Which two border nodes are available in the Cisco SD-Access architecture? (Choose two.)
A.
extended border
B.
edge border
C.
internal border
D.
anywhere border
E.
intermediate border
internal border
anywhere border
Explanation: There are 3 types of border nodes in SD-Access:
External. Default exit from fabric with no specific routes injection
Internal. Gateway only for a set of networks, such as shared services prefixes
Anywhere. Combination of external and internal functionality
A network administrator is troubleshooting a DMVPN setup between the hub and the
spoke. Which action should the administrator take before troubleshooting the IPsec
configuration?
A.
Verify the GRE tunnels.
B.
Verify ISAKMP.
C.
Verify NHRP.
D.
Verify crypto maps.
Verify the GRE tunnels.
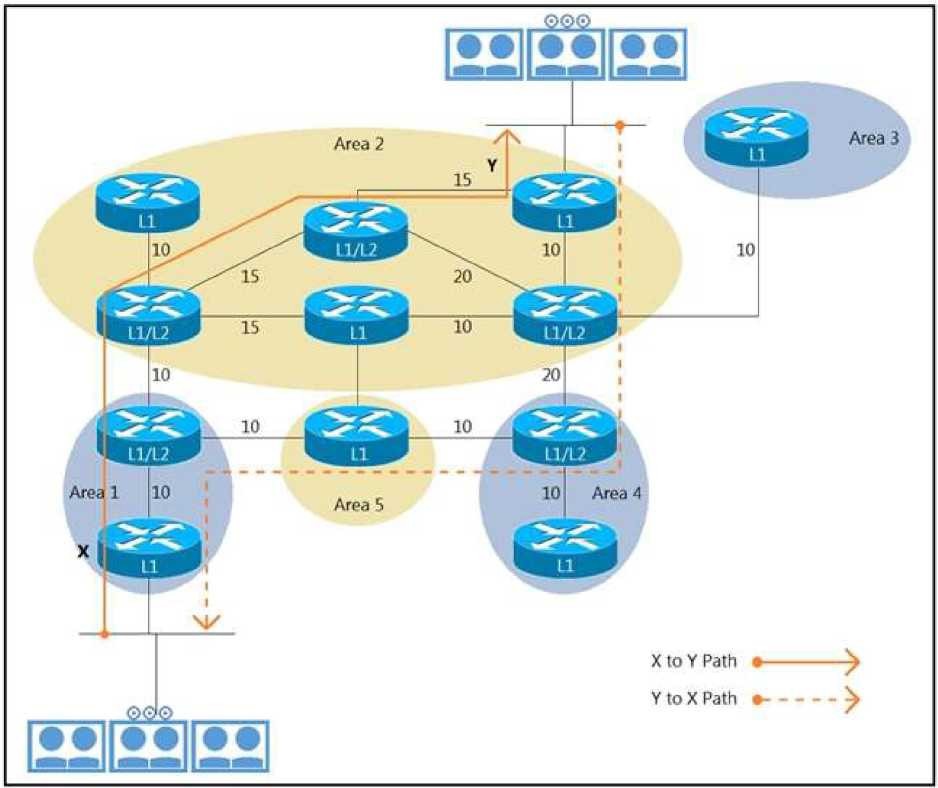
Refer to the exhibit. Customers report low video quality and delays when having point-topoint
telepresence video calls between the two locations. An architect must optimize a
design so that traffic follows the same path for egress and ingress traffic flows. Which
technique optimizes the design?
A.
Configure route leaking on the router in area 2.
B.
Configure route leaking on the router in area 1.
C.
Configure the high metric on the router in area 4.
D.
Configure route filter on the router in area 4.
Configure the high metric on the router in area 4.
How do endpoints inside an SD-Access network reach resources outside the fabric?
A.
a VRF fusion router is used to map resources in one VN to another VN
B.
Fabric borders use VRFs to map VNs to VRFs
C.
SD-Access transit links are used to transport encapsulated traffic from one fabric
to another
D.
A fabric edge is used to de-encapsulate VXLAN traffic to normal IP traffic then
Fabric borders use VRFs to map VNs to VRFs
Explanation: https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-sdadesign-
guide.html
"Packets and frames sourced from inside the fabric and destined outside of the fabric are
de-encapsulated by the border node"(not the edge node)
Which component of Cisco SD-Access integrates with Cisco DNA Center to perform policy
segmentation and enforcement through the use of security group access control lists and
security group tags?
A.
Cisco Application Policy Infrastructure Controller Enterprise Module
B.
Cisco Network Data Platform
C.
Cisco Identity Services Engine
D.
Cisco TrustSec
Cisco TrustSec
In the SD-WAN underlay network, which WAN Edge VPN ID is defined as the transport
VPN and is used to
carry control traffic?
A.
VPN 0
B.
VPN 512
C.
VPN 128
D.
VPN 256
VPN 0
Which consideration must be made when designing a Cisco SD-Access fabric underlay?
A.
Subnets must be reduced to decrease latency.
B.
Up to six control planes are supported.
C.
