Topic 5: Exam Pool E (NEW)
A third-party contractor recently installed a new switch, router, and cabling for a small corporate office. After the installation, users started experiencing issues connecting to resources over the network.
INSTRUCTIONS
Click on each PC and server to review outputs. From the remediation section on the right, select an issue and solution for each device.
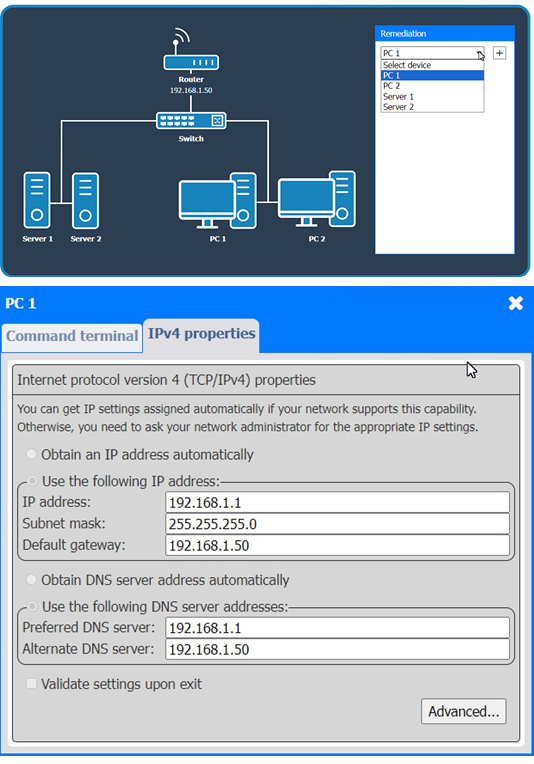
Answer: See the Explanation and detailed steps below.
Explanation:
Looking at the network configurations and outputs from both PCs and servers, here are the possible issues and solutions:
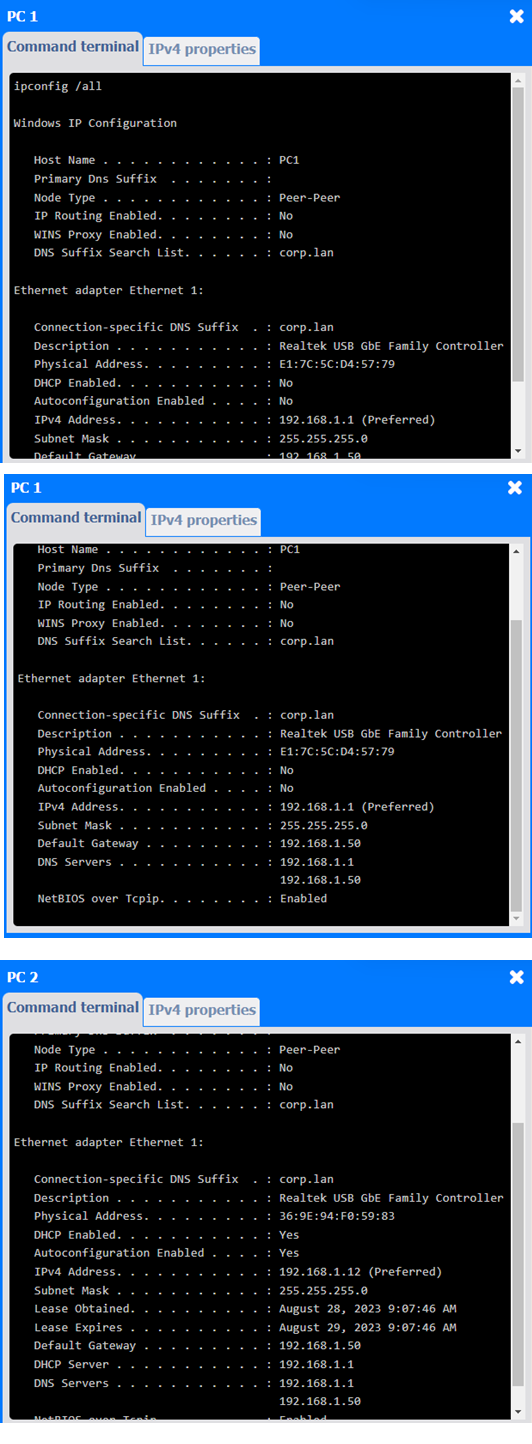
1. PC 1
✑ Issue: The IP address for PC1 is 192.168.1.1, which conflicts with Server 1 (which also uses 192.168.1.1).
