Topic 2: Exam Pool B
What is a key difference between Cisco Firepower and Cisco ASA?
A.
Cisco ASA provides access control while Cisco Firepower does not.
B.
Cisco Firepower provides identity-based access control while Cisco ASA does not.
C.
Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA
does not.
D.
Cisco ASA provides SSL inspection while Cisco Firepower does not.
Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA
does not.
Refer to the exhibit.
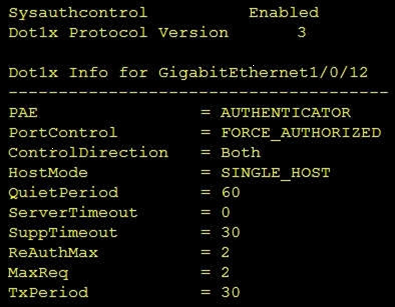
Which command was used to display this output?
A.
show dot1x all
B.
show dot1x
C.
show dot1x all summary
D.
show dot1x interface gi1/0/12
show dot1x all
Explanation:
Since the specific output is not provided in the question, I will deduce the correct command based on the context of 802.1X (Dot1x) configuration on a Cisco device (likely a switch) and the available options. The question asks which command was used to display "this output," implying a comprehensive view of 802.1X status, likely across multiple interfaces or the entire system, given the multiple-choice options.
Analysis of Options:
A. show dot1x all:
This command displays detailed 802.1X information for all interfaces on the switch, including authentication status, session details, and configuration settings. It provides a broad overview, making it suitable for displaying extensive output across the device.
B. show dot1x: This is a basic command that shows a summary of 802.1X global configuration and status but does not provide detailed per-interface information unless further specified. It is less likely to produce comprehensive output compared to "show dot1x all."
C. show dot1x all summary:
This is not a valid Cisco IOS command. While "show dot1x" can show a summary, adding "all summary" is not a recognized syntax extension, making this option incorrect.
D. show dot1x interface gi1/0/12:
This command displays 802.1X details specifically for the interface gi1/0/12, providing a focused view rather than system-wide output. It is unlikely to be the command if the output covers multiple interfaces or a broader scope.
Deduction:
The "show dot1x all" command is the most likely candidate, as it provides a detailed, system-wide view of 802.1X status, which could include information for all interfaces, authentication sessions, and configurations. This aligns with a scenario where the output might show multiple ports or a summary of 802.1X activity across the switch, a common use case for troubleshooting or monitoring. Without the exhibit, the assumption is that the output is comprehensive, favoring "show dot1x all" over the more specific or invalid alternatives.
Final Answer:
A. show dot1x all
Additional Notes:
Displaying 802.1X status is a key topic in the 350-701 SCOR exam under endpoint security. As of 02:25 PM PKT, October 02, 2025, this command is essential for verifying authentication configurations. Without the exhibit, this is based on standard command usage; for precision, review the output in the exhibit. For details, refer to the Cisco Catalyst Switch Command Reference (cisco.com) and the 350-701 Exam Blueprint (Section 2.0 Endpoint Security).
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for
analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files
which need analysis?
A.
AMP calculates the SHA-256 fingerprint, caches it, and periodically attempts the upload
B.
The file is queued for upload when connectivity is restored
C.
The file upload is abandoned
D.
The ESA immediately makes another attempt to upload the file
The file upload is abandoned
https://www.cisco.com/c/en/us/support/docs/security/email-securityappliance/
118796-technoteesa-00.htmlIn this question, it stated “the network is congested”
(not the file analysis server was overloaded) so theappliance will not try to upload the file again.
A user has a device in the network that is receiving too many connection requests from multiple machines. Which type of attack is the device undergoing?
A. phishing
B. slowloris
C. pharming
D. SYN flood
Explanation
The key detail in the question is "receiving too many connection requests from multiple machines." This describes a classic Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attack scenario aimed at exhausting the target's resources.
