Topic 2: Exam Pool B
A macOS user needs to create another virtual desktop space. Which of the following applications will allow the user to accomplish this task?
A. Dock
B. Spotlight
C. Mission Control
D. Launchpad
Explanation:
application that will allow a macOS user to create another virtual desktop space is Mission
Control Mission Control lets you create additional desktops, called spaces, to organize the
windows of your apps. You can create a space by entering Mission Control and clicking the
Add button in the Spaces bar1. You can also assign apps to specific spaces and move
between them easily1.
A customer recently experienced a power outage at a SOHO. The customer does not think
the components are connected properly. A print job continued running for several minutes
after the power failed, but the customer was not able to interact with the computer. Once
the UPS stopped beeping, all functioning devices also turned off. In case of a future power
failure, the customer wants to have the most time available to save cloud documents and
shut down the computer without losing any data.
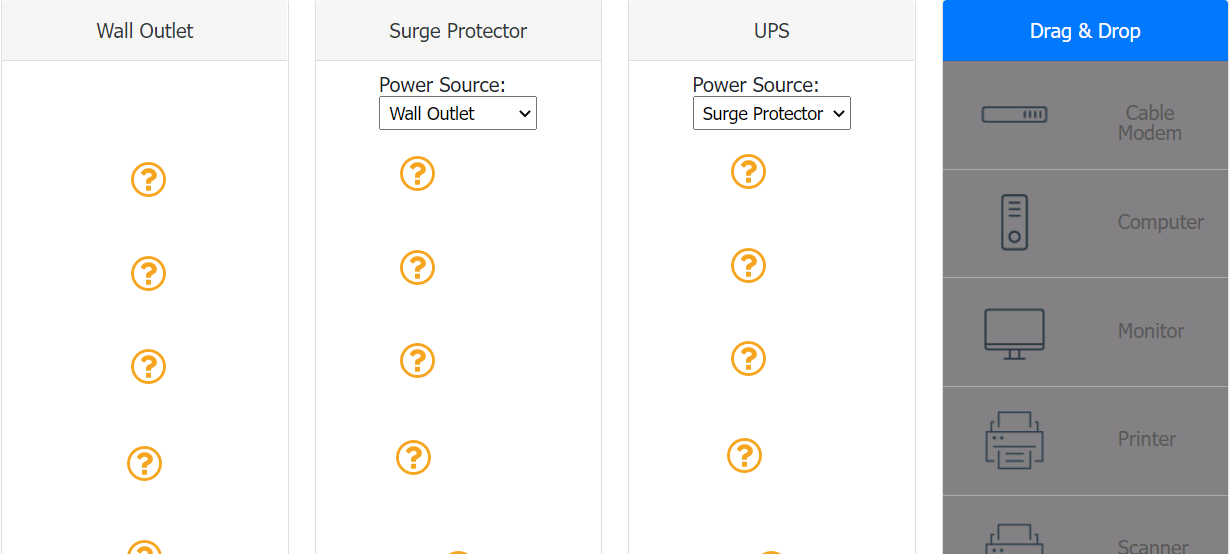
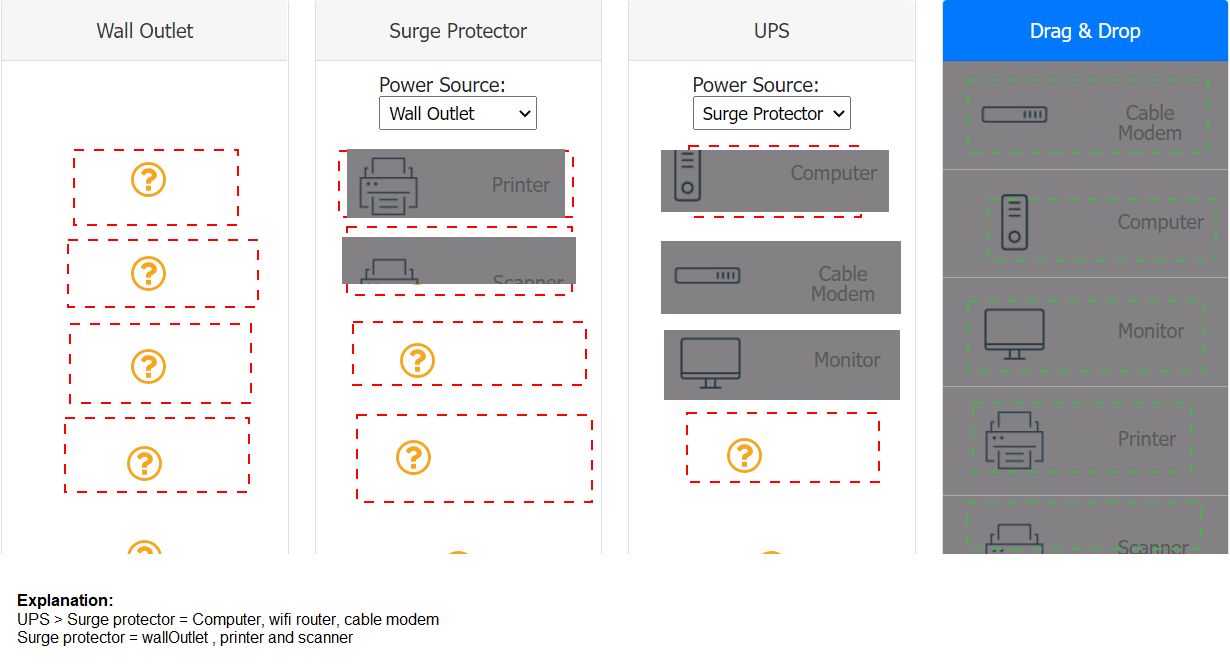
Which of the following file extensions are commonly used to install applications on a macOS machine? (Select THREE).
A. .mac
B. .Pkg
C. .deb
D. .dmg
E. .msi
F. .appx
G. .app
H. .apk
Which of the following is an example of MFA?
A. Fingerprint scan and retina scan
B. Password and PIN
C. Username and password
D. Smart card and password
Explanation:
Smart card and password is an example of two-factor authentication (2FA), not multi-factor
authentication (MFA). MFA requires two or more authentication factors. Smart card and
password is an example of two-factor authentication (2FA)2.
While assisting a customer with an issue, a support representative realizes the appointment is taking longer than expected and will cause the next customer meeting to be delayed by five minutes. Which of the following should the support representative do NEXT?
A. Send a quick message regarding the delay to the next customer
B. Cut the current customer's lime short and rush to the next customer
C. Apologize to the next customer when arriving late.
