Topic 2, Exam B
Which technology must be implemented to configure network device monitoring with the highest security?
A. IP SLA
B. syslog
C. NetFlow
D. SNMPv3
Refer to the exhibit.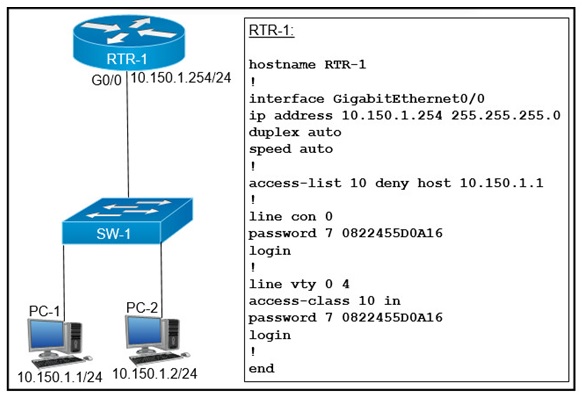
An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access from all other hosts A Telnet attempt from PC-2 gives this message:"% Connection refused by remote host" Without allowing Telnet access from PC-1, which action must be taken to permit the traffic?
A. Add the access-list 10 permit any command to the configuration
B. Remove the access-class 10 in command from line vty 0.4.
C. Add the ip access-group 10 out command to interface g0/0.
D. Remove the password command from line vty 0 4.
How does WPA3 improve security?
A. It uses SAE for authentication.
B. It uses a 4-way handshake for authentication.
C. It uses RC4 for encryption.
D. It uses TKIP for encryption.
What role does a hypervisor provide for each virtual machine in server virtualization?
A.
infrastructure-as-a-service.
B.
Software-as-a-service
C.
control and distribution of physical resources
D.
services as a hardware controller.
control and distribution of physical resources
Explanation: The hypervisor creates and manages virtual machines on a host computer
and allocates physical system resources to them.
R1 has learned route 192.168.12.0/24 via IS-IS. OSPF, RIP. and Internal EIGRP Under normal operating conditions, which routing protocol is installed in the routing table?
A. IS-IS
B. RIP
C. Internal EIGRP
D. OSPF
Refer to the exhibit
With which metric was the route to host 172.16.0.202 learned?
A. 0
B. 110
C. 38443
D. 3184439
Explanation:
Both the line “O 172.16.0.128/25” and “S 172.16.0.0/24” cover the host 172.16.0.202 but with the “longest (prefix) match” rule the router will choose the first route.
Refer to Exhibit.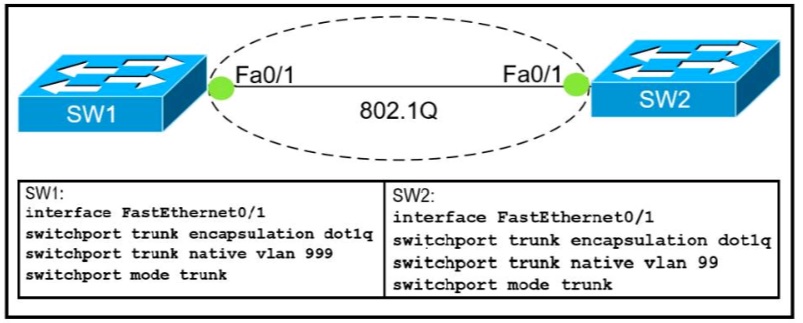
Which action do the switches take on the trunk link?
A. The trunk does not form and the ports go into an err-disabled status.
B. The trunk forms but the mismatched native VLANs are merged into a single broadcast domain.
C. The trunk does not form, but VLAN 99 and VLAN 999 are allowed to traverse the link.
D. The trunk forms but VLAN 99 and VLAN 999 are in a shutdown state.
Explanation:
The trunk still forms with mismatched native VLANs and the traffic can
actually flow between mismatched switches. But it is absolutely necessary that the native
VLANs on both ends of a trunk link match; otherwise a native VLAN mismatch occurs,
causing the two VLANs to effectively merge.
For example with the above configuration, SW1 would send untagged frames for VLAN
999. SW2 receives them but would think they are for VLAN 99 so we can say these two
VLANs are merged
Which 802.11 frame type is indicated by a probe response after a client sends a probe request?
