Topic 2: Exam Pool B
A switch with Dynamic ARP Inspection enabled has received a spoofed ARP response on
a trusted interface.
How does the switch behave in this situation?
A.
It forwards the packet after validation by using the MAC Binding Table.
B.
It drops the packet after validation by using the IP & MAC Binding Table
C.
It forwards the packet without validation
D.
It drops the packet without validation
It forwards the packet without validation
What are two DDoS attack categories? (Choose two)
A.
sequential
B.
protocol
C.
database
D.
volume-based
E.
screen-based
protocol
volume-based
There are three basic categories of attack:+
volume-based attacks, which use high traffic to inundate the network bandwidth+ protocol attacks, which focus on exploiting server resources+ application attacks, which focus on
web applications and are considered the most sophisticated and serious type of attacks
Reference: https://www.esecurityplanet.com/networks/types-of-ddos-attacks/
An administrator is configuring a DHCP server to better secure their environment. They
need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped.
How would this be accomplished?
A.
Set a trusted interface for the DHCP server
B.
Set the DHCP snooping bit to 1
C.
Add entries in the DHCP snooping database
D.
Enable ARP inspection for the required VLAN
Set a trusted interface for the DHCP server
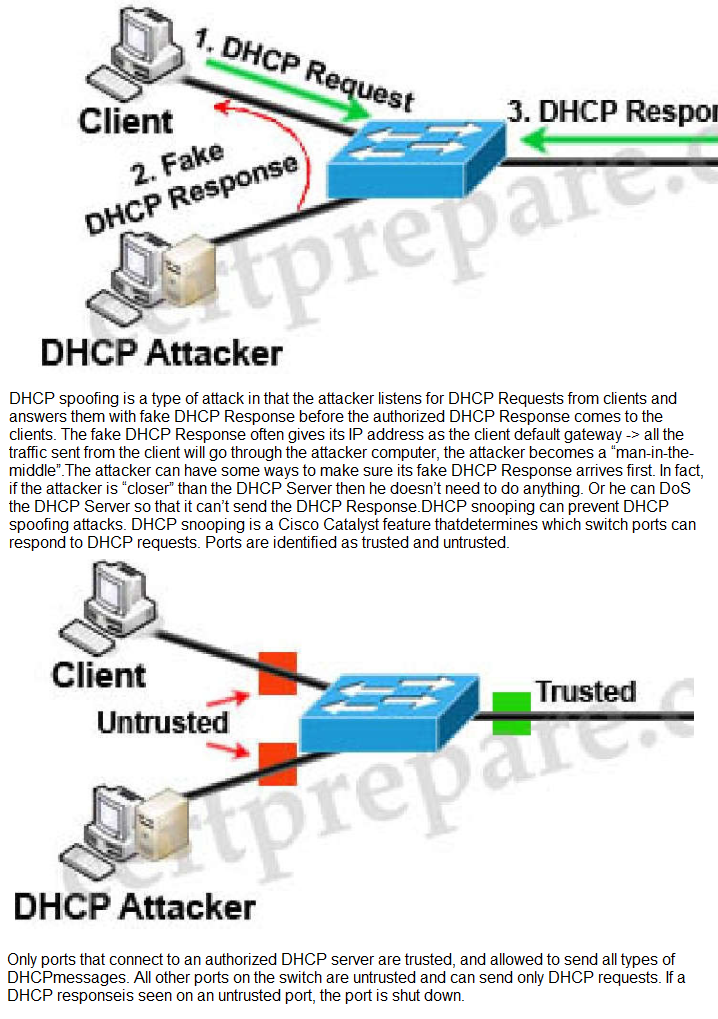
To understand DHCP snooping we need to learn about DHCP
spoofing attack first.
In which cloud services model is the tenant responsible for virtual machine OS patching?
A. IaaS
B. UCaaS
C. PaaS
D. SaaS
Explanation
This question tests the understanding of the shared responsibility model in cloud computing. The key is knowing which layers of the stack are managed by the cloud provider and which are managed by the tenant (customer).
IaaS (Infrastructure as a Service):
In this model, the cloud provider is responsible for the core infrastructure: the physical data center, network, storage, and servers. The tenant is responsible for everything on top of that, including the operating system, runtime, data, and applications. Therefore, patching the guest operating system of a virtual machine is the tenant's responsibility.
