Topic 1: Exam Pool A
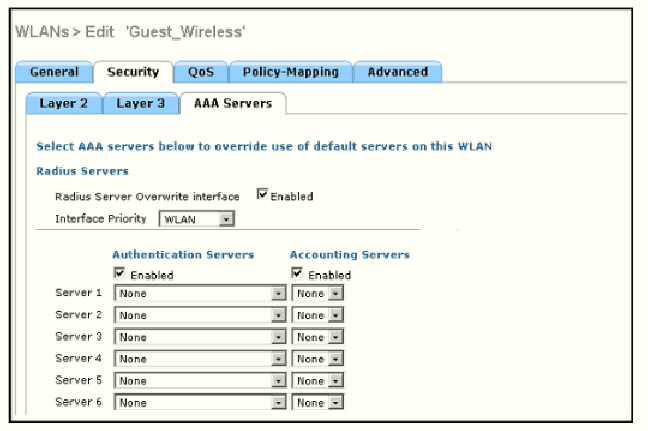
A. the interface specified on the WLAN configuration
B. any interface configured on the WLC
C. the controller management interface
D. the controller virtual interface
Refer to the exhibit.
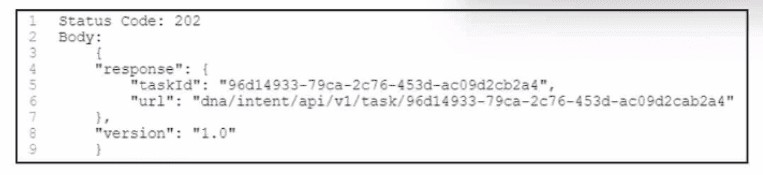
A. POST /auth/token
B. GET /network-device
C. GET /template-programmer/template/version/42a3df73-3ef4-49e2-b4f0-6927bbd4bf52
D. POST /discovery
An engineer is reviewing a PCAP file that contains a packet capture of a four-way handshake exchange between a client and AP using WPA2 Enterprise. Which EAPOL message validates and confirms that the client device has successfully Installed the GTK?
A. M2-Message
B. M1-Message
C. M3-Message
D. M4-Message
Which device makes the decision for a wireless client to roam?
A. wireless client
B. Wireless LAN controller
C. access point
D. WCS location server
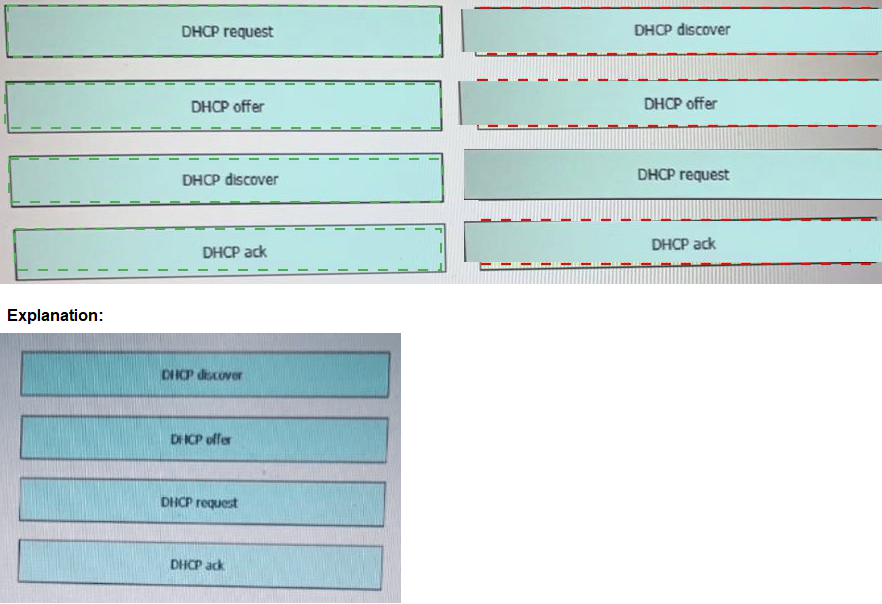
Drag and drop the DHCP messages that are exchanged between a client and an AP into the order they are exchanged on the right.

Which characteristics applies to Cisco SD-Access?
A. It uses dynamic routing to discover and provision the border and edge switches
B. It uses VXLAN for the control plane
C. It uses PnP to discover and provision border and access switches
D. It uses GRE tor me policy plane
In a Cisco SD-WAN solution, which two functions are performed by OMP? (Choose two.)