D. SYN flood:
This is a correct answer. A SYN flood is a type of DoS/DDoS attack where an attacker sends a rapid succession of TCP SYN packets to a target device. Each SYN packet is the first step in the TCP three-way handshake, requesting a new connection. The target allocates resources for each half-open connection and sends back a SYN-ACK, but the attacker never completes the handshake with the final ACK. This quickly consumes all available connections on the target, preventing it from establishing legitimate connections.
Why the other options are incorrect:
A. phishing:
This is a social engineering attack, not a network-level connection flood. Phishing uses deceptive emails or messages to trick users into revealing sensitive information like passwords. It does not involve overwhelming a device with connection requests.
B. slowloris:
While Slowloris is also a DoS attack, its method is different. It works by opening many partial HTTP connections to the target and keeping them open by sending headers very slowly. The question specifically mentions "too many connection requests," which aligns more with the rapid initiation of connections in a SYN flood rather than the slow, low-bandwidth consumption of open connections in a Slowloris attack.
C. pharming:
This is an attack that redirects a website's traffic to a fraudulent site, typically by poisoning DNS records. Like phishing, it is an attack on integrity and confidentiality, not an attack that overwhelms a device with connection requests to deny availability.
Reference:
This is a fundamental topic in network security, covered in the Security Concepts domain of the SCOR 350-701 exam.
Cisco Security Documentation on DoS Attacks: Describes various flood attacks, including SYN floods, as common methods to exhaust connection state tables on servers, firewalls, and other network devices.
In summary, an attack characterized by a target device being overwhelmed with initial connection requests from multiple sources is a SYN flood attack.
Which license is required for Cisco Security Intelligence to work on the Cisco Next Generation Intrusion Prevention System?
A. control
B. malware
C. URL filtering
D. protect
Explanation:
Cisco's Firepower licensing is modular, and the "Protect" license is the one that specifically enables the Intrusion Prevention System (IPS) and Next-Generation IPS (NGIPS) capabilities.
Let's break down the license types:
D) Protect is CORRECT.
The Protect license is required to enable the core IPS/NGIPS functionality. This includes:
Intrusion Prevention System (IPS) signature updates and engine.
Network-based application visibility and control (AVC).
File and malware inspection.
The underlying Security Intelligence (SI) feeds, which include IP, URL, and domain reputation data, are a foundational part of this license. SI acts as a first line of defense, quickly blocking connections to known malicious IPs and URLs before more resource-intensive inspection like IPS occurs.
Why the other options are incorrect:
A) Control is INCORRECT.
The Control license is focused on identity-based policies and integration with Cisco TrustSec for security group tagging (SGT) and enforcement. It is not required for the basic IPS and Security Intelligence to function.
B) Malware is INCORRECT.
While the Malware license is often bundled, it specifically enables advanced file analysis and sandboxing with Advanced Malware Protection (AMP). The basic file and malware inspection that is part of NGIPS is included in the Protect license. The "Malware" license typically refers to the more advanced retrospective analysis and threat intelligence from Talos.
C) URL Filtering is INCORRECT.
The URL Filtering license provides access to Cisco's full, categorized URL database (like "Gambling," "Social Media") to create policies based on website categories. The Security Intelligence component included with the Protect license only blocks URLs/domains that are on a known-malicious threat list, not general web categorization and filtering.
Reference:
Cisco Firepower Management Center Configuration Guide, "Licensing":
The official documentation clearly maps features to license types. It states that the "Protect" license is required for Intrusion Policies, File Policies, and Security Intelligence (which includes IP, URL, and Domain block lists).
Cisco Firepower Data Sheets:
Product data sheets for the FTD and NGIPS consistently list Intrusion Prevention and Security Intelligence as core features enabled by the Protect license.
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise?
A. Cisco Cloudlock
B. Cisco Umbrella
C. Cisco AMP
D. Cisco App Dynamics
Explanation for Each Option:
A. Cisco Cloudlock (Correct):
Cisco Cloudlock is a cloud-native, API-based Cloud Access Security Broker (CASB) designed to protect cloud environments by reducing compromises, application risks, and data breaches. It integrates with cloud applications via APIs to provide visibility, data security, and threat protection in non-on-premises environments like SaaS, IaaS, and PaaS, making it the ideal solution for this scenario. (Reference: Cisco Cloudlock Datasheet, API Integration.)