Why the other options are incorrect:
B. UCaaS (Unified Communications as a Service):
This is a specific type of SaaS for communication tools (e.g., Webex). The provider manages the entire application and its underlying platform and infrastructure. The tenant has no responsibility for OS patching.
C. PaaS (Platform as a Service):
In this model, the cloud provider manages the underlying infrastructure (servers, storage, network) and the operating system, middleware, and runtime environment. The tenant is only responsible for their application and data. The tenant does not have access to or responsibility for the OS.
D. SaaS (Software as a Service):
In this model, the cloud provider manages the entire application stack, from the infrastructure all the way up to the application itself. The tenant is only responsible for their use of the application and their data. The tenant has zero responsibility for any OS patching.
Reference:
The shared responsibility model is a fundamental concept for cloud security.
A common analogy used in Cisco and other cloud training is:
IaaS: The cloud provider is the landlord; you are responsible for everything inside your rented unit (the VM), including maintenance (patching).
PaaS: The cloud provider manages the building and utilities; you are only responsible for your business operations inside (the application).
SaaS: You are just a customer using a service; the provider manages everything.
In which two ways does Easy Connect help control network access when used with Cisco TrustSec? (Choose two)
A. It allows multiple security products to share information and work together to enhance security posture in the network.
B. It creates a dashboard in Cisco ISE that provides full visibility of all connected endpoints.
C. It allows for the assignment of Security Group Tags and does not require 802.1x to be configured on the switch or the endpoint.
D. It integrates with third-party products to provide better visibility throughout the network.
E. It allows for managed endpoints that authenticate to AD to be mapped to Security Groups (PassiveID).
Explanation:
Easy Connect is a specific deployment model for Cisco TrustSec designed to simplify the implementation of micro-segmentation without the complexity of a full 802.1X rollout. It achieves this by leveraging alternative methods to assign Security Group Tags (SGTs).
Let's break down why C and E are correct and the others are not:
C) It allows for the assignment of Security Group Tags and does not require 802.1x to be configured on the switch or the endpoint.
This is CORRECT. This is the core value proposition of Easy Connect. Instead of relying solely on 802.1X authentication (which can be complex to deploy on all switches and endpoints), Easy Connect uses other methods like Device Registration (via the My Devices portal) or Web Authentication to classify an endpoint and assign it an SGT. The switchport is configured with a static SGT, which is applied to all traffic from a connected device.
E) It allows for managed endpoints that authenticate to AD to be mapped to Security Groups (PassiveID).
This is CORRECT. Passive Identity (PassiveID) is a key component of Easy Connect. ISE can integrate with Active Directory (AD) by monitoring authentication traffic (e.g., from a Domain Controller). When a managed corporate laptop authenticates to AD, ISE learns the user's identity and IP address. It can then map that IP address to a specific Security Group, allowing for dynamic policy enforcement based on user identity without requiring 802.1X on the network access layer.
Why the other options are incorrect:
A) It allows multiple security products to share information and work together to enhance security posture in the network.
This is INCORRECT. While this is a general benefit of a security platform architecture (like pxGrid), it is not the specific purpose or defining feature of Easy Connect. This describes ecosystem integration, not the simplified access control method that Easy Connect provides.
B) It creates a dashboard in Cisco ISE that provides full visibility of all connected endpoints.
This is INCORRECT. Cisco ISE does have dashboards for endpoint visibility (via Profiling), but this is not a feature unique to or created by "Easy Connect." Easy Connect is a deployment methodology that uses existing ISE profiling and context services.
D) It integrates with third-party products to provide better visibility throughout the network.
This is INCORRECT. Similar to option A, this describes the function of pxGrid, which is a separate, though complementary, technology within the ISE ecosystem. Easy Connect itself is focused on simplifying the initial SGT assignment for access control.
Reference:
Cisco TrustSec Solution Design Guide:
Documentation on Easy Connect explicitly states its purpose is to "enable SGT assignment without 802.1X" using methods like "Central Web Auth, Native Supplicant Profile, and Device Registration."
Cisco ISE Administrator Guide on Passive Identity:
The documentation for PassiveID describes how it "leverages existing authentication systems (like AD) to identify users and their devices without deploying 802.1X," which is a cornerstone of the Easy Connect model.
Refer to the exhibit.
