Topic 1: Exam Pool A
desc about topic
What are two southbound APIs? (Choose two )
A. OpenFlow
B. NETCONF
C. Thrift
D. CORBA
E. SC
Explanation:
In a Software-Defined Networking (SDN) architecture, APIs (Application Programming Interfaces) are categorized based on the direction of communication relative to the SDN Controller.
Southbound APIs are used for communication from the controller down to the network devices (switches, routers, etc.). They are used to push configuration and forwarding rules to the data plane.
The two primary and most relevant southbound APIs in modern networking are:
OpenFlow:
This is a standardized, protocol-based API that allows the controller to directly manipulate the forwarding tables of switches. It is one of the earliest and most fundamental SDN southbound interfaces.
NETCONF (Network Configuration Protocol):
This is a protocol defined by the IETF (RFC 6241) used to install, manipulate, and delete the configuration of network devices. It uses a structured data format (XML) and is often paired with YANG data models. It is a more general and powerful configuration interface than OpenFlow.
Why the other options are incorrect:
C. Thrift:
Thrift is a general-purpose interface definition and RPC (Remote Procedure Call) framework developed by Facebook. While it could be used to build an API, it is not a standard or recognized southbound API in the networking industry like OpenFlow or NETCONF.
D. CORBA (Common Object Request Broker Architecture):
This is an older, complex middleware standard for building distributed applications. It is obsolete and not used as a southbound API in modern SDN architectures.
E. SC:
This is not a recognized API standard in this context. It could be a distractor or an acronym for something unrelated to southbound interfaces.
Reference:
ONF (Open Networking Foundation): Standardizes OpenFlow as a key southbound API.
IETF RFC 6241: Defines the NETCONF protocol, which has become the de facto standard for declarative configuration and is a critical southbound API in controller-based architectures like Cisco DNA Center.
Refer to the exhibit. 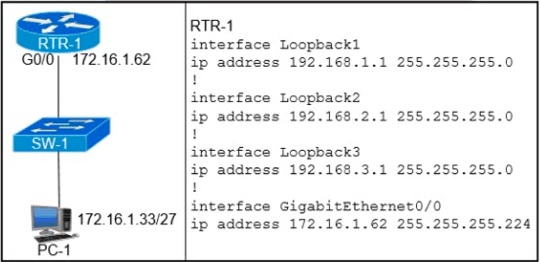 Which configuration on RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
Which configuration on RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
A. access-list 100 deny tcp host 172.16.1.33 any eq 22 access-list 100 permit ip any any interface GigabitEthernet0/0 ip access-group 100 in
B. access-list 100 deny tcp host 172.16.1.33 any eq 22 access-list 100 permit ip any any line vty 0 15 ip access-group 100 in
C. access-list 100 deny tcp host 172.16.1.33 any eq 23 access-list 100 permit ip any any interface GigabitEthernet0/0 ip access-group 100 in
D. access-list 100 deny tcp host 172.16.1.33 any eq 23 access-list 100 permit ip any any line vty 0 15 ip access-group 100 in
Explanation:
The task is to configure Router RTR-1 to deny SSH access from PC-1 (with IP address 172.16.1.33) to any interface on RTR-1 while allowing all other traffic. Let’s break this down step by step:
SSH and Port Number:
SSH (Secure Shell) uses TCP port 22 by default. To deny SSH access, the access control list (ACL) must block traffic from PC-1 to any destination using port 22.
ACL Application:
The ACL must be applied to the appropriate interface or line to enforce the restriction. Since the question specifies denying SSH access to "any RTR-1 interface," the ACL should typically be applied to the interface where traffic from PC-1 enters (e.g., GigabitEthernet0/0) or to the VTY lines if restricting remote access.
Allow All Other Traffic:
The ACL must include a permit statement (e.g., permit ip any any) to allow all other traffic, as ACLs have an implicit deny at the end.
Analysis of Options:
A. access-list 100 deny tcp host 172.16.1.33 any eq 22 access-list 100 permit ip any any interface GigabitEthernet0/0 ip access-group 100 in
The ACL denies TCP traffic from host 172.16.1.33 to any destination on port 22 (SSH).
The permit ip any any allows all other traffic.
The ACL is applied inbound on GigabitEthernet0/0, which is the interface connected to SW-1 (and thus PC-1). This effectively blocks SSH traffic from PC-1 to RTR-1’s interfaces while allowing other traffic.
Correct:
This configuration meets the requirement, assuming SSH access to RTR-1’s interfaces is initiated from PC-1 via this interface.
B. access-list 100 deny tcp host 172.16.1.33 any eq 22 access-list 100 permit ip any any line vty 0 15 ip access-group 100 in
The ACL denies TCP traffic from host 172.16.1.33 to any destination on port 22.
The permit ip any any allows all other traffic.
