Topic 1: Exam Pool A
A response code of 404 is received while using the REST API on Cisco UNA Center to
POST to this URI.
/dna/intent/api/v1 /template-programmer/project
What does the code mean?
A. The client made a request a resource that does not exist.
B. The server has not implemented the functionality that is needed to fulfill the request.
C. The request accepted for processing, but the processing was not completed.
D. The POST/PUT request was fulfilled and a new resource was created, Information about the resource is in the response body.
What is one characteristic of an AP that is operating in Mobility Express mode?
A. It is recommended for large scale deployments.
B. It requires a centralized WLC.
C. At least three APs are needed for WLC redundancy.
D. It requires an AP to act as a WLC.
A customer requests a design that includes GLBP as the FHRP. The network architect discovers that the members of the GLBP group have different throughput capabilities. Which GLBP load balancing method supports this environment?
A. host dependent
B. weighted
C. least connection
D. round robin
What are two methods of ensuring that the multicast RPF check passes without changing the unicast routing table? (Choose two.)
A. disabling the interface of the router back to the multicast source
B. implementing MBGP
C. disabling BGP routing protocol
D. implementing static mroutes
E. implementing OSPF routing protocol
Refer to the exhibit.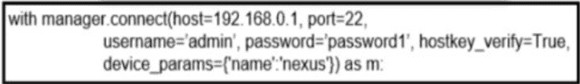
What does the snippet of code achieve?
A. It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls.
B. It opens a tunnel and encapsulates the login information, if the host key is correct.
C. It opens an ncclient connection to a Cisco Nexus device and maintains it for the duration of the context.
D. It creates an SSH connection using the SSH key that is stored, and the password is ignored.
When deploying Cisco SD-Access Fabric APs, where does the data plane VXLAN tunnel terminate?
A. on the first-hop fabric edge switch
B. on the WLC node
C. on the fabric border node switch
D. directly on the fabric APs
What is a benefit of MACsec in a multilayered LAN network design?
A. There is no requirement to run IEEE 802.1X when MACsec is enabled on a switch port.
B. Layer 2 trunk links between switches can be secured.
C. Application flows between hosts on the LAN to remote destinations can be encrypted.
D. Layer 3 links between switches can be secured.
When deploying a Cisco Unified Wireless solution what is a design justification for using a distributed WLC deployment model?
A. It reduces the number of WLCs that network administrators must support by locating them in a common location
B. It more evenly distributes MAC ARP and ND processing over multiple switches which helps with scalability
C. The number of wireless clients is low and the size of the physical campus is small
D. There are no latency concerns about LWAPP and CAPWAP tunnels traversing the campus core network
Which deployment option of Cisco NGFW provides scalability?
A. tap
B. inline tap
C. high availability
D. clustering
Which tag defines the roaming domain and properties of an AP deployment?
A. RF tag
B. policy tag
C. site tag
D. AP tag
Which controller is the single plane of management for Cisco SD-WAN?
A. vBond
B. vEdge
C. vSmart
D. vManage
An engineer must configure a new 6 Ghz only SSID on a cisco catalyst 9800 series WLC,
with these requirements:
Provide 802.11ax data rates for supported devices
All users authenticate using a certificate
Which wireless layer 2 security mode meets the requirements?
A. WPA2 Enterprise
B. WPA3 Personal
C. WPA2 Personal
D. WPA3 Enterprise
| Page 8 out of 30 Pages |
| Previous |