A. advertisement of network prefixes and their attributes
B. configuration of control and data policies
C. gathering of underlay infrastructure data
D. delivery of crypto keys
E. segmentation and differentiation of traffic
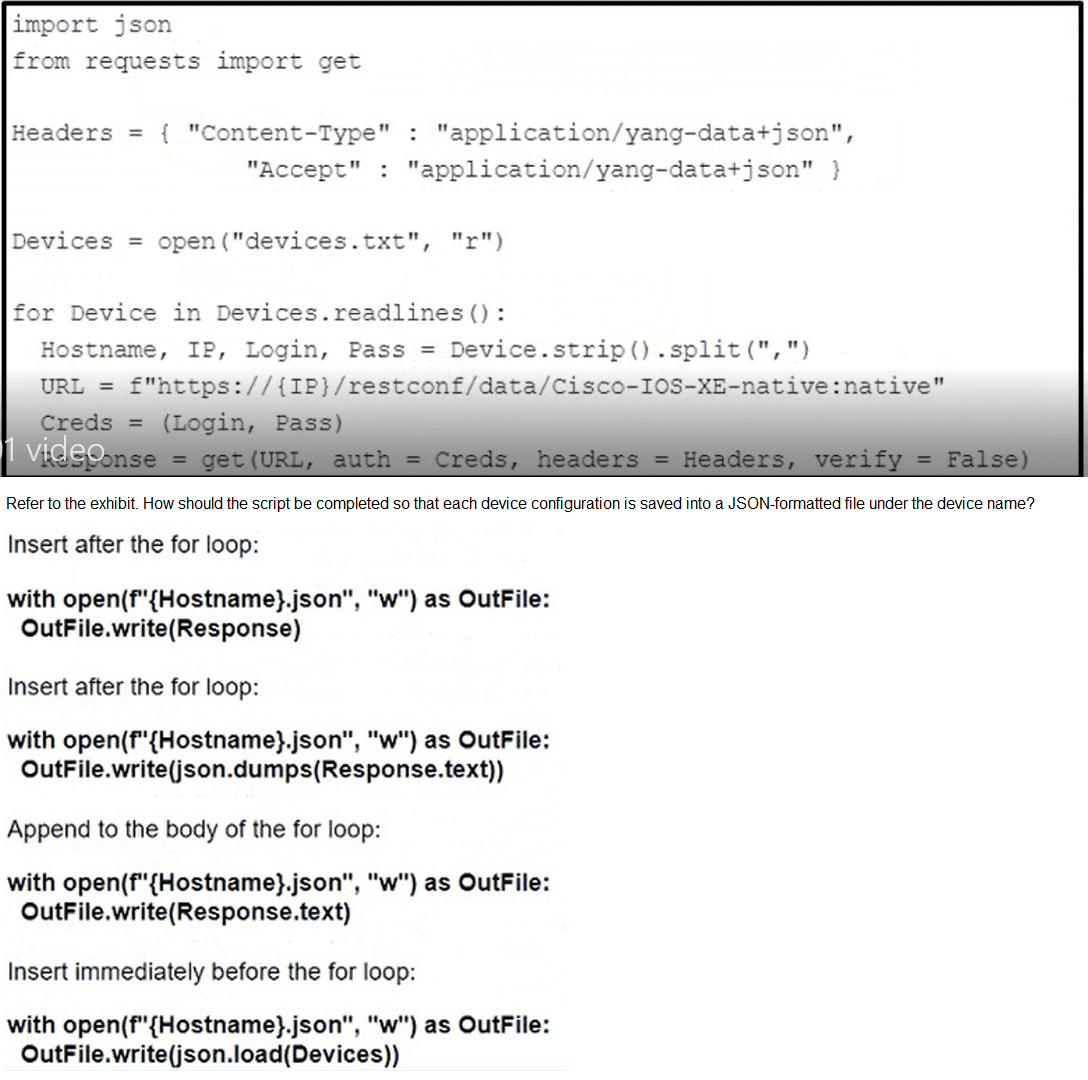
A. Option A
B. Option B
C. Option C
D. Option D
What is a client who is using 802.1x for authentication referred to as?
A. authenticator
B. policy enforcement point
C. NAC device
D. supplicant
Which two components are needed when a Cisco SD-Access fabric is designed? (Choose two.)
A. Cisco Catalyst Center (formerly DNA Center) application
B. Firepower Threat Defense
C. Identity Service Engine
D. Cisco Data Center Network Manager
E. Cisco Prime Infrastructure
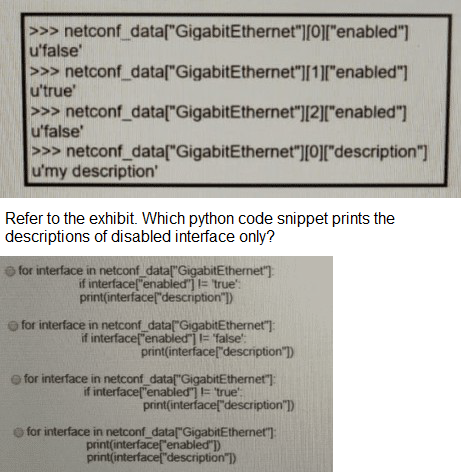
A. Option A
B. Option B
C. Option C
D. Option D
Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
A. Cisco Firepower and FireSIGHT
B. Cisco Stealth watch system
C. Advanced Malware Protection
D. Cisco Web Security Appliance
| Page 6 out of 30 Pages |
| Previous |