Which service is a VNF role?
A.
Compute
B.
Network
C.
Firewall
D.
Storage
Network
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttlsecurity
hops 2 command.
After you issue this command, which BGP packets does the PE accept?
A.
from 2.2.2.2, with a TTL ol 253 Of more
B.
from 2.2.2.2, with a TTL of less than 2
C.
to 2.2.2.2, with a TTL of less than 253
D.
to 2.2.2.2, with a TTL of 2 or more
from 2.2.2.2, with a TTL ol 253 Of more
Refer to the exhibit.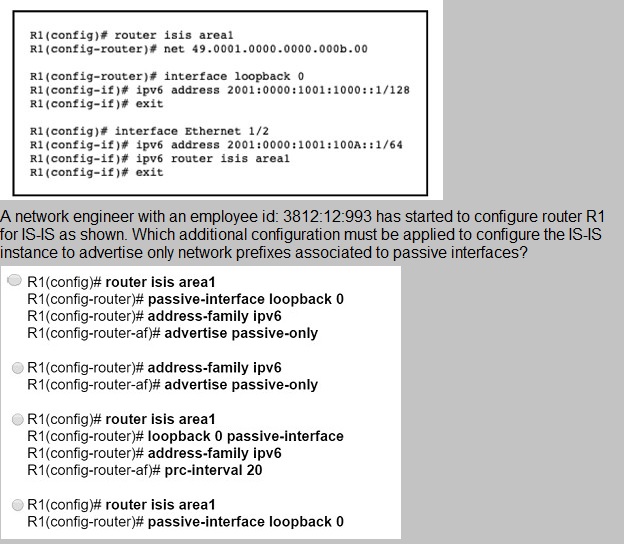
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
Refer to the exhibit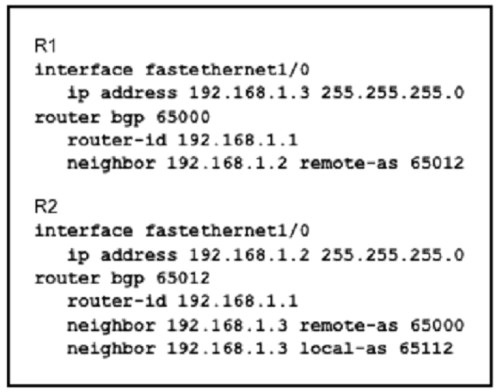
Assume all other configurations are correct and the network is otherwise operating
normally. Which conclusion can you draw about the neighbor relationship between routers
R1 and R2?
A.
The neighbor relationship will be up only if the two devices have activated the correct
neighbor relationships under the IPv4 address family
B.
The neighbor relationship is down because R1 believes R2 is in AS 65012.
C.
The neighbor relationship is up
D.
The neighbor relationship is down because the loco I-as value for R2 is missing in the
R1 neighbor statement
The neighbor relationship is down because R1 believes R2 is in AS 65012.
Refer to the exhibit: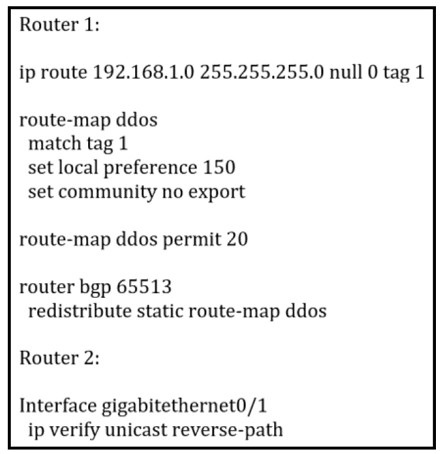
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
A.
Router 2 must configure a route to null 0 for network 192 168.1 0/24 for the RTBH
implementation to be complete.
B.
Router 1 is the trigger router in a RTBH implementation.
C.
Router 1 must be configured with uRPF for the RTBH implementation to be effective.
D.
Router 2 is the router receiving the DDoS attack
Router 2 must configure a route to null 0 for network 192 168.1 0/24 for the RTBH
implementation to be complete.
