Topic 2, Exam Pool B
Refer to the exhibit.
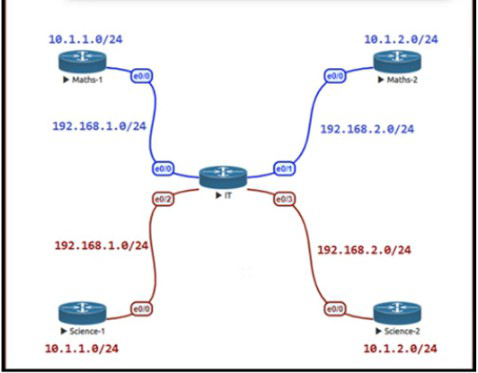
The Math and Science departments connect through the corporate. IT router but users in the Math department must not be able to reach the Science department and vice versa Which configuration accomplishes this task?
A.
vrf definition Science
interface E 0/2
ip address 192.168.1.1 255.255.255.0
no shut
interface E 0/3
ip address 192.168.2.1 255.255.255.0
no shut
B.
vrf definition Science
address-family ipv4
!
interface E 0/2
ip address 192.168.1.1 255.255.255.0
vrf forwarding Science
no shut
!
interface E 0/3
ip address 192.168.2.1 255.255.255.0
vrf forwarding Science
no shut
C.
vrf definition Science
address-family ipv4
!
interface E 0/2
ip address 192.168.1.1 255.255.255.0
no shut
!
interface E 0/3
ip address 192.168.2.1 255.255.255.0
no shut
D.
vrf definition Science
address-family ipv4
!
interface E 0/2
vrf forwarding Science
ip address 192.168.1.1 255.255.255.0
no shut
!
interface E 0/3
vrf forwarding Science
ip address 192.168.2.1
vrf definition Science
address-family ipv4
!
interface E 0/2
vrf forwarding Science
ip address 192.168.1.1 255.255.255.0
no shut
!
interface E 0/3
vrf forwarding Science
ip address 192.168.2.1
Refer to the exhibit.
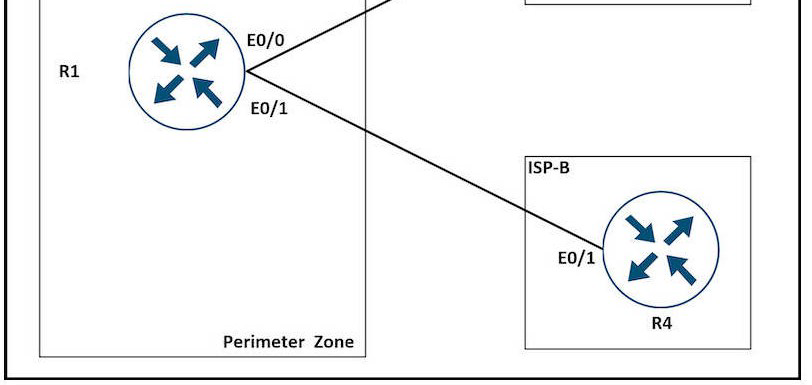
A network is under a cyberattack. A network engineer connected to R1 by SSH and enabled the terminal monitor via SSH session to find the source and destination of the attack. The session was flooded with messages, which made it impossible for the engineer to troubleshoot the issue. Which command resolves this issue on R1?
A.
no terminal monitor
B.
(config)#terminal no monitor
C.
#terminal no monitor
D.
(config)#no terminal monitor
#terminal no monitor
Which Ipv6 first-hop security feature helps to minimize denial of service attacks?
A.
IPv6 Router Advertisement Guard
B.
IPv6 Destination Guard
C.
DHCPv6 Guard
D.
IPv6 MAC address filtering
IPv6 Destination Guard
Explanation:
The Destination Guard feature helps in minimizing denial-of-service (DoS) attacks. It performs address resolutions only for those addresses that are active on the link,and requires the FHS binding table to be populated with the help of the IPv6 snooping feature.The feature enables the filtering of IPv6 traffic based on the destinationaddress, and blocks the NDP resolution for destination addresses that are not found in the binding table. By default, the policy drops traffic coming for an unknowndestination.