B. Cisco Umbrella (Incorrect):
Cisco Umbrella is a cloud-delivered security platform that provides DNS-layer protection, blocking malicious domains and phishing attempts. While effective for securing internet traffic, it is not primarily an API-based broker focused on reducing application risks and data breaches in non-on-premises cloud environments, making it less suitable for this specific use case. (Reference: Cisco Umbrella Overview.)
C. Cisco AMP (Incorrect):
Cisco Advanced Malware Protection (AMP) is a threat-focused solution that detects, prevents, and responds to malware across endpoints, networks, and cloud environments. Although it enhances security, it is not an API-based broker tailored for managing cloud application risks and data breaches in non-on-premises settings, focusing more on malware-specific threats. (Reference: Cisco AMP Datasheet.)
D. Cisco App Dynamics (Incorrect):
Cisco App Dynamics is an application performance monitoring (APM) tool that helps optimize application performance and troubleshoot issues in cloud and on-premises environments. It is not designed as an API-based broker to reduce compromises, application risks, or data breaches, as its primary focus is performance rather than security brokering. (Reference: Cisco App Dynamics User Guide.)
Additional Notes:
Cisco Cloudlock, relevant to the 350-701 SCOR exam under cloud security, is tailored for non-on-premises environments. As of 09:08 AM PKT, October 02, 2025, it remains a key CASB solution. For details, refer to the Cisco Cloudlock documentation (cisco.com) and the 350-701 Exam Blueprint (Section 3.0 Security Concepts).
What is a characteristic of traffic storm control behavior?
A.
Traffic storm control drops all broadcast and multicast traffic if the combined traffic
exceeds the level within the interval.
B.
Traffic storm control cannot determine if the packet is unicast or broadcast
C.
Traffic storm control monitors incoming traffic levels over a 10-second traffic storm
control interval.
D.
Traffic storm control uses the Individual/Group bit in the packet source address to
determine if the packet is unicast or broadcast
Traffic storm control drops all broadcast and multicast traffic if the combined traffic
exceeds the level within the interval.
An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network, what action will resolve this issue?
A. Configure security appliances to send syslogs to Cisco Stealthwatch Cloud
B. Configure security appliances to send NetFlow to Cisco Stealthwatch Cloud
C. Deploy a Cisco FTD sensor to send events to Cisco Stealthwatch Cloud
D. Deploy a Cisco Stealthwatch Cloud sensor on the network to send data to Cisco Stealthwatch Cloud
Explanation:
Cisco Stealthwatch Cloud has two primary deployment models for data collection:
Cloud-Native Integration:
For cloud environments (like AWS, Azure), it uses APIs and cloud-native flow logs. This is why "cloud logging is working as expected."
On-Premises Network:
For physical and private data centers, it requires an on-premises collector, officially called the Stealthwatch Cloud Sensor.
The sensor is a virtual machine deployed inside the private network. Its job is to:
Receive network flow data (NetFlow, IPFIX, sFlow) from routers, switches, and firewalls.
Perform initial analysis and compression.
Securely forward the relevant metadata and security events to the Stealthwatch Cloud console.
If logs are not being received from the on-premises network, the most likely cause is that this sensor is not deployed or is misconfigured.
Why the other options are incorrect:
A) Configure security appliances to send syslogs to Cisco Stealthwatch Cloud is INCORRECT.
Stealthwatch Cloud is primarily designed to analyze network flow data (NetFlow, IPFIX), not syslog. While it can integrate with other systems, its core threat detection for the network is based on flow analysis. Furthermore, the Stealthwatch Cloud console does not have a public endpoint for syslog ingestion from on-premises; all data flows through the sensor.
B) Configure security appliances to send NetFlow to Cisco Stealthwatch Cloud is INCORRECT.
You cannot configure your on-premises devices to send NetFlow directly to the Stealthwatch Cloud public IP address. The network flow data must be sent to the private IP address of the Stealthwatch Cloud Sensor, which then forwards it.