A. action
B. management
C. control
D. data
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closer? (Choose two.)
A. enable the PortFast feature on ports
B. implement port-based authentication
C. configure static ARP entries
D. configure ports to a fixed speed
E. shut down unused ports
Refer to the exhibit.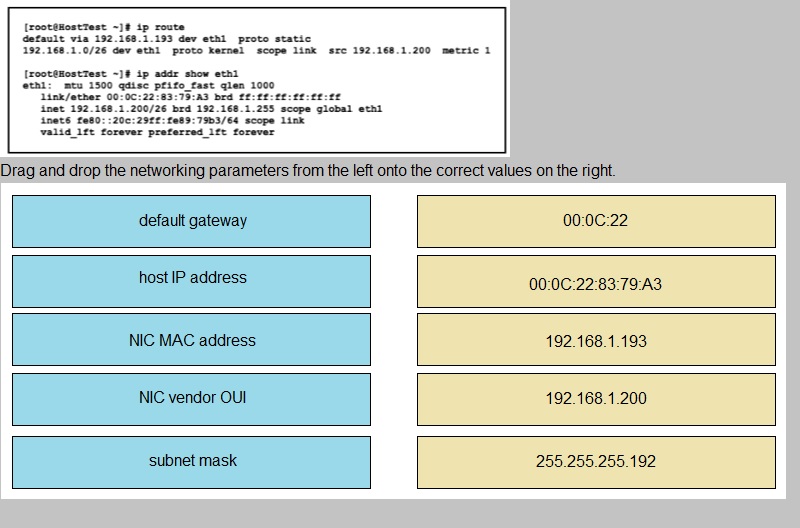

Refer to the exhibit.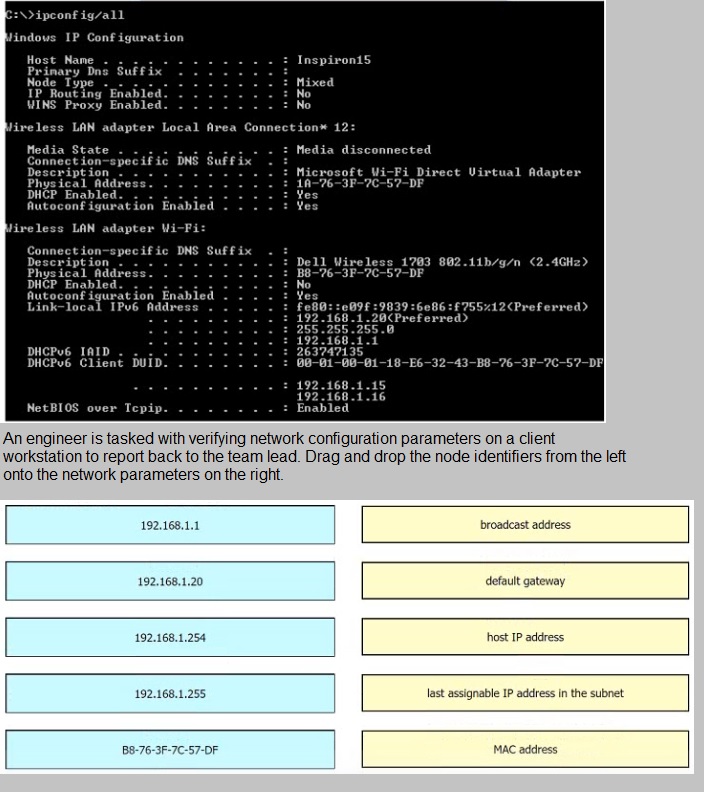

What is the purpose of an SSID?
A. It provides network security
B. It differentiates traffic entering access posits
C. It identities an individual access point on a WLAN
D. It identifies a WLAN
Explanation:
“In IEEE 802.11 wireless local area networking standards (including Wi-Fi), a
service set is a group of wireless network devices which share a service set identifier
(SSID)… A service set forms a logical network of nodes operating with shared link-layer networking parameters; they form one logical network segment.
| Page 28 out of 72 Pages |
| Previous |