✑ Solution: Change the IP address on PC1 to a unique one within the range, like 192.168.1.3.
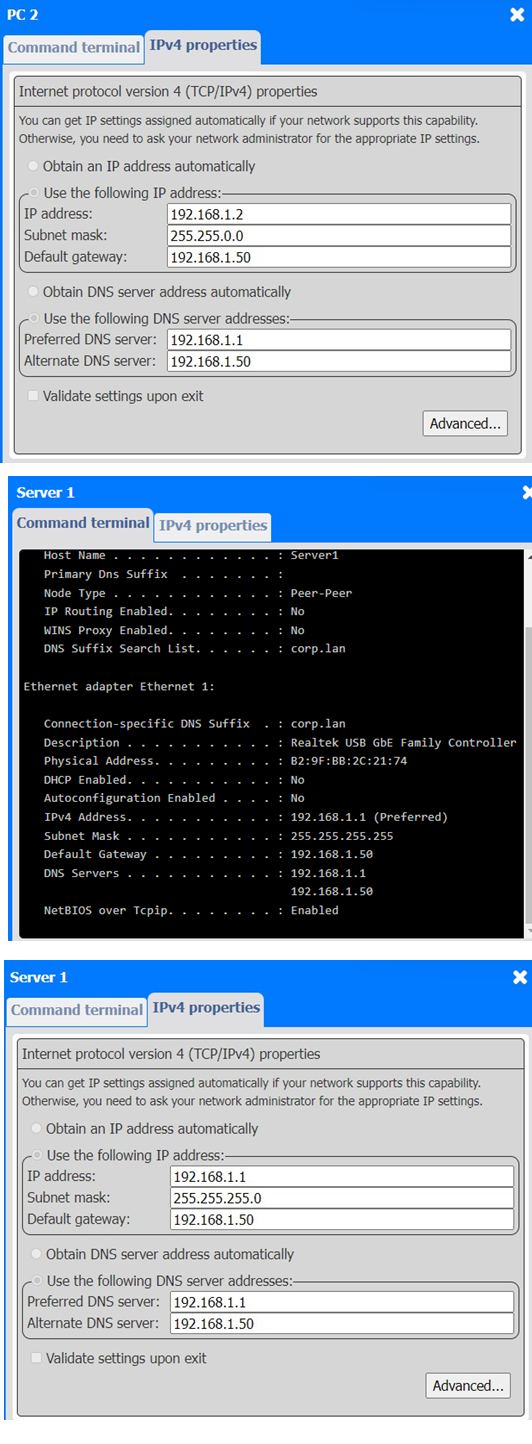
2. PC 2
✑ Issue: PC 2 is configured with 192.168.1.2, which conflicts with Server 2 that has the same IP address.
✑ Solution: Update the IP address on PC 2 to something unique, like 192.168.1.4.
3. Server 1
✑ Issue: The IP address for Server 1 is 192.168.1.1, which conflicts with PC1.
✑ Solution: Since Server 1 and PC1 are using the same IP address, change one of them. For Server 1, you could change the IP address to 192.168.1.5.
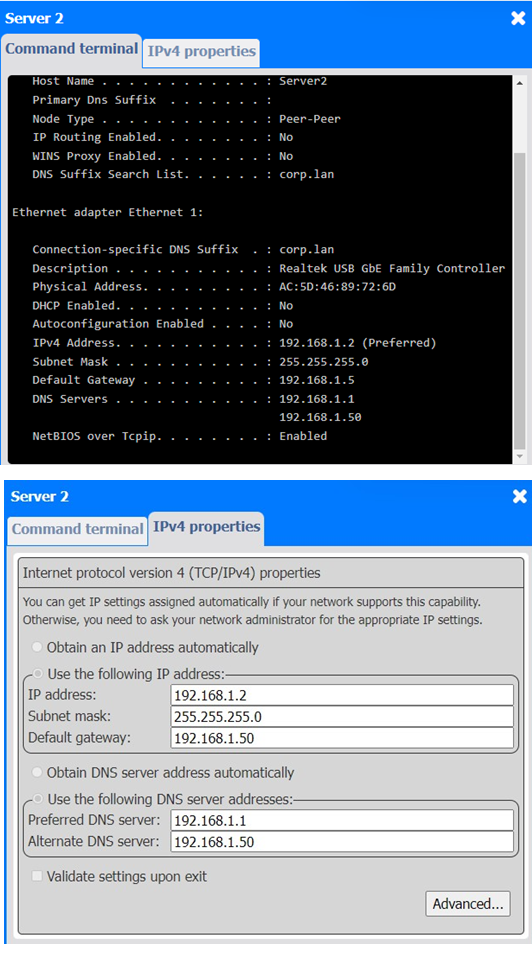
4. Server 2
✑ Issue: Server 2 is using the IP address 192.168.1.2, which conflicts with PC2.