D. Arrive late to the next meeting without acknowledging the lime.
Explanation:
The support representative should send a quick message regarding the delay to the next
customer. This will help the next customer understand the situation and adjust their
schedule accordingly.
A technician just completed a Windows 10 installation on a PC that has a total of 16GB of RAM. The technician notices the Windows OS has only 4GB of RAM available for use. Which of the following explains why the OS can only access 46B of RAM?
A. The UEFI settings need to be changed.
B. The RAM has compatibility issues with Windows 10.
C. Some of the RAM is defective
D. The newly installed OS is x86.
Explanation:
The newly installed OS is x86. The x86 version of Windows 10 can only use up to 4GB of
RAM. The x64 version of Windows 10 can use up to 2TB of RAM1.
Sensitive data was leaked from a user's smartphone. A technician discovered an unapproved application was installed, and the user has full access to the device's command shell. Which of the following is the NEXT step the technician should take to find the cause of the leaked data?
A. Restore the device to factory settings.
B. Uninstall the unapproved application
C. Disable the ability to install applications from unknown sources
D. Ensure the device is connected to the corporate WiFi network
Explanation:
The technician should disable the user’s access to the device’s command shell. This will
prevent the user from accessing sensitive data and will help to prevent further data leaks.
The technician should then investigate the unapproved application to determine if it is the
cause of the data leak. If the application is found to be the cause of the leak, the technician
should uninstall the application and restore the device to factory settings. If the application
is not the cause of the leak, the technician should investigate further to determine the
cause of the leak. Disabling the ability to install applications from unknown sources can
help to prevent future data leaks, but it is not the next step the technician should take in this
scenario. Ensuring the device is connected to the corporate WiFi network is not relevant to
this scenario1.