Refer to Exhibit.
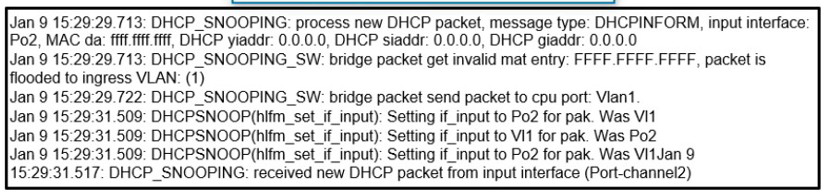
A network administrator enables DHCP snooping on the Cisco Catalyst 3750-X switch and configures the uplink port (Port-channel2) as a trusted port. Clients are not receiving an IP address, but when DHCP snooping is disabled, clients start receiving IP addresses. Which global command resolves the issue?
A.
No ip dhcp snooping information option
B.
ip dhcp snooping
C.
ip dhcp relay information trust portchannel2
D.
ip dhcp snooping trust
No ip dhcp snooping information option
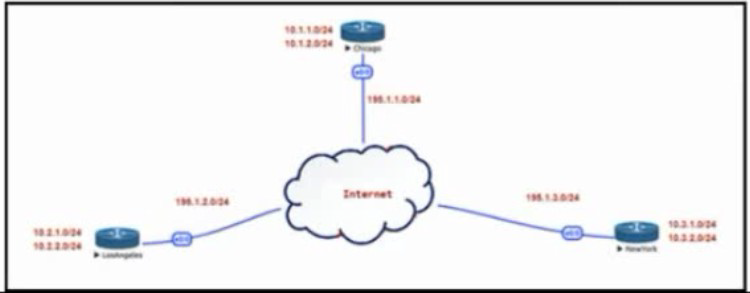
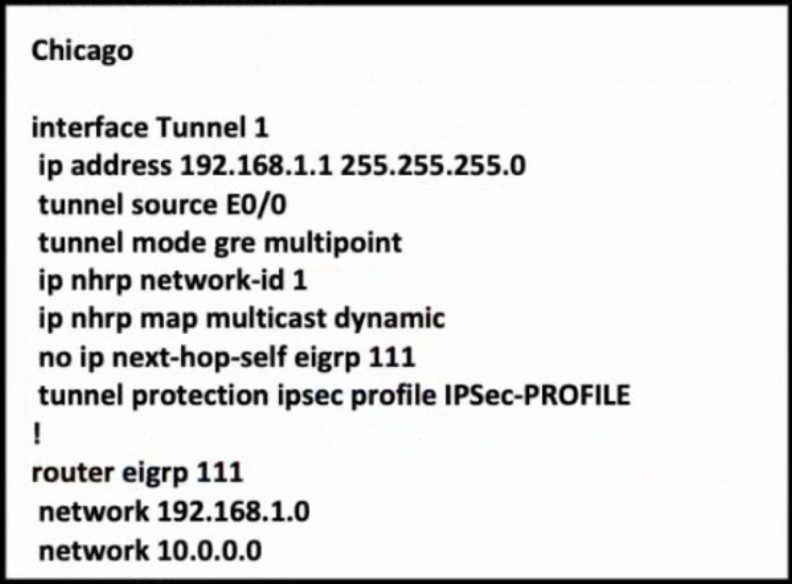
Refer to the exhibit. The Los Angeles and New York routers are receiving routes from Chicago but not from each other. Which configuration fixes the issue?
A.
Interface Tunnel1
no ip split-horizon eigrp 111
B.
Interface Tunnel1
Ip next-hop-self elgrp 111
C.
Interface Tunnel1
tunnel mode Ipsec Ipv4
D.
