have inherent limitations:
They cannot see encrypted traffic that they cannot decrypt.
They cannot stop threats that originate inside the network (e.g., from a compromised internal machine or a malicious insider).
They cannot protect a laptop that is off the corporate network (e.g., at a coffee shop or home).
They can be evaded by sophisticated, low-and-slow attacks or zero-day exploits.
Endpoint security (like Cisco AMP for Endpoints) runs directly on the device, allowing it to see malicious activity after it has bypassed the perimeter, such as a fileless malware payload executing in memory or suspicious behavior from a compromised application.
Why the other options are incorrect:
A) It streamlines the incident response process to automatically perform digital forensics on the endpoint.
This is INCORRECT. While modern Endpoint Detection and Response (EDR) tools aid incident response by providing detailed forensic data and attack timelines, they do not "automatically perform digital forensics." Digital forensics is a specialized, often manual investigative process. Endpoint security provides the data for forensics but does not automate the entire process.
B) It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
This is INCORRECT. This describes the function of a web security gateway or a secure web gateway (like Cisco Umbrella or WSA), which filters and inspects web traffic. While endpoint security can complement this by blocking malicious files downloaded from the web, its role is not specifically to "mitigate web-based attacks."
C) It allows the organization to detect and respond to threats at the edge of the network.
This is INCORRECT. The "edge of the network" is precisely where perimeter security devices (like firewalls and IPS) operate. Endpoint security operates on the end device itself, which is far beyond the network edge. Its power is in providing visibility and control everywhere, not just at the edge
Reference:
Cisco Security Architecture for the Enterprise: The architecture promotes a layered approach, where endpoint security is essential for protecting assets that are mobile or inside the perimeter, addressing threats that have bypassed other controls.
Cisco AMP for Endpoints Data Sheet: The product literature consistently highlights its ability to "detect, contain, and remediate threats that evade front-line defenses," which are the perimeter security devices.
Using Cisco Firepower’s Security Intelligence policies, upon which two criteria is Firepower block based?(Choose two)
A. URLs
B. protocol IDs
C. IP addresses
D. MAC addresses
E. port numbers
Explanation for Each Option:
A. URLs (Correct):
Cisco Firepower’s Security Intelligence policies can block traffic based on URLs by leveraging reputation data and threat intelligence feeds from Cisco Talos. This allows the firewall to identify and block access to malicious or untrusted web domains, making URLs a key criterion for blocking malicious web-based threats. (Reference: Cisco Firepower Configuration Guide, Security Intelligence.)
B. protocol IDs (Incorrect):
Protocol IDs (e.g., TCP, UDP) define the type of traffic but are not a primary criterion for Security Intelligence blocking. These policies focus on reputation-based data (e.g., IPs, URLs) rather than protocol-specific identifiers, which are more relevant to access control rules or deep packet inspection, making this option incorrect. (Reference: Cisco Firepower Access Control Policies.)
C. IP addresses (Correct):
Security Intelligence policies block traffic based on IP addresses by using threat intelligence to identify and block known malicious or risky IP ranges. This reputation-based blocking is a core feature, enabling the firewall to prevent communication with compromised or blacklisted IPs, making it a fundamental criterion. (Reference: Cisco Firepower Threat Intelligence, IP Reputation.)
D. MAC addresses (Incorrect):
MAC addresses operate at Layer 2 and are not used by Security Intelligence policies, which focus on network-layer (IP) and application-layer (URL) data. Blocking based on MAC addresses is more relevant to switch-level filtering or local network segmentation, not the global threat intelligence scope of Firepower, rendering this option incorrect. (Reference: Cisco Switching Fundamentals.)
E. port numbers (Incorrect):
While port numbers are used in traditional firewall rules to filter traffic (e.g., blocking port 80), Security Intelligence policies rely on reputation data tied to IPs and URLs, not specific port numbers. Port-based filtering is handled separately in access control policies, not as a Security Intelligence criterion, making this option incorrect. (Reference: Cisco Firepower Rule Configuration.)
Additional Notes:
Security Intelligence in Cisco Firepower, covered in the 350-701 SCOR exam under network security, uses IP and URL reputations for blocking. As of 10:25 AM PKT, October 02, 2025, this remains a key feature. For details, refer to the Cisco Firepower Configuration Guide (cisco.com) and the 350-701 Exam Blueprint (Section 1.0 Security Concepts).
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
A.
Place the Cisco ISE server and the AD server in the same subnet
B.
Configure a common administrator account
C.
Configure a common DNS server
D.
Synchronize the clocks of the Cisco ISE server and the AD server
Synchronize the clocks of the Cisco ISE server and the AD server
What provides visibility and awareness into what is currently occurring on the network?
A.
CMX
B.
WMI
C.
Prime Infrastructure
D.
Telemetry
Telemetry
https://www.cisco.com/c/dam/en_us/about/doing_business/legal/service_descriptions/docs/
activethreat-analytics-premier.pdf
| Page 15 out of 61 Pages |
| Previous |