The default MTU should be increased.
D.
A unified policy must be used.
Up to six control planes are supported.
Which design consideration should be observed when EIGRP is configured on Data Center
switches?
A.
Perform manual summarization on all Layer 3 interfaces to minimize the size of the routing table.
B.
Prevent unnecessary EIGRP neighborships from forming across switch virtual
interfaces.
C.
Lower EIGRP hello and hold timers to their minimum settings to ensure rapid
route reconvergence.
D.
Configure multiple EIGRP autonomous systems to segment Data Center services
and applications.
Perform manual summarization on all Layer 3 interfaces to minimize the size of the routing table.
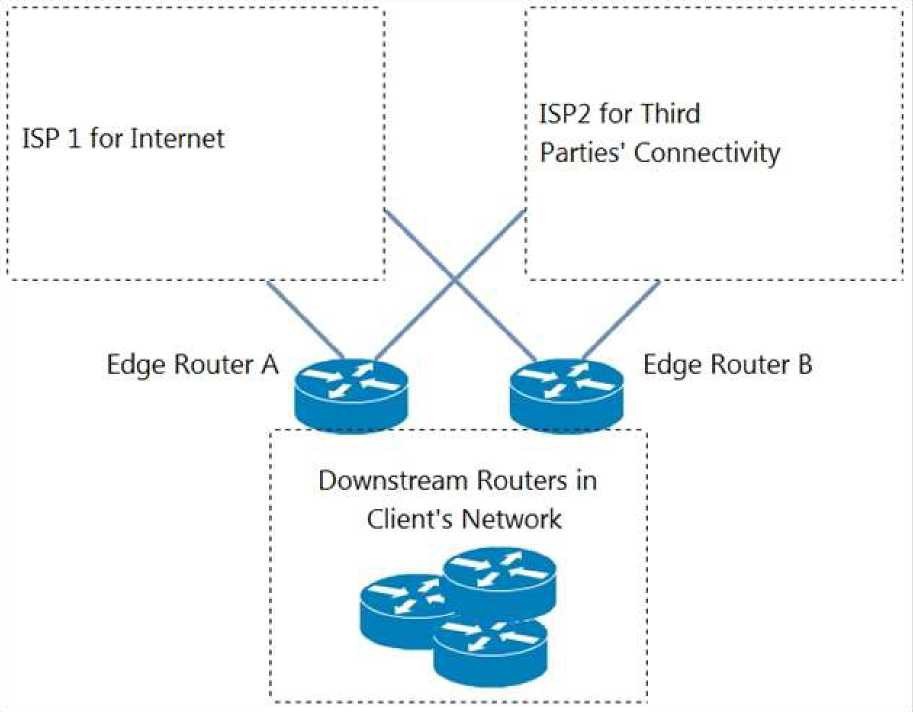
Refer to the exhibit. An engineer is designing a BGP solution for a client that peers with
ISP1 for full Internet connectivity and with ISP2 for direct exchange of routes for several
third parties. Which action, when implemented on the edge routers, enables the client
network to reach the Internet through ISP1?
A.
Run an eBGP session within different VRFs for each ISP.
B.
Advertise a default route for downstream routers within the client network.
C.
Apply the AS-path prepend feature for ISP2.
D.
Apply route filtering such that the client advertises only routes originated from its own
AS.
Advertise a default route for downstream routers within the client network.
An engineer is designing a QoS policy that queues excess packets for later transmission.
Which mechanism must be included in the design?
A.
shaping
B.
WRED
C.
policing
D.
RED
shaping
Refer to the exhibit.
An engineer must optimize the traffic flow of the network. Which change provides a more
efficient design between the access and the distribution layer?
A.
Add a link between access switch A and access switch B
B.
Reconfigure the distribution switch A to become the HSRP Active
C.
Change the link between distribution switch A and distribution switch B to be a
routed link
D.
Create an EtherChannel link between distribution switch A and distribution switch
B
Reconfigure the distribution switch A to become the HSRP Active

Refer to the exhibit. A customer needs to apply QoS to the network management traffic
passing through the GigabitEthernet0/2 interface. All eight queuing classes are in use, so
the new requirement must be integrated into the existing policy. Which solution must the
customer choose?
A.
Mark traffic to DSCP CS5 and assign it to the SIGNALLING class. Then, baseline
existing queue sizes to determine if additional bandwidth can be provisioned to the
SIGNALLING class.
B.
Mark the traffic to DSCP CS4 and assign it to the SIGNALLING class. Then, prioritize traffic within the class.
C.
Mark the traffic to DSCP CS6 and assign it to the ROUTING class Then, prioritize traffic within the class.
D.
Mark the traffic to DSCP CS2 and assign it to the ROUTING class Then, baseline existing queue sizes to determine if additional bandwidth can be provisioned to the
ROUTING class
Mark the traffic to DSCP CS2 and assign it to the ROUTING class Then, baseline existing queue sizes to determine if additional bandwidth can be provisioned to the
ROUTING class
| Page 10 out of 27 Pages |
| Previous |