Topic 1: Exam Pool A
What is the purpose of data modeling languages?
A. to describe a data schema convertible into any data encoding format
B. to specify algorithms necessary to decode binary-encoded protocol data units
C. to translate encoded data for interoperability between different CPU architectures
D. to provide a framework to describe data flow patterns in networks
What is used by vManage to interact withCiscoSD-WAN devices in the fabric?
A. northbound API
B. RESTCONF
C. Southbound API
D. IPsec
Which device is responsible for finding EID-to-RLOC mappings when traffic is sent to a LISP-capable site?
A. ingress tunnel router
B. map resolver
C. egress tunnel router
D. map server
Drag and drop the code snippets from the bottom onto the blanks in the script to convert a Python object into a JSON string. Not all options are used
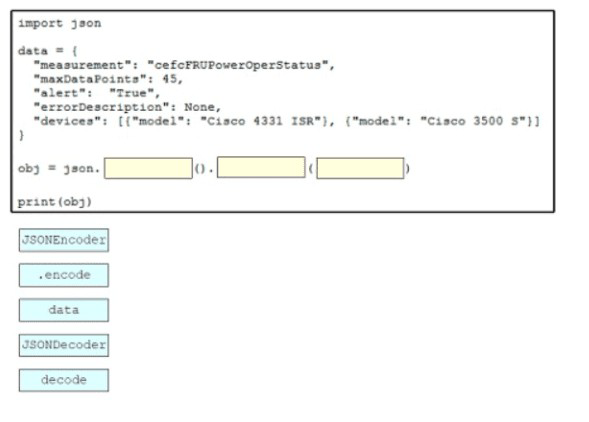
Which two functions is an edge node responsible for? (Choose two.)
A. provides multiple entry and exit points for fabric traffic
B. provides the default exit point for fabric traffic
C. provides the default entry point for fabric traffic
D. provides a host database that maps endpoint IDs to a current location
E. authenticates endpoints
What is the structure of a JSON web token?
A. header and payload
B. three parts separated by dots: version, header, and signature
C. payload and signature
D. three parts separated by dots: header, payload. and signature
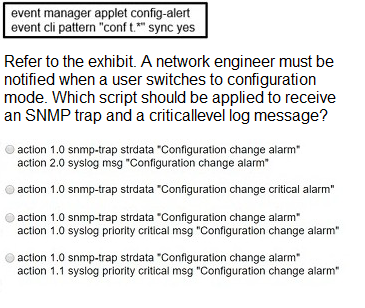
A. Option A
B. Option B
C. Option C
D. Option D
Which technology is the Cisco SD-Access control plane based on?
A. IS-IS
B. LISP
C. Cisco TrustSec
D. VXLAN
Which two operations are valid for RESTCONF? (Choose two)
A. PULL
B. ADD
C. HEAD
D. REMOVE
E. GET
F. PUSH
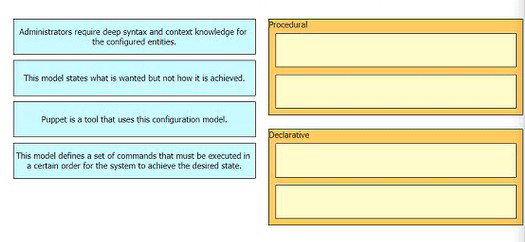
Drag anti drop the characteristics from the ten onto the configuration models on the right.

Which AP mode analyzes the spectrum to detect sources of interference?
A. Monitor
B. Rogue detector
C. SE-Connect
D. Sniffer
With IGMPv2, which multicast group address does the IGMP querier use to send query messages to all hosts on the LAN?
A. 239.0.0.2
B. 224.0.0.1
C. 239.0.0.1
D. 224.0.0.2
| Page 3 out of 30 Pages |
| Previous |