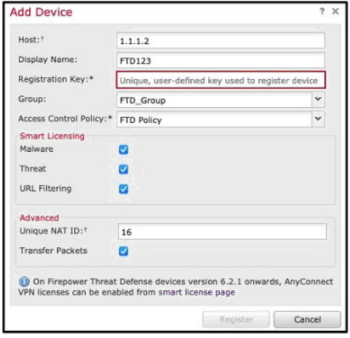
An administrator is adding a new Cisco FTD device to their network and wants to manage it
with Cisco FMC.
The Cisco FTD is not behind a NAT device. Which command is needed to enable this on
the Cisco FTD?
A.
configure manager add DONTRESOLVE kregistration key>
B.
configure manager add <FMC IP address> <registration key> 16
C.
configure manager add DONTRESOLVE <registration key> FTD123
D.
configure manager add <FMC IP address> <registration key>
configure manager add <FMC IP address> <registration key>
Which two deployment model configurations are supported for Cisco FTDv in AWS?
(Choose two)
A.
Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
B.
Cisco FTDv with one management interface and two traffic interfaces configured
C.
Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
D.
Cisco FTDv with two management interfaces and one traffic interface configured
E.
Cisco FTDv configured in routed mode and IPv6 configured
Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
What are the two types of managed Intercloud Fabric deployment models? (Choose two)
A. Service Provider managed
B. Public managed
C. Hybrid managed
D. User managed
E. Enterprise managed
Explanation for Each Option:
A. Public managed (Incorrect):
"Public managed" is not a recognized deployment model for Cisco Intercloud Fabric. The Intercloud Fabric focuses on hybrid cloud connectivity, with specific managed models tied to service providers or enterprises, not a generic public category, making this option incorrect. (Reference: Cisco Intercloud Fabric Overview.)
B. Service Provider managed (Correct):
In the Service Provider managed model, a third-party service provider manages the Intercloud Fabric infrastructure, including connectivity and orchestration between private and public clouds. This is a standard deployment option, making it a correct choice. (Reference: Cisco Intercloud Fabric Deployment Guide, Service Provider Model.)
C. Enterprise managed (Correct):
In the Enterprise managed model, the organization itself manages the Intercloud Fabric deployment, maintaining control over the infrastructure and connectivity across its private and public cloud environments. This is another standard model, making it a correct choice. (Reference: Cisco Intercloud Fabric Deployment Guide, Enterprise Model.)
D. User managed (Incorrect):
"User managed" is not a defined deployment model for Intercloud Fabric. Management is categorized by the entity (service provider or enterprise), not the end user, rendering this option incorrect. (Reference: Cisco Intercloud Fabric Management Options.)
E. Hybrid managed (Incorrect):
While Intercloud Fabric supports hybrid cloud environments, "Hybrid managed" is not a specific deployment model. The management is either service provider or enterprise-led, not a distinct hybrid management category, making this option incorrect. (Reference: Cisco Intercloud Fabric Hybrid Cloud Support.)
Additional Notes:
Understanding Intercloud Fabric deployment models is a key topic in the 350-701 SCOR exam under cloud security. As of 1:05 PM PKT, October 03, 2025, these models support hybrid connectivity.
What is a benefit of using Cisco FMC over Cisco ASDM?
A. Cisco FMC uses Java while Cisco ASDM uses HTML5.
B. Cisco FMC provides centralized management while Cisco ASDM does not.
C. Cisco FMC supports pushing configurations to devices while Cisco ASDM does not.
D. Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA devices
Explanation
This question tests the fundamental architectural difference between the two management tools.
Cisco FMC (Firepower Management Center):
This is a centralized management system. A single FMC appliance or virtual server can manage dozens or even hundreds of Cisco Firepower Threat Defense (FTD) devices (such as Firepower 2100 series, FTD on ASA 5500-X, etc.). You configure policies once and deploy them to many devices from a single pane of glass.
Cisco ASDM (Adaptive Security Device Manager):
This is a device-level management tool. It is used to manage a single Cisco ASA (Adaptive Security Appliance) firewall at a time. You connect ASDM directly to the IP address of one specific ASA to configure it.
Therefore, the primary and most significant benefit of FMC over ASDM is its ability to centrally manage a fleet of firewalls.
Why the other options are incorrect:
A. Cisco FMC uses Java while Cisco ASDM uses HTML5. This is factually incorrect.
The opposite is true. Historically, ASDM was a Java Web Start application, which caused many operational issues. Modern ASDM versions can use a standalone launcher or a web interface. Cisco FMC is a web-based (HTML5) application and does not require Java.