✑ Solution: Update Server 2 to use a different IP address, such as 192.168.1.6.
General Remediation:
The primary problem here is overlapping IP addresses, leading to connectivity issues. Each device on the network must have a unique IP address. After making these changes, ensure that all devices can communicate properly by testing the connection between devices and verifying they can access shared resources.
A company wants to give third-party developers access to the corporate network through desktop environments that the company can control. Which of the following can BEST achieve these requirements?
A. Sandbox
B. VDI
C. Private cloud
D. Saas
Explanation: VDI is a technology that allows a company to provide desktop environments to third-party developers while still maintaining control over the corporate network. VDI creates virtual desktops on a remote server, and each user gets their own desktop environment that is isolated from the other users. This allows the company to maintain control over the corporate network, as the virtual desktops are not directly connected to the corporate network.
A technician needs to update a web server's IPv4 address in a DNS server. Which of the following records should the technician update?
A. AAAA
B. MX
C. CNAME
D. A
A user who works with sensitive data has a computer configured with hard drive encryption The TPM is active and hosting the encrypted key. After an upgrade to the motherboard. RAM and video card the hard drive is not booting and data cannot be accessed from the hard drive. Which of the following should the technician do to enable the system to boot again and get access to the stored data?
A. Use data recovery software to find and recover the hard drive information
B. Access the BIOS and select to rebuild the degraded RAID array
C. Boot into the BIOS and enable the TPM on the new motherboard
D. Return the replaced motherboard back to the computer
Explanation: The technician should boot into the BIOS and enable the TPM on the new motherboard to enable the system to boot again and get access to the stored data1. Boot into the BIOS and enable the TPM on the new motherboard. Explanation: After upgrading the motherboard, the TPM may need to be enabled in the BIOS in order to access the encrypted key and boot the system. Enabling the TPM on the new motherboard should allow the system to boot and provide access to the encrypted data. References: CompTIA A+ Certification Exam Guide, 220-1001, Chapter 13
Which of the following DNS record types is used to direct email to a mail server?
A. CNAME
B. SRV
C. MX
D. SOA
Which of the forming connector types would best suit a company that experiences a large volume of internet traffic?
A. USB 3.1
B. Quad-shielded RG11 coax
C. SATA3.0
D. Unshielded plenum RJ45
Explanation:
RG11 coaxial cable with quad shielding is designed to handle large volumes of internet traffic, providing excellent resistance to interference and high bandwidth capacity.
✑ Why Not A (USB 3.1): USB 3.1 is used for connecting peripherals, not for high-
volume internet traffic.
✑ Why Not C (SATA3.0): SATA is used for internal data storage connections, not for network traffic.
✑ Why Not D (Unshielded plenum RJ45): While RJ45 cables are commonly used, unshielded cables are prone to interference and are not ideal for high-volume traffic.
CompTIA A+ Exam Reference: Core 1 (220-1101), Section 3.1, cable types and their characteristics.
An employee cannot connect to the wireless network at the office but can connect to a personal wireless network when at home. The technician verifies the wireless network name is correct, and the signal strength appears to be strong. Which of the following is the best action for the technician to take to resolve the issue?
A. Install the current 802.1X certificate.
B. Check the wireless router settings.
C. Update the wireless driver.
D. Disable the Windows firewall.
Explanation: 802.1X is a network authentication protocol commonly used in enterprise environments. If the user cannot connect to the office wireless network but can connect at home, the issue is likely related to the 802.1X certificate required for authentication.
Installing or updating the certificate will resolve the issue.
✑ Why Not B (Check the wireless router settings): If other users can connect to the network, this step is unnecessary.
✑ Why Not C (Update the wireless driver): Driver updates might resolve connectivity issues but are unrelated to 802.1X certificate authentication.