The ACL is applied to the VTY lines (0-15), which control remote access (e.g., Telnet or SSH) to the router.
Incorrect:
Applying the ACL to the VTY lines restricts SSH access to the router’s management plane (e.g., CLI access), but it does not block SSH to other interfaces or services on RTR-1. The question specifies denying SSH to "any RTR-1 interface," which implies broader interface-level control, not just VTY access.
C. access-list 100 deny tcp host 172.16.1.33 any eq 23 access-list 100 permit ip any any interface GigabitEthernet0/0 ip access-group 100 in
The ACL denies TCP traffic from host 172.16.1.33 to any destination on port 23 (Telnet, not SSH).
The permit ip any any allows all other traffic.
The ACL is applied inbound on GigabitEthernet0/0.
Incorrect:
Port 23 is for Telnet, not SSH (port 22). This configuration does not block SSH traffic, so it fails to meet the requirement.
D. access-list 100 deny tcp host 172.16.1.33 any eq 23 access-list 100 permit ip any any line vty 0 15 ip access-group 100 in
The ACL denies TCP traffic from host 172.16.1.33 to any destination on port 23 (Telnet).
The permit ip any any allows all other traffic.
The ACL is applied to the VTY lines (0-15).
Incorrect:
Similar to B, this restricts Telnet (not SSH) to the VTY lines and does not address SSH to RTR-1’s interfaces.
Why Option A is Correct:
The ACL correctly identifies SSH traffic (port 22) from PC-1 (172.16.1.33) and denies it.
Applying the ACL inbound on GigabitEthernet0/0 ensures that traffic entering RTR-1 from PC-1 is filtered, blocking SSH attempts to any interface on RTR-1.
The permit ip any any ensures all other traffic (e.g., HTTP, ICMP) is allowed, satisfying the "allows all other traffic" requirement.
Additional Consideration:
In a real-world scenario, if SSH is enabled on RTR-1’s VTY lines, applying the ACL only on GigabitEthernet0/0 might not block SSH if PC-1 initiates a session from a different path (e.g., another interface). However, based on the exhibit and the question’s focus on PC-1’s connection via GigabitEthernet0/0, Option A is the best fit. For complete SSH restriction, an ACL on VTY lines would complement this, but the question’s phrasing suggests interface-level filtering is sufficient.
Reference:
Cisco Official Documentation: Configuring IP Access Lists
CCNA 200-301 Official Cert Guide, Volume 1, by Wendell Odom: Chapter on Access Control Lists.
Which network action occurs within the data plane?
A. compare the destination IP address to the IP routing table.
B. run routing protocols (OSPF, EIGRP, RIP, BGP)
C. make a configuration change from an incoming NETCONF RPC
D. reply to an incoming ICMP echo request
Explanation:
In network devices (routers, switches), operations are divided into three logical planes:
Data Plane (Forwarding Plane):
Responsible for the actual task of forwarding user traffic based on decisions made by the control plane. It handles packets as they arrive, performs lookups (in tables built by the control plane), and switches them to the correct outgoing interface. The data plane is all about high-speed packet handling.
Control Plane:
Responsible for making decisions about how traffic should be routed. It runs routing protocols, builds routing tables, and manages other control functions.
Management Plane:
Handles the configuration, monitoring, and management of the device itself (e.g., SSH, SNMP, NETCONF).
Replying to an incoming ICMP echo request is a data plane function because it involves directly processing a user data packet and generating a response (an ICMP echo reply) that is sent back out a network interface. The router treats this like any other packet that needs to be processed and forwarded.
Why the other options are incorrect:
A. compare the destination IP address to the IP routing table:
This is a tricky one. The initial decision for a route is made by the control plane when it builds the routing table (FIB). However, the actual lookup for each individual packet is performed by the data plane using a pre-computed Forwarding Information Base (FIB). While the line can be blurry, the act of looking up a destination for a specific packet is considered a fundamental data plane task. However, the more definitive data plane action in this list is D. If this were a "choose one" question, D is the best answer.
B. run routing protocols (OSPF, EIGRP, RIP, BGP):
This is a classic control plane function. The router uses these protocols to learn routes and build its routing table.
C. make a configuration change from an incoming NETCONF RPC:
This is a management plane function. It involves changing the device's configuration, not forwarding user traffic.
Reference:
Cisco Architecture: The separation of the data, control, and management planes is a fundamental concept for understanding how network devices operate. The data plane's role is to forward traffic as quickly as possible using information provided by the control plane.
Which IPv6 address block sends packets to a group address rather than a single address?
A. 2000::/3
B. FC00::/7
C. FE80::/10
D. FF00::/8
Explanation:
The IPv6 address block FF00::/8 is reserved specifically for multicast addresses. A multicast address is used to identify a group of interfaces, typically on different nodes. A packet sent to a multicast address is delivered to every interface that is a member of that group.