C. Cisco FMC supports pushing configurations to devices while Cisco ASDM does not.
This is incorrect. Both management tools push configurations to the devices they manage. ASDM pushes configurations to the single ASA it is connected to, while FMC pushes configurations to the multiple FTD devices under its control.
D. Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA devices.This is misleading and incorrect.
Cisco FMC does not manage traditional ASA firewalls running the legacy ASA software. FMC only manages firewalls running the Firepower Threat Defense (FTD) operating system. ASDM manages ASA firewalls running the legacy ASA software. They manage different product lines and operating systems.
Reference
This distinction is a core concept in the Cisco Security Certifications, particularly when comparing the older ASA platform to the newer Firepower/FTD platform.
Cisco FMC Data Sheet: Typically states it "simplifies security management with centralized, unified policies across the entire portfolio of Firepower NGFWs and NGIPSs."
Cisco ASDM Data Sheet: Describes it as "a powerful, per-device management tool."
The key differentiator is Centralized (FMC) vs. Per-Device (ASDM) Management.
What is a capability of Cisco ASA Netflow?
A. It filters NSEL events based on traffic
B. It generates NSEL events even if the MPF is not configured
C. It logs all event types only to the same collector
D. It sends NetFlow data records from active and standby ASAs in an active standby failover pair
Explanation
Cisco ASA NetFlow is more specifically known as NetFlow Secure Event Logging (NSEL). Unlike traditional NetFlow which samples traffic, NSEL is event-based and logs stateful firewall connection events.
A key capability is the ability to be selective about which traffic generates these NSEL events. This is configured using a Modular Policy Framework (MPF) service policy.
How it works:
You create a class-map to define the traffic you are interested in (e.g., traffic from a specific subnet, going to a specific port). You then apply a service-policy that includes the flow-export event-type command for that specific class of traffic.
Result:
This allows you to filter NSEL events so that only the traffic matching your policy class is sent to the NetFlow collector. This reduces the volume of data and focuses reporting on the most important traffic, which is the capability described in option A
Detailed Breakdown of Incorrect Options
B. It generates NSEL events even if the MPF is not configured
Why it is incorrect:
This is the opposite of the truth. The MPF (Modular Policy Framework) must be configured to enable and direct NSEL/NetFlow on an ASA. Without a service-policy that includes the flow-export command, the ASA will not generate or send any NSEL events to a collector. The configuration is not automatic.
C. It logs all event types only to the same collector
Why it is incorrect:
This is an absolute statement that is false. While a basic configuration might send all events to a single collector, the ASA is capable of more granular control. You can configure multiple flow-export destinations and use different MPF policies to send specific types of events (e.g., flow-create events) to one collector and other events (e.g., flow-teardown events) to another.
D. It sends NetFlow data records from active and standby ASAs in an active standby failover pair
Why it is incorrect:
In an active/standby failover pair, only the active unit processes traffic and generates NSEL events. The standby unit does not process traffic and therefore does not generate its own flow data. Sending duplicate records from both units would create inaccurate data on the collector. The failover link synchronizes configuration and state information, but it does not synchronize or forward NetFlow data from the standby unit.
Reference and Key Context
Cisco ASA Series NetFlow Configuration Guide:
This documentation explicitly details that NSEL is configured using the Modular Policy Framework and that you can use class-map to select the traffic for which you want to generate events.
NSEL Event Types:
NSEL is triggered by specific stateful firewall events like flow creation (flow-create), flow teardown (flow-teardown), and flow denial (flow-denied). The ability to filter which traffic generates these events is a fundamental capability.
Key Takeaway:
The power of ASA NetFlow (NSEL) is its integration with the ASA's powerful MPF, which allows an administrator to be very precise about which traffic flows are exported to the collector. This filtering capability is a direct and important feature.
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
Explanation for Each Option:
A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX (Incorrect):
The crypto isakmp key command is specific to IKEv1 (Internet Key Exchange version 1) on Cisco IOS devices, not IKEv2. While IKEv2 uses a similar pre-shared key mechanism, this command syntax is tied to IKEv1 configuration. Thus, it does not authenticate IKEv2 peers, making this option incorrect. (Reference: Cisco IOS Security Configuration Guide, IKEv1 vs. IKEv2.)