Interface Tunnel1
tunnel protection ipsec profile IPSec-PROFILE
Interface Tunnel1
no ip split-horizon eigrp 111
Explanation: In this topology, Chicago router (Hub) will receive advertisements from Los Angeles (Spoke1) router on its tunnel interface. The problem here is that it also has a connection with New York (Spoke2) on that same tunnel interface. If we don’t disable EIGRP split-horizon, then the Hub will not relay routes from Spoke1 to Spoke2 and the other way around. That is because it received those routes on interface Tunnel1 and therefore it cannot advertise back out that same interface (splithorizon rule). Therefore we must disable split-horizon on the Hub router to make sure the Spokes know about each other.
How are MPLS Layer 3 VPN services deployed?
A.
The RD and RT values must match under the VRR
B.
The RD and RT values under a VRF must match on the remote PE router
C.
The import and export RT values under a VRF must always be the same
D.
The label switch path must be available between the local and remote PE routers
The label switch path must be available between the local and remote PE routers
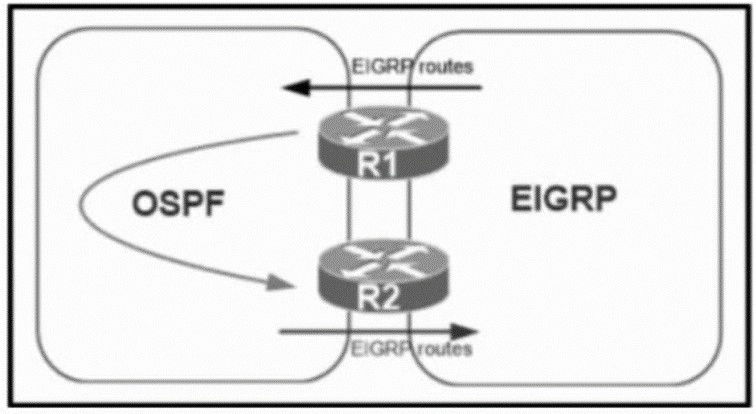
Refer to the exhibit. A network administrator configured mutual redistribution on R1 and R2 routers, which caused instability in the network. Which action resolves the issue?
A.
Set a tag in the route map when redistributing EIGRP into OSPF on R1. and match the same tag on R2 to deny when redistributing OSPF into EIGRP.
B.
Set a tag in the route map when redistributing EIGRP into OSPF on R1. and match the same tag on R2 to allow when redistributing OSPF into EIGRP.
C.
Advertise summary routes of EIGRP to OSPF and deny specific EIGRP routes when redistributing into OSPF.
D.
Apply a prefix list of EIGRP network routes in OSPF domain on R1 to propagate back into the EIGRP routing domain.
Set a tag in the route map when redistributing EIGRP into OSPF on R1. and match the same tag on R2 to deny when redistributing OSPF into EIGRP.
Which IGPs are supported by the MPLS LDP autoconfiguration feature?
A.
RIPv2 and OSPF
B.
OSPF and EIGRP
C.
OSPF and ISIS
D.
ISIS and RIPv2
OSPF and ISIS
Refer to the exhibit.
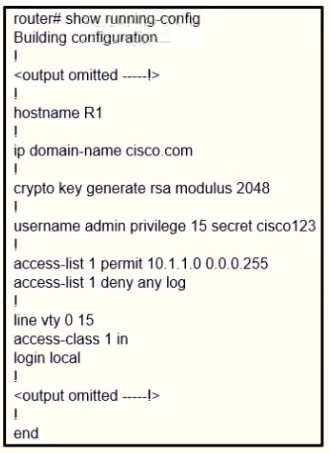
A user cannot SSH to the router. What action must be taken to resolve this issue?
A.
Configure transport input ssh
B.
Configure transport output ssh
C.
Configure ip ssh version 2
D.