The first 8 bits (one byte) of an IPv6 multicast address are always 1111 1111, which is FF in hexadecimal. This defines the entire FF00::/8 block.
Why the other options are incorrect:
A. 2000::/3:
This is the global unicast address block, equivalent to the public IPv4 addresses. Packets are sent to a single, unique address.
B. FC00::/7:
This is the unique local address (ULA) block, similar to the IPv4 private address ranges (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16). These are unicast addresses used for communication within a single site.
C. FE80::/10:
This is the link-local unicast address block. Every IPv6 interface automatically configures a link-local address in this range for communication on a single network segment. It is a unicast address.
Reference:
RFC 4291, IP Version 6 Addressing Architecture: This RFC formally defines the IPv6 addressing architecture and states: "Multicast addresses have the following format: | 8 bits | 4 bits | 4 bits | 112 bits | ... | FF | flags | scop | group ID | ..." This confirms that all multicast addresses start with FF.
Which two actions are performed by the Weighted Random Early Detection mechanism?
(Choose two)
A. It drops lower-priority packets before it drops higher-priority packets
B. It can identify different flows with a high level of granularity
C. It guarantees the delivery of high-priority packets
D. It can mitigate congestion by preventing the queue from filling up
E. it supports protocol discovery
Explanation:
Weighted Random Early Detection (WRED) is a congestion avoidance mechanism. Its primary goal is to prevent a network interface queue from becoming completely full, which leads to the problematic "tail drop" behavior where all new packets are dropped indiscriminately.
Here's how the correct actions are performed by WRED:
A. It drops lower-priority packets before it drops higher-priority packets:
This is the core of the "Weighted" aspect. WRED can be configured with different drop profiles based on the IP Precedence or DSCP value in a packet's header. Lower-priority traffic (e.g., web browsing) has a lower drop threshold, meaning WRED will begin randomly dropping these packets sooner (at a lower average queue depth) than it will for higher-priority traffic (e.g., voice). This provides a form of preferential treatment.
D. It can mitigate congestion by preventing the queue from filling up:
This is the core of the "Random Early Detection" aspect. Instead of waiting for the queue to be 100% full, WRED proactively starts to randomly drop packets as the average queue depth increases. This causes some TCP sessions to throttle back their transmission rates before a severe congestion event occurs, which helps keep the queue from ever filling completely and prevents global synchronization.
Why the other options are incorrect:
B. It can identify different flows with a high level of granularity:
This is incorrect. WRED operates on an aggregate level, making drop decisions based on the total queue depth and a packet's IP Precedence/DSCP mark. It does not identify or manage individual traffic flows (e.g., a specific TCP session between a client and a server). That is the function of a feature like NetFlow or specific queuing techniques.
C. It guarantees the delivery of high-priority packets:
This is false. WRED is a congestion avoidance mechanism, not a reservation mechanism. It makes it less likely that high-priority packets will be dropped compared to low-priority ones, but it does not guarantee their delivery. In a severe congestion scenario, even high-priority packets will be dropped once their specific threshold is exceeded.
E. it supports protocol discovery:
This is not a function of WRED. Protocol discovery is a feature associated with other technologies, such as Cisco's NBAR (Network-Based Application Recognition), which is used to identify the applications on the network.
Reference:
Cisco QoS Configuration Guide: The documentation for configuring WRED explicitly describes its behavior of using IP Precedence/DSCP for weighted drops and its role in managing queue depths to avoid tail drop.
Which attribute does a router use to select the best path when two or more different routes to the same destination exist from two different routing protocols.
A. dual algorithm
B. metric
C. administrative distance
D. hop count
Explanation:
When a router learns about the same destination network from two different routing protocols (e.g., OSPF and EIGRP), it must decide which route to place in its routing table. It makes this decision using a value called Administrative Distance (AD).
Administrative Distance (AD) is a measure of the trustworthiness of the source of the routing information. It is a number from 0 to 255, where a lower value is more trusted.
Since the routes are from different protocols, the router cannot compare their metrics (like OSPF cost vs. EIGRP composite metric) because they are calculated differently and are not comparable.
Therefore, the router selects the route with the lowest Administrative Distance.
Example:
A route learned from EIGRP has an AD of 90.
A route to the same network learned from OSPF has an AD of 110.
The router will select the EIGRP route and install it in the routing table because 90 is lower (more trustworthy) than 110.
Why the other options are incorrect:
A. dual algorithm:
The DUAL (Diffusing Update Algorithm) is the algorithm used specifically by EIGRP to select loop-free paths. It is not used to compare routes from different routing protocols.
B. metric:
A metric is a value used by a single routing protocol to determine the best path within that protocol. For example, OSPF uses cost, and RIP uses hop count. Metrics from different protocols are apples-to-oranges; they cannot be directly compared.