B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX (Incorrect):
The command specifies address 172.16.0.0 without a mask, which defaults to a /32 (single IP) in some contexts, but when followed by a subnet (implied /16 from 172.16.0.0 range), it applies to the 172.16.0.0/16 network. It authenticates a range of peers, not just 172.16.0.0/32, making this option inaccurate. (Reference: Cisco IOS IPsec Configuration Guide, ISAKMP Key Syntax.)
C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX (Correct):
The crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command configures a pre-shared key (ciscXXXXXXXX) for IKEv1 Phase 1 authentication. The IP address 172.16.0.0 without a mask implies a /16 range (172.16.0.0 - 172.16.255.255), authenticating all peers in this subnet, aligning with standard IKEv1 behavior on Cisco routers. (Reference: Cisco IOS ISAKMP Configuration Guide, Pre-Shared Keys.)
D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX (Incorrect):
This command configures a pre-shared key for IKEv1 authentication, not certificate-based security. Certificate-based authentication uses crypto ca commands and relies on digital certificates, not pre-shared keys. The key here authenticates peers, not certificates, making this option a misinterpretation of the command’s purpose. (Reference: Cisco IOS PKI Configuration Guide, Certificate Authentication.)
Additional Notes:
The crypto isakmp key command is a key topic in the 350-701 SCOR exam under VPN technologies, configuring IKEv1 pre-shared keys. As of 09:12 AM PKT, October 02, 2025, this remains a standard configuration for site-to-site VPNs. For details, refer to the Cisco IOS Security Configuration Guide (cisco.com) and the 350-701 Exam Blueprint (Section 3.0 Security Concepts). More questions?
Note:
The key "ciscXXXXXXXX" appears to be a placeholder with truncated characters; I treated it as a valid pre-shared key for explanation purposes.
What is provided by the Secure Hash Algorithm in a VPN?
A. integrity
B. key exchange
C. encryption
D. authentication
Explanation:
The Secure Hash Algorithm (SHA) is a cryptographic hash function. In the context of a VPN, its primary role is to provide data integrity.
Let's break down how it works and why the other options are incorrect:
A) Integrity is CORRECT.
In an IPsec VPN, SHA (e.g., SHA-256, SHA-384) is used within the Hash-based Message Authentication Code (HMAC) function. For every packet sent through the VPN tunnel, the sender calculates a hash (a unique digital fingerprint) of the packet's contents. This hash is sent along with the packet. The receiver recalculates the hash upon receipt. If the hashes match, it proves the packet was not altered in transit. If even a single bit was changed, the hashes would be completely different, indicating a loss of integrity.
Why the other options are incorrect:
B) Key exchange is INCORRECT.
Key exchange is the process of securely establishing a shared secret key between two peers. This is the function of protocols like Diffie-Hellman (DH) or RSA, not the Secure Hash Algorithm.
C) Encryption is INCORRECT.
Encryption is the process of scrambling data to make it unreadable to anyone without the key. This is the function of symmetric encryption algorithms like AES (Advanced Encryption Standard), 3DES, or ChaCha20. SHA does not perform encryption or decryption.
D) Authentication is INCORRECT.
This is a common point of confusion. While the HMAC function (which uses SHA) provides data origin authentication (proving the data came from the expected peer and wasn't modified), the primary function listed for the algorithm itself is integrity. Peer authentication (verifying the identity of the VPN peer) is typically handled by pre-shared keys (PSK) or digital certificates during the IKE negotiation phase.
Summary of IPsec VPN Cryptographic Roles:
Encryption: AES, 3DES
Integrity: SHA, MD5 (via HMAC)
Key Exchange: Diffie-Hellman (DH)
Peer Authentication:Pre-shared Keys (PSK) or Digital Certificates (RSA)
Reference:
IPsec Protocol Standard (RFC 4301): Defines the use of integrity algorithms (like those in the SHA family) for the Authentication Header (AH) and Encapsulating Security Payload (ESP) protocols to provide data integrity.
Crypto VPN Configuration Guides (IOS/ASA):When configuring an IPsec transform set, you select an encryption cipher (e.g., esp-aes) and an integrity (authentication) algorithm (e.g., esp-sha-hmac), clearly separating the two functions.
| Page 12 out of 61 Pages |
| Previous |