C) Deploy a Cisco FTD sensor to send events to Cisco Stealthwatch Cloud is INCORRECT.
While Cisco FTD can be a source of NetFlow data (by sending it to the Stealthwatch Cloud Sensor), the "FTD sensor" is not the correct component. The specific component required is the Stealthwatch Cloud Sensor VM.
Reference:
Cisco Stealthwatch Cloud Deployment Guide: The official documentation explicitly states that for on-premises networks, you must "Deploy the Stealthwatch Cloud sensor virtual machine" and then "Configure your network infrastructure to send NetFlow to the sensor."
Which attack is preventable by Cisco ESA but not by the Cisco WSA?
A. buffer overflow
B. DoS
C. SQL injection
D. phishing
Explanation:
The key to this question is recognizing the primary delivery method for each attack and which appliance is the gateway for that method.
D) phishing is CORRECT.
Phishing attacks are predominantly launched via email. The attacker sends a fraudulent email designed to trick the recipient into revealing sensitive information. The Cisco ESA is the first line of defense for email-borne threats and is specifically designed to detect and block phishing emails using techniques like sender reputation, anti-spam engines, and anti-phishing filters. The Cisco WSA, which filters web traffic, would only be involved if a user clicks a link within a phishing email, but it cannot prevent the phishing email itself from arriving in the user's inbox. Therefore, the initial phishing email is preventable by ESA but not by WSA.
Why the other options are incorrect:
A) buffer overflow is INCORRECT.
A buffer overflow is a software exploit that can be delivered via multiple vectors, including both malicious email attachments (filtered by ESA) and drive-by downloads from malicious websites (filtered by WSA). Both appliances can play a role in preventing its delivery.
B) DoS is INCORRECT.
A Denial-of-Service (DoS) attack aims to overwhelm a service with traffic. Both appliances can be involved in mitigating DoS attacks relevant to their protocols. The ESA can mitigate email-based DoS (mail bombing), and the WSA can help mitigate HTTP/HTTPS-based DoS attacks
C) SQL injection is INCORRECT.
SQL injection is an attack against web applications. It is typically launched through a web browser. The Cisco WSA, especially when integrated with a Web Application Firewall (WAF) like Cisco Secure Firewall Management Center, can detect and block SQL injection attempts in web traffic. The ESA would not see this attack as it does not involve the email protocol.
Summary of Responsibilities:
Cisco ESA: Protects against threats delivered via email (spam, phishing, malware in attachments).
Cisco WSA: Protects against threats delivered via web browsing (malicious sites, drive-by downloads, web application attacks).
Reference:
Cisco ESA vs. WSA Solution Overviews: The data sheets for each product clearly delineate their primary use cases, with ESA focusing on the email vector and WSA focusing on the web vector. Phishing is consistently listed as a top threat mitigated by the ESA.
What are two functions of secret key cryptography? (Choose two)
A.
key selection without integer factorization
B.
utilization of different keys for encryption and decryption
C.
utilization of large prime number iterations
D.
provides the capability to only know the key on one side
E.
utilization of less memory
utilization of different keys for encryption and decryption
provides the capability to only know the key on one side
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
A. biometric factor
B. time factor
C. confidentiality factor
D. knowledge factor
E. encryption factor
Explanation for Each Option:
A. biometric factor (Correct):
The biometric factor, such as fingerprints, facial recognition, or iris scans, is a widely used authentication factor in multifactor authentication (MFA). It relies on unique physical characteristics, providing a strong, something-you-are component, making it one of the most common factors. (Reference: Cisco Identity Services Engine MFA Guide, Biometrics.)
B. time factor (Incorrect):
The time factor, often associated with time-based one-time passwords (TOTP) like those from authenticator apps, is a method within the possession factor (something-you-have), not a distinct authentication factor. It supports MFA but is not considered a primary factor type, rendering this option incorrect. (Reference: Cisco Secure Access TOTP Configuration.)
C. confidentiality factor (Incorrect):
"Confidentiality factor" is not a recognized authentication factor in MFA. Confidentiality relates to data protection, not user authentication, and is unrelated to the standard factors (something-you-know, -have, -are), making this option invalid. (Reference: NIST Digital Identity Guidelines, Authentication Factors.)
