Topic 1: Exam Pool A
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are
recorded as follows:
A. The signal strength at location B is 10 dB better than location C.
B. The signal strength at location C is too weak to support web surfing
C. Location D has the strongest RF signal strength.
D. The RF signal strength at location B is 50% weaker than location A.
E. The RF signal strength at location C is 10 times stronger than location B

A. action 4.0 syslog command "show process cpu sorted | append flash:high-cpu-file"
B. action 4.0 cli command "show process cpu sorted | append flash:high-cpu-file"
C. action 4.0 ens-event "show process cpu sorted | append flash:high-cpu-file"
D. action 4.0 publish-event "show process cpu sorted | append flash:high-cpu-file"
Which RF value represents the decline of the RF signal amplitude over a given distance"?
A. signal-to-noise ratio
B. received signal strength indicator
C. free space path loss
D. effective isotropic radiated power
What is one characteristic of Cisco SD-Access networks?
A. Devices are assigned to virtual networks based on their VLAN membership.
B. Scalable group tags are used for macrosegmentatlon.
C. Virtual networks are used for microsegmentation.
D. All traffic is Layer 3 within the fabric
How can an engineer prevent basic replay attacks from people who try to brute force a system via REST API?
A. Add a timestamp to the request in the API header.
B. Use a password hash.
C. Add OAuth to the request in the API header.
D. Use HTTPS.
What is a characteristic of a Type 2 hypervisor?
A. quick deployment
B. ideal for data center
C. complicated deployment
D. referred to as bare-metal
Which language defines the structure or modelling of data for NETCONF and RESTCONF?
A. JSON
B. YANG
C. XML
D. YAML
What is the recommended minimum SNR for data applications on wireless networks?
A. 15
B. 20
C. 25
D. 10
What is used to validate the authenticity of the client and is sent in HTTP requests as a JSON object?
A. SSH
B. TLS
C. HTTPS
D. JWT
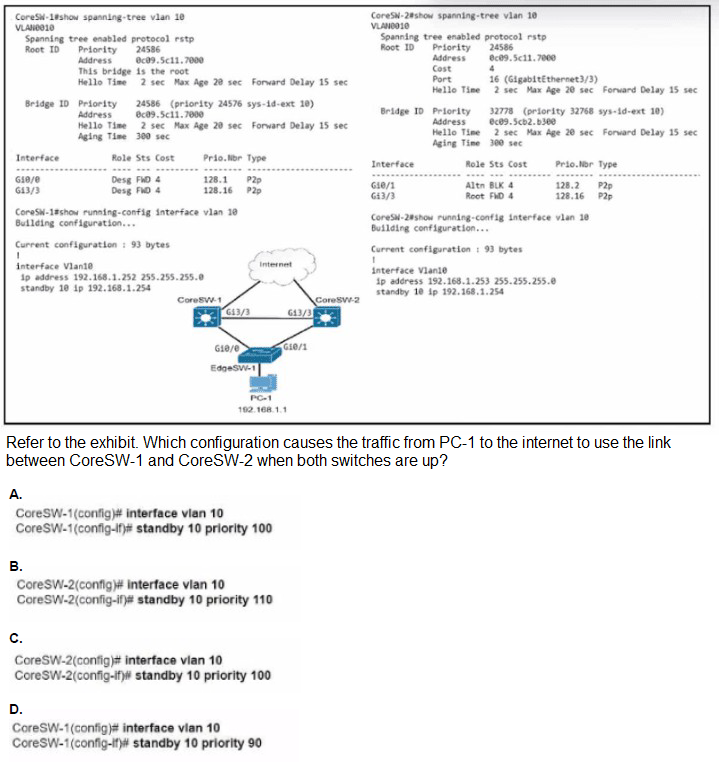
A. Option A
B. Option B
C. Option C
D. Option D
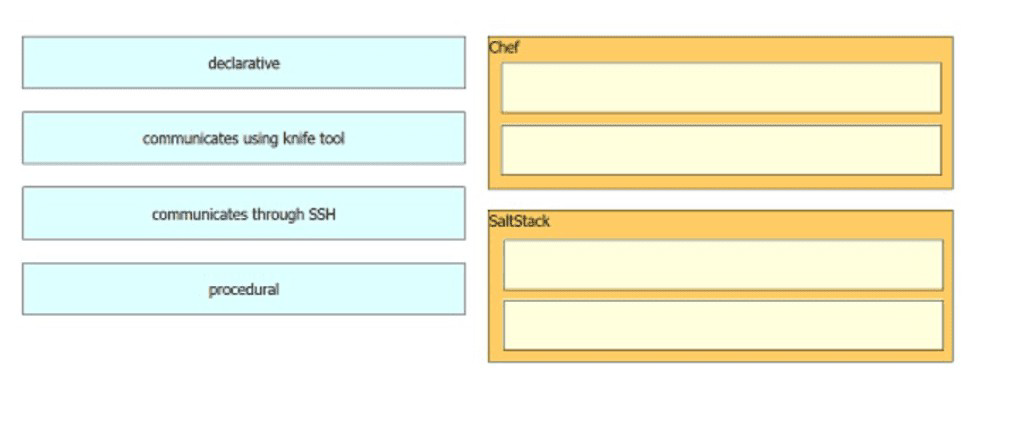
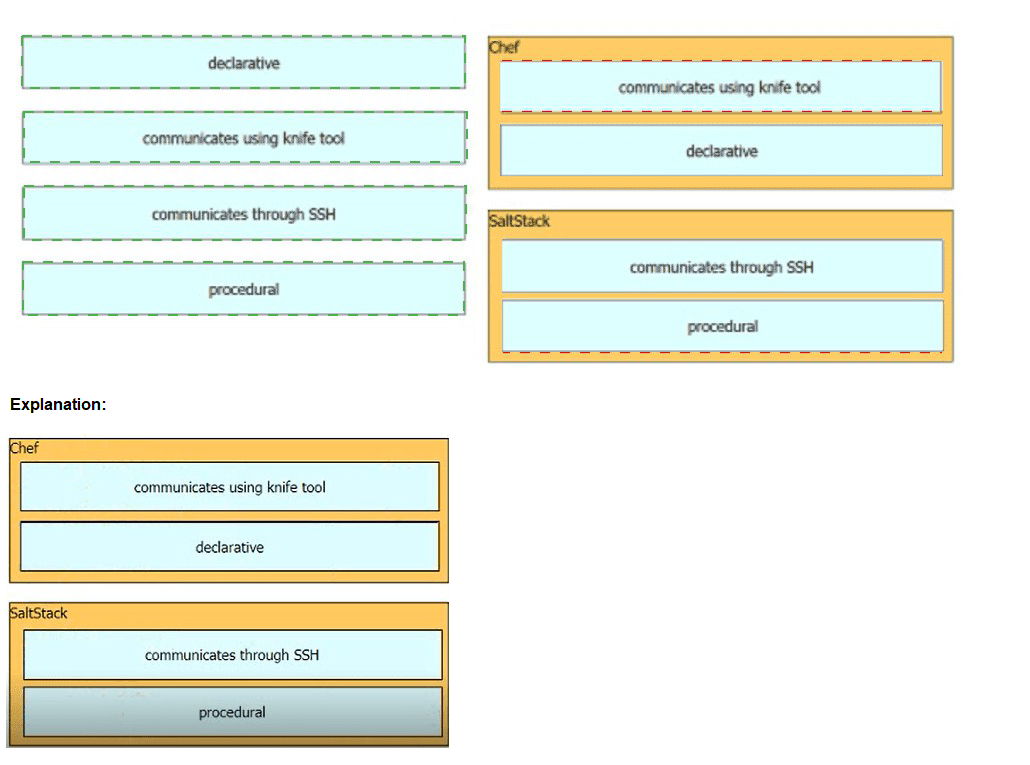
Drag and drop the characteristics from the left into the orchestration tools that they describe on the right.