Refer to the exhibit.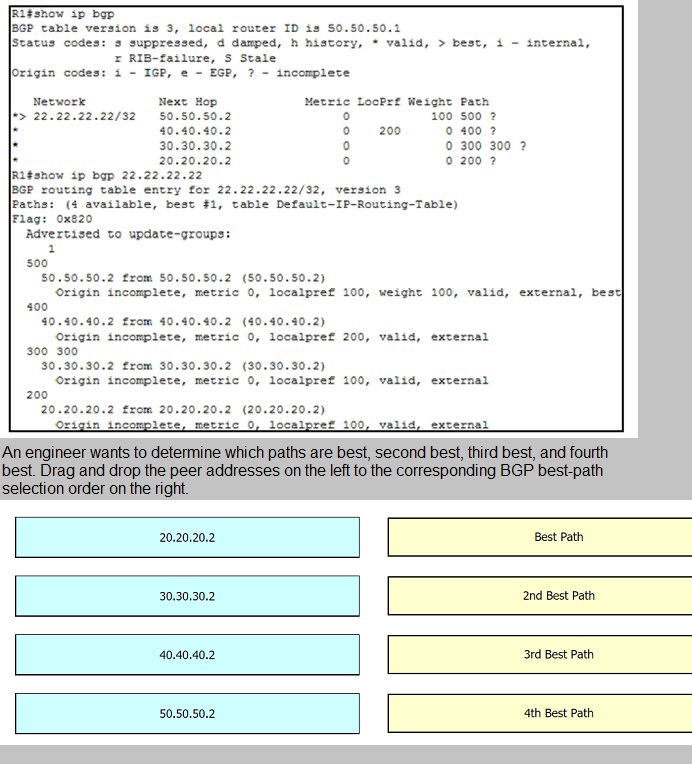

Refer to the exhibit: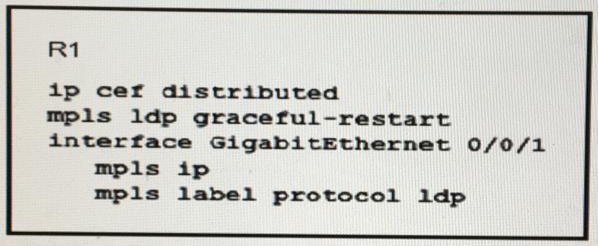
Which effect of this configuration is true?
A.
R1 can support a peer that is configured for LDP SSO/NSF as the peer recovers from
an outage
B.
R1 can failover only to a peer that is configured for LDP SSO/NSF
C.
R1 can failover to any peer
D.
R1 can support a graceful restart operation on the peer, even if graceful restart is
disabled on the peer
R1 can failover only to a peer that is configured for LDP SSO/NSF
Why do packet loops occur during the configuration of BlDlR-PIM?
A.
The network does not support BIDIR-PIM
B.
The network is partially upgraded to support BIDlR-PIM
C.
No interface for carrying traffic for multicast groups has been configured
D.
The router has not been configured to advertise itself
The network is partially upgraded to support BIDlR-PIM
What causes multicast traffic to permanently stay on the shared tree and not switch to the
source tree?
A.
The SPT threshold is set to infinity.
B.
The RP IP address is configured incorrectly.
C.
The RP announcements are being filtered.
D.
SSM range is being used.
The RP announcements are being filtered.
What is a role of NSO?
A.
It automates the deployment of access points with its built-in wireless LAN controller.
B.
It manages WAN infrastructure using a virtual switch.
C.
It provides full lifecycle management of a device.
D.
It resides on a hypervisor that runs the Windows OS.
It provides full lifecycle management of a device.
Which statement about TLS is accurate when using RESTCONF to write configurations on
network devices'?
A.
It requires certificates for authentication.
B.
It is provided using NGINX acting as a proxy web server
C.
It is used for HTTP and HTTPS requests.
D.
It is not supported on Cisco devices
It requires certificates for authentication.
Refer to the exhibit.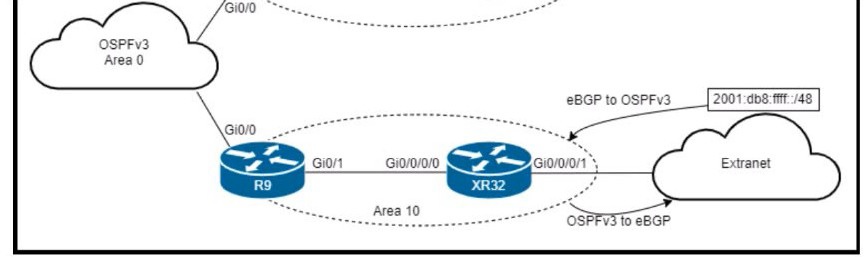
An engineer is updating this network to meet these conditions:
• Area 10 will receive inter-area routes and support mutual redistribution of external routes
with the extranet.
• The ::/0 route is prohibited in Area 10.
• Area 11 will receive only the ::/0 route from the ABR.
• External route redistribution is not supported in Area 11.
• The ABR in Area 11 will advertise no interarea routes.
Which two configurations must be performed to meet the requirements? (Choose two.)
A.
Configure area 11 as nssa no-summary on R7 and as nssa on XR31.
B.
Configure area 10 as stub on R9 and XR32.
C.
Configure area 11 as stub no-summary on R7 and as stub on XR31.
D.
Configure area 11 as nssa default-information-originate on R7 and as nssa on XR31.
E.
Configure area 10 as nssa on R9 and XR
Configure area 11 as stub no-summary on R7 and as stub on XR31.
Configure area 11 as nssa default-information-originate on R7 and as nssa on XR31.
| Page 9 out of 31 Pages |
| Previous |