D. knowledge factor (Correct):
The knowledge factor, such as passwords or PINs, is one of the most commonly used authentication factors in MFA. It represents something-you-know, providing a foundational element that is often combined with other factors, making it a standard and widely adopted choice. (Reference: Cisco ISE Knowledge-Based Authentication.)
E. encryption factor (Incorrect):
"Encryption factor" is not an authentication factor in MFA. Encryption is a security mechanism used to protect data, not to verify identity, and does not align with the recognized categories (knowledge, possession, biometric), rendering this option incorrect. (Reference: Cisco Secure Encryption Overview.)
Additional Notes:
Understanding MFA factors is a key topic in the 350-701 SCOR exam under endpoint security. As of 12:15 PM PKT, October 03, 2025, knowledge and biometric factors are prevalent.
Due to a traffic storm on the network, two interfaces were error-disabled, and both
interfaces sent SNMP traps.
Which two actions must be taken to ensure that interfaces are put back into service?
(Choose two)
A. Have Cisco Prime Infrastructure issue an SNMP set command to re-enable the ports after the pre configured interval.
B. Use EEM to have the ports return to service automatically in less than 300 seconds
C. Enter the shutdown and no shutdown commands on the interfaces
D. Enable the snmp-server enable traps command and wait 300 seconds
E. Ensure that interfaces are configured with the error-disable detection and recovery feature
Explanation for Each Option:
A. Have Cisco Prime Infrastructure issue an SNMP set command to re-enable the ports after the preconfigured interval (Incorrect):
While Cisco Prime Infrastructure can manage devices via SNMP, issuing an SNMP set command to re-enable ports requires specific configuration and manual intervention. It is not a standard or automated method for recovering error-disabled interfaces, and it depends on external tools, making it less practical than built-in recovery mechanisms. (Reference: Cisco Prime Infrastructure User Guide, SNMP Management.)
B. Use EEM to have the ports return to service automatically in less than 300 seconds (Incorrect):
Embedded Event Manager (EEM) can automate actions based on events, such as re-enabling ports after a timer. However, this requires custom scripting and configuration, which is not a default or guaranteed method for error-disable recovery. It is an advanced option, not a standard action, making it incorrect as a primary solution. (Reference: Cisco IOS EEM Configuration Guide.)
C. Enter the shutdown and no shutdown commands on the interfaces (Correct):
Manually issuing the shutdown and no shutdown commands on the affected interfaces is a direct and widely accepted method to recover from an error-disabled state. This clears the error condition and reactivates the ports, ensuring they return to service after the traffic storm issue is resolved, making it a standard action. (Reference: Cisco IOS Interface Command Reference, Error Disable Recovery.)
D. Enable the snmp-server enable traps command and wait 300 seconds (Incorrect):
The snmp-server enable traps command enables SNMP notifications (e.g., for error-disabled states), but it does not automatically re-enable ports. Waiting 300 seconds assumes a recovery timer, which requires additional error-disable recovery configuration. This alone does not restore service, making it insufficient without further setup. (Reference: Cisco IOS SNMP Configuration Guide.)
E. Ensure that interfaces are configured with the error-disable detection and recovery feature (Correct):
Configuring the error-disable detection and recovery feature (e.g., errdisable recovery cause all and setting a timer like errdisable recovery interval) allows interfaces to automatically recover from error-disabled states, such as those caused by a traffic storm. This proactive setup ensures ports return to service without manual intervention, meeting the requirement. (Reference: Cisco IOS LAN Switching Configuration Guide, Error Disable Recovery.)
Additional Notes:
Error-disable recovery is a key topic in the 350-701 SCOR exam under network security. As of 05:15 PM PKT, October 01, 2025, this remains a standard practice for managing interface errors. For details, refer to the Cisco IOS Interface and Switching Configuration Guides (cisco.com) and the 350-701 Exam Blueprint (Section 1.0 Security Concepts).
| Page 13 out of 61 Pages |
| Previous |