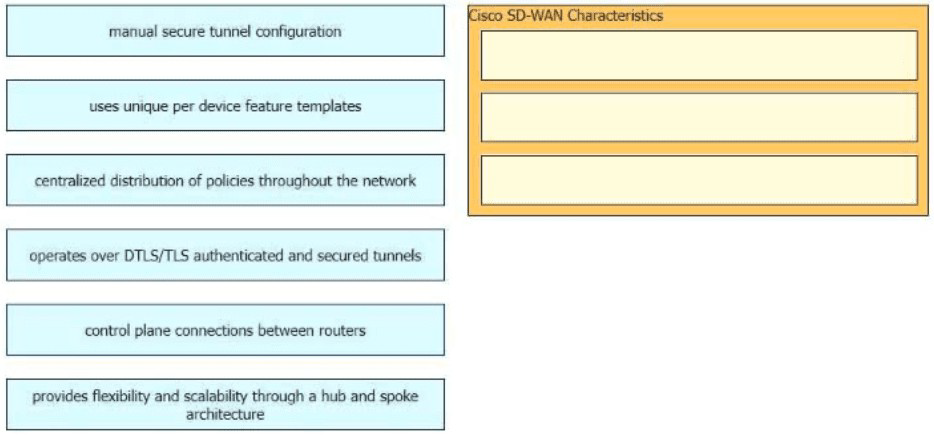
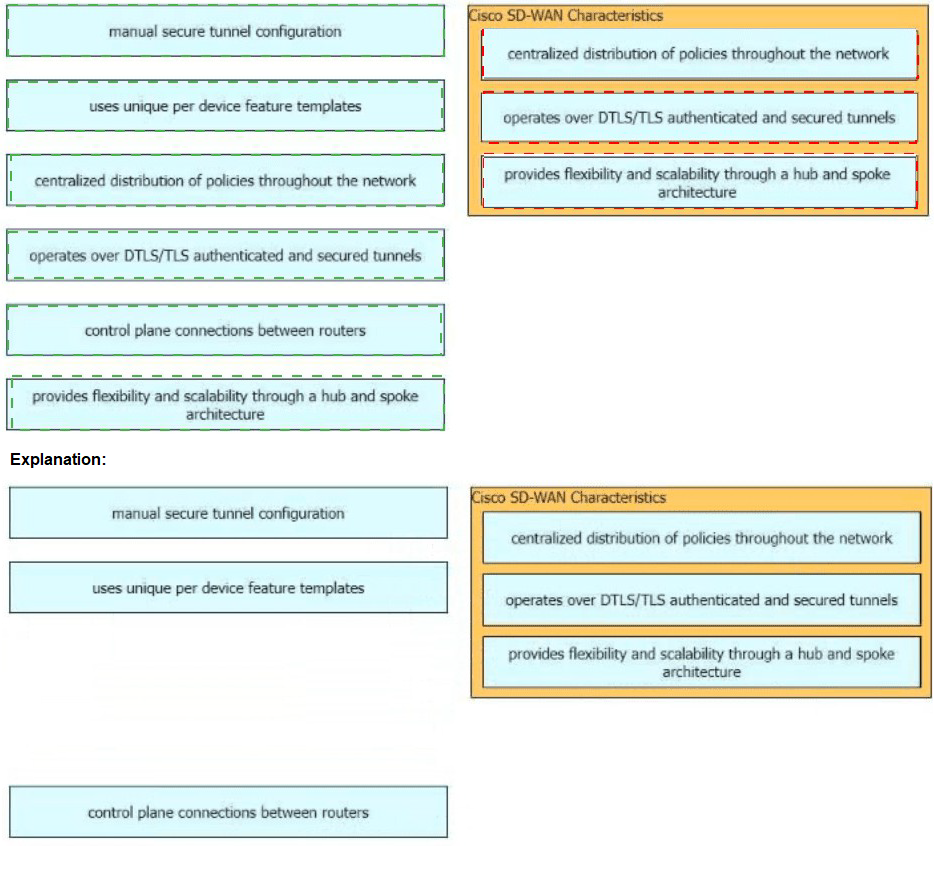
Drag and drop the characteristics of Cisco Catalyst SD-WAN from the left onto the right. Not all options are used.
| Page 7 out of 30 Pages |
| Previous |