A company discovered that numerous computers from multiple geographic locations are sending a very high number of connection requests which is causing the company’s web server to become unavailable to the general public. Which of the following attacks is occurring?
A. Zero day
B. SOL injection
C. Cross-site scripting
D. Distributed denial of service
Explanation:
The company is experiencing a distributed denial of service (DDoS) attack. A DDoS attack
is a type of cyber attack in which multiple compromised systems are used to target a single system, causing a denial of service for users of the targeted system.
A technician is troubleshooting a smartphone that is unable to download and install the latest OS update. The technician notices the device operates more slowly than expected, even after rebooting and closing all applications. Which of the following should the technician check next?
A. Application permissions
B. Available storage space
C. Battery charge level
D. Wi-Fi connection speed
Explanation:
When a smartphone is unable to download and install the latest OS update and is
operating slower than expected, one of the first things to check is the available storage
space. Operating system updates often require a significant amount of free space for
downloading and installing, and insufficient space can prevent the update process from
initiating or completing.
Available Storage Space: Smartphones use their internal storage to hold the OS,
apps, user data, and temporary files needed for updates. If the storage is nearly
full, the device can slow down due to the lack of space for writing temporary files
and may not have enough space to download and install updates. Clearing up
space can resolve these issues.
Checking application permissions (A) might be relevant for specific app-related issues but
is less likely to affect OS updates. The battery charge level (C) can affect the initiation of an
update, as some devices require a minimum charge level to start the update process, but it
doesn't typically cause slow operation. While a stable Wi-Fi connection (D) is necessary for
downloading updates, it's less likely to be the cause of slowed operation and update issues
compared to insufficient storage space.
Multiple users routinely record log-in information in readily accessible areas. Which of the following is the best way to mitigate this issue?
A. Trusted sources
B. Valid certificates
C. User training
D. Password manager
Explanation: Using a password manager is the best way to mitigate the issue of users recording their login information in accessible areas. Password managers securely store and encrypt passwords and login details, reducing the need for users to write down or remember multiple complex passwords. This approach enhances security by encouraging the use of strong, unique passwords for different accounts without the risk of forgetting them or the unsafe practice of writing them down. Trusted sources, valid certificates, and user training are important security measures but do not directly address the problem of managing multiple secure passwords as effectively as a password manager does.
A mobile phone user has downloaded a new payment application that allows payments to be made with a mobile device. The user attempts to use the device at a payment terminal but is unable to do so successfully. The user contacts a help desk technician to report the issue. Which of the following should the technician confirm NEXT as part of the troubleshooting process?
A. If airplane mode is enabled
B. If Bluetooth is disabled
C. If NFC is enabled
D. If WiFi is enabled
E. If location services are disabled
Explanation:
NFC stands for Near Field Communication, and it is a wireless technology that allows your
phone to act as a contactless payment device, among other things2. Payment applications
that allow payments to be made with a mobile device usually rely on NFC to communicate
with the payment terminal1. Therefore, if NFC is disabled on the phone, the payment will
not work. To enable NFC on an Android phone, you need to follow these steps3:
A user is attempting to make a purchase at a store using a phone. The user places the phone on the payment pad, but the device does not recognize the phone. The user attempts to restart the phone but still has the same results. Which of the following should the user do to resolve the issue?
A. Turn off airplane mode while at the register.
B. Verify that NFC is enabled.
C. Connect to the store's Wi-Fi network.
D. Enable Bluetooth on the phone
Explanation:
The user should verify that NFC is enabled on their phone. NFC is a technology that allows
two devices to communicate with each other when they are in close proximity2.
NFC (Near Field Communication) technology allows a phone to wirelessly communicate
with a payment terminal or other compatible device. In order to use NFC to make a
payment or transfer information, the feature must be enabled on the phone. Therefore, the
user should verify that NFC is enabled on their phone before attempting to make a
payment with it. The other options, such as turning off airplane mode, connecting to Wi-Fi,
or enabling Bluetooth, do not pertain to the NFC feature and are unlikely to resolve the
issue. This information is covered in the Comptia A+ Core2 documents/guide under the
Mobile Devices section.
| Page 27 out of 62 Pages |
| Previous |