Topic 1: Exam Pool A
Refer to the exibit.
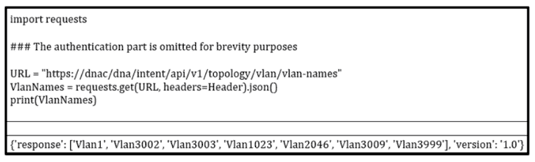
A. VlanNames(0)
B. VlanName[Vlan1']
C. VlanName['response']
D. list(VlanNames)
Which method does FastLocate use to collect location-based information?
A. RFID
B. client probing
C. beacons
D. data packets
An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation.
B. Use Cisco AMP deployment with the Malicious Activity Protection engine enabled.
C. Use Cisco AMP deployment with the Exploit Prevention engine enabled.
D. Use Cisco Firepower and block traffic to TOR networks.
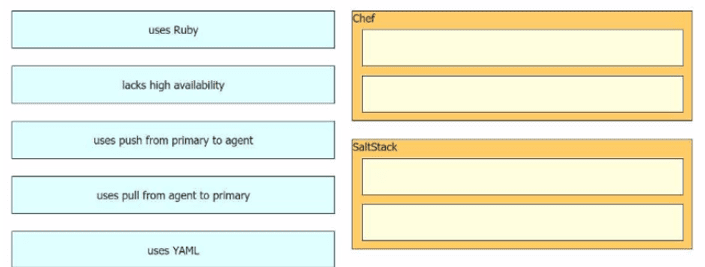
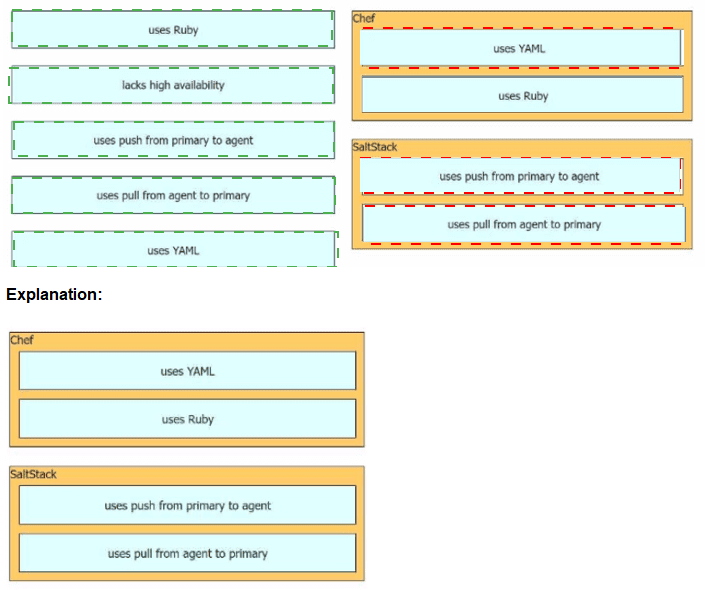
Drag and drop the automation characteristics from the left onto the appropriate tools on the right. Not all options are used.
What is used to measure the total output energy of a Wi-Fi device?
A. dBi
B. EIRP
C. mW
D. dBm
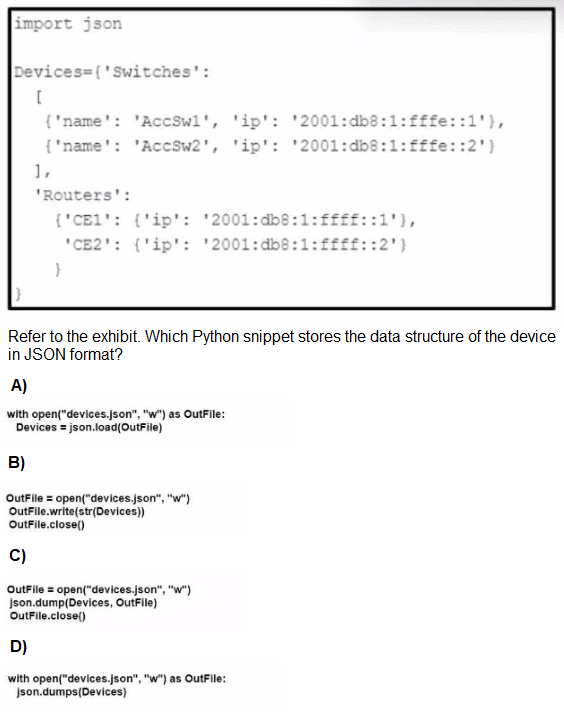
A. Option A
B. Option B
C. Option C
D. Option D
How is Layer 3 roaming accomplished in a unified wireless deployment?
A. An EoIP tunnel is created between the client and the anchor controller to provide seamless connectively as the client is associated with the new AP.
B. The client entry on the original controller is passed to the database on the new controller.
C. The new controller assign an IP address from the new subnet to the client.
D. The client database on the original controller is updated with the anchor entry, and the new controller database is updated with the foreign entry.
Whichtwo benefits result from a network design mat uses small and repeatable sections? (Choose two.)
A. lower monitoring requirements
B. low latency
C. scalability
D. quick failure isolation
E. improved throughput
Which method ensures the confidentiality of data exchanged over a REST API?
A. Use TLS to secure the underlying HTTP session.
B. Use me POST method Instead or URL-encoded GET to pass parameters.
C. Deploy digest-based authentication to protect the access to the API.
D. Encode sensitive data using Base64 encoding.
Which AP mode allows administrators to generate pcap files to use for troubleshooting?
A. Sniffer
B. Local
C. H-REAP
D. Monitor
Which DNS record type is needed to allow a Cisco AP to discover a WLC when using IPv4?
A. CNAME record
B. A record
C. NS record
D. SOA record
Refer to the exhibit.

A. [1,2.1.2.1,2]
B. [1,2] * 3
C. [3,6]
D. [1,2]. [1.2]. [1,2]
| Page 5 out of 30 Pages |
| Previous |