D. hop count:
This is the specific metric used by the RIP routing protocol. It is not used as a universal tie-breaker between different protocols.
Reference:
Cisco Routing Table Principles: One of the fundamental principles for building a routing table is that when multiple paths to the same destination exist, the path with the lowest Administrative Distance is preferred. This is a cornerstone of Cisco router operation. Default AD values are: Connected Interface=0, Static Route=1, EIGRP=90, OSPF=110, RIP=120.
What event has occurred if a router sends a notice level message to a syslog server?
A. A TCP connection has been torn down
B. An ICMP connection has been built
C. An interface line has changed status
D. A certificate has expired.
Explanation:
Syslog uses severity levels (also called notice levels) to categorize messages. A notice (level 5) message is a "normal but significant condition." It indicates an event that is not an error, but is important for logging the normal operation and state changes of the device.
An interface changing state (e.g., going from "down" to "up" or "up" to "down") is a classic example of a significant event that generates a notice-level syslog message. This allows a network administrator to track the stability and status of network links.
Why the other options are incorrect:
A. A TCP connection has been torn down:
While a router might log this event, it would typically be at a debug (level 7) severity because it is a very detailed, high-volume event related to a specific session, not a normal significant condition for the router itself.
B. An ICMP connection has been built:
ICMP is a connectionless protocol; there is no concept of "building a connection." An event like an ICMP echo (ping) might be logged at a debug level, but it is not a standard notice-level event.
D. A certificate has expired:
This is a much more critical event. A certificate expiration is a security and service-impacting issue and would be logged at a higher severity level, such as a warning (level 4) or error (level 3).
Reference:
Cisco Syslog Messages - Severity Levels: The notice level (5) is defined for significant but normal events. Interface status changes are one of the most common sources of these messages.
Common Practice: Monitoring systems are often configured to watch for interface "link up"/"link down" syslog messages, which are generated at the notice level, to automatically create and resolve network outage tickets.
Refer to the exhibit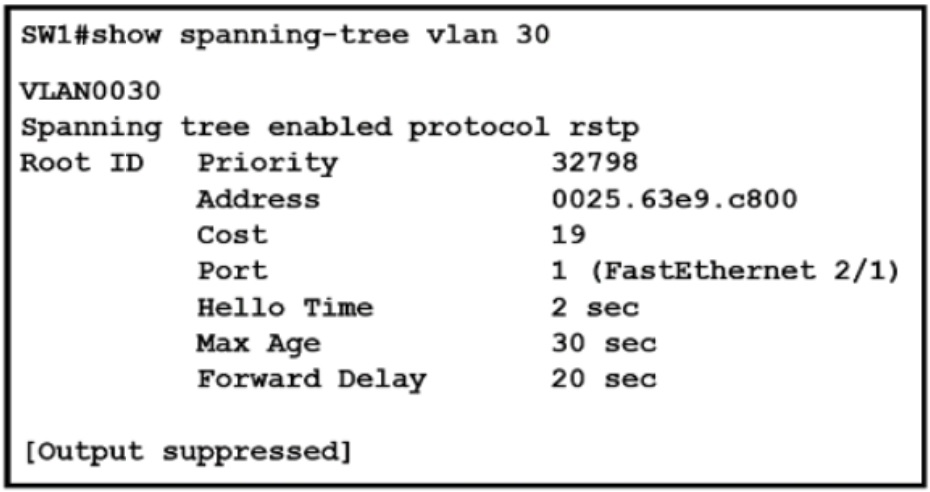
What two conclusions should be made about this configuration? (Choose two )
A. The designated port is FastEthernet 2/1
B. This is a root bridge
C. The spanning-tree mode is Rapid PVST+
D. The spanning-tree mode is PVST+
E. The root port is FastEthernet 2/1
Explanation:
Let's analyze the provided show spanning-tree output step by step.
1. Identify the Spanning-Tree Mode (Option C vs. D)
The output clearly states: Spanning tree enabled protocol rstp.
RSTP (Rapid Spanning Tree Protocol) is the underlying protocol.
When RSTP is used on a Cisco switch in a per-VLAN context, the mode is called Rapid PVST+ (Per-VLAN Rapid Spanning Tree Plus).
Therefore, C. The spanning-tree mode is Rapid PVST+ is correct, and D is incorrect.
2. Determine if this is the Root Bridge (Option B)
The "Root ID" section displays the characteristics of the root bridge for VLAN 30.
The Root ID's MAC address is 0025.63e9.c800.
If this switch (SW1) were the root bridge, the Root ID would match this switch's own Bridge ID. There is no information provided about this switch's own Bridge ID, but a key giveaway is the "Cost" and "Port" fields. A root bridge would list its own paths with a cost