Topic 2, Exam Pool B
Before performing a logical or physical search of a drive in Encase, what must be added to the program?
A.
File signatures
B.
Keywords
C.
Hash sets
D.
Bookmarks
Keywords
Depending upon the jurisdictional areas, different laws apply to different incidents. Which of the following law is related to fraud and related activity in connection with computers?
A.
18 USC §1029
B.
18 USC §1030
C.
18 USC §1361
D.
18 USC §1371
18 USC §1030
While searching through a computer under investigation, you discover numerous files that appear to have had the first letter of the file name replaced by the hex code byte 5h. What does this indicate on the computer?
A.
The files have been marked as hidden
B.
The files have been marked for deletion
C.
The files are corrupt and cannot be recovered
D.
The files have been marked as read-only
The files have been marked for deletion
Which rule requires an original recording to be provided to prove the content of a
recording?
A.
1004
B.
1002
C.
1003
D.
1005
1002
Which of the following is a list of recently used programs or opened files?
A.
Most Recently Used (MRU)
B.
Recently Used Programs (RUP)
C.
Master File Table (MFT)
D.
GUID Partition Table (GPT)
Most Recently Used (MRU)
When a user deletes a file or folder, the system stores complete path including the original
filename is a special hidden file called “INFO2” in the Recycled folder. If the INFO2 file is
deleted, it is recovered when you ______________________.
A.
Undo the last action performed on the system
B.
Reboot Windows
C.
Use a recovery tool to undelete the file
D.
Download the file from Microsoft website
Undo the last action performed on the system
When a user deletes a file or folder, the system stores complete path including the original filename is a special hidden file called “INFO2” in the Recycled folder. If the INFO2 file is deleted, it is recovered when you ______________________.
A.
Undo the last action performed on the system
B.
Reboot Windows
C.
Use a recovery tool to undelete the file
D.
Download the file from Microsoft website
Undo the last action performed on the system
What feature of Windows is the following command trying to utilize? 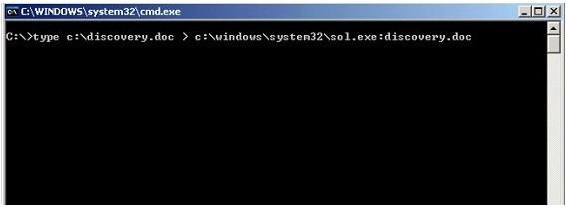
A.
White space
B.
AFS
C.
ADS
D.
Slack file
ADS
Sniffers that place NICs in promiscuous mode work at what layer of the OSI model?
A.
Network
B.
Transport
C.
Physical
D.
Data Link
Physical
If you are concerned about a high level of compression but not concerned about any possible data loss, what type of compression would you use?
A.
Lossful compression
B.
Lossy compression
C.
Lossless compression
D.
Time-loss compression
Lossy compression
Adam, a forensic investigator, is investigating an attack on Microsoft Exchange Server of a
large organization. As the first step of the investigation, he examined the PRIV.EDB file and
found the source from where the mail originated and the name of the file that disappeared
upon execution. Now, he wants to examine the MIME stream content. Which of the
following files is he going to examine?
A.
PRIV.STM
B.
gwcheck.db
C.
PRIV.EDB
D.
PUB.EDB
PRIV.STM
Which of the following tool can the investigator use to analyze the network to detect Trojan
activities?
A.
Regshot
B.
TRIPWIRE
C.
RAM Computer
D.
D. Capsa
D. Capsa
| Page 23 out of 50 Pages |
| Previous |