✑ Why Not D (Disable the Windows firewall): The firewall does not affect 802.1X authentication.
CompTIA A+ Exam Reference: Core 1 (220-1101), Section 2.6, wireless network authentication.
Which of the following best describes the concept of a DHCP lease?
A. A definition of the scope of addresses to be assigned to a device on the network
B. A reservation of an IP configuration for a device on the network
C. A temporary assignment of an IP configuration to a device on the network
D. A translation of network names to IP addresses for a device on the network
Explanation: A DHCP lease is a temporary assignment of an IP address and other network configuration parameters (such as DNS and gateway) to a device. The lease is renewed periodically to maintain the assignment. ✑ Why Not A (A definition of the scope of addresses): The DHCP scope defines the range of IP addresses but is not the lease itself. ✑ Why Not B (A reservation of an IP configuration): DHCP reservations ensure a specific device always receives the same IP address, but this is not the lease. ✑ Why Not D (A translation of network names to IP addresses): This describes DNS, not DHCP. CompTIA A+ Exam Reference: Core 1 (220-1101), Section 2.6, DHCP concepts.
Which of the following devices is used to implement ACL polices for an environment?
A. Managed switch
B. Gateway
C. Repeater
D. Firewall
Explanation: A firewall implements ACLs (Access Control Lists) to filter traffic and enforce policies based on rules such as IP address, port, or protocol.
✑ Why Not A (Managed switch): A managed switch supports VLANs and QoS but
does not enforce ACLs at the network perimeter.
✑ Why Not B (Gateway): Gateways connect networks and translate protocols but don’t typically implement ACLs.
✑ Why Not C (Repeater): Repeaters extend signal range but don’t enforce policies.
CompTIA A+ Exam Reference: Core 1 (220-1101), Section 2.2, firewall concepts.
A company wants to save printing costs by restricting network printer use. The company implements a solution that requires employees to authenticate to the printer to release print jobs Which of the following has the company implemented?
A. Access control list
B. Audit logging
C. Badging
D. Print server
Explanation: Badging is a form of authentication that requires employees to use a badge or ID card to release print jobs. This solution reduces unnecessary printing by ensuring only authorized users print.
✑ Why Not A (Access control list): While ACLs manage permissions, they are not
used for physical authentication at printers.
✑ Why Not B (Audit logging): Audit logs track actions but do not restrict printer access.
✑ Why Not D (Print server): A print server manages print jobs but doesn’t enforce authentication.
CompTIA A+ Exam Reference: Core 2 (220-1102), Section 2.5, authentication mechanisms.
A user calls the help desk lot assistance configuring an Android phone with a new NFCenabled speaker that will be used for an upcoming conference call. The user was unable to direct the phone's audio to the NFC speaker. Which of the following sequences should the help desk technician walk the customer through to accomplish this task?
A. Enable NFC on the speaker. Ensure the speaker is less than 33ft (10m) from the Android phone. On the phone's Bluetooth settings menu for Connected Devices, select Pair New Device. Tap to accept the connection to the speaker when the prompt is displayed on the phone's screen.
B. Enable NFC and Bluetooth on the Android phone. From the Android phone's Bluetooth settings menu for Connected Devices, select the Previously Connected Devices option. Select a listed device that most closely matches the speaker. Tap lo accept the connection lo the speaker when the prompt is displayed on the phone's screen.
C. Enable NFC and Bluetooth on the Android phone. Tap and hold the Android phone to the spot on the speaker where the NFC logo is displayed. Accept the connection to the speaker when the prompt is displayed on the phone's screen.
D. Enable Wi-Fi on the speaker. Enable Wi-Fi on the Android phone. Tap and hold the Android phone to the spot on the speaker where the NFC logo is displayed. Accept the connection to the speaker when the prompt is displayed on the phone's screen.
A technician is troubleshooting a smartphone that has a large dark area on the screen. The screen has no damage to Indicate that It is cracked. Which of the following BEST describes why a blot Is on the screen?
A. Digitizer damage
B. Improper charging
C. Ambient light sensor damage
D. Liquid damage
Explanation: A blot on the screen of a smartphone is most likely caused by damage to the digitizer, which is the part of the device responsible for interpreting touch input. Improper charging is unlikely to cause a blot on the screen, as is damage to the ambient light sensor. Liquid damage is a possibility, but it is more likely to cause discoloration or other physical damage to the screen.
| Page 29 out of 71 Pages |
| Previous |