Configure ip ssh source-interface loopback0
Configure transport input ssh
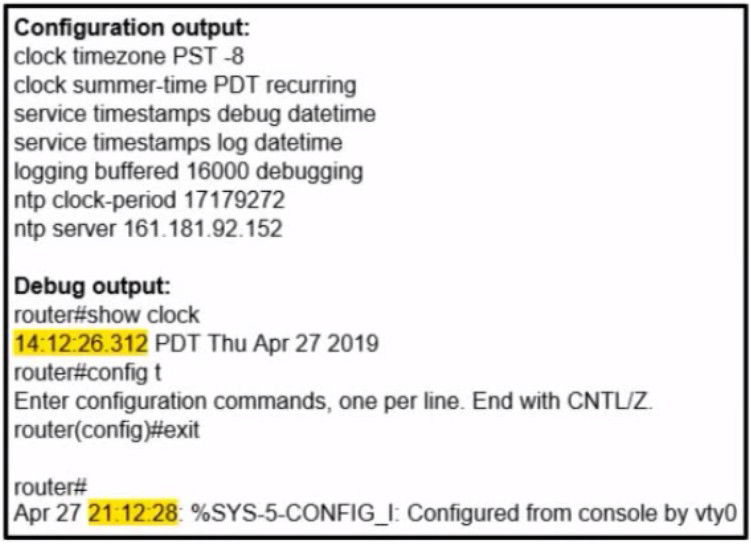
Refer to the exhibit. A network administrator configured NTP on a Cisco router to get synchronized time for system and logs from a unified time source The configuration did not work as desired Which service must be enabled to resolve the issue?
A.
Enter the service timestamps log datetime localtime global command.
B.
Enter the service timestamps log datetime synchronize global command.
C.
Enter the service timestamps log datetime console global command.
D.
Enter the service timestamps log datetime clock-period global command
Enter the service timestamps log datetime localtime global command.
Refer to the exhibit.
An IT staff member comes into the office during normal office hours and cannot access devices through SSH Which action should be taken to resolve this issue?
A.
Modify the access list to use the correct IP address.
B.
Configure the correct time range.
C.
Modify the access list to correct the subnet mask
D.
Configure the access list in the outbound direction.
Modify the access list to use the correct IP address.
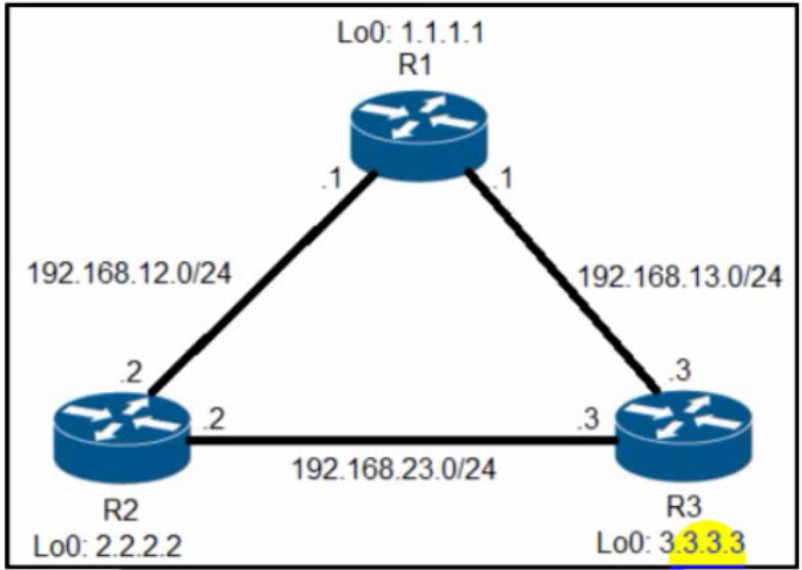

Refer to the exhibit. R2 has two paths to reach 192.168.13.0/24. but traffic is sent only through R3. Which action allows traffic to use both paths?
A.
Configure the bandwidth 2000 command under interface FastEthernet0/0 on R2.
B.
Configure the variance 4 command under the EIGRP process on R2.
C.
Configure the delay 1 command under interface FastEthernet0/0 on R2.
D.
Configure the variance 2 command under the EIGRP process on R2
Configure the variance 4 command under the EIGRP process on R2.
| Page 12 out of 47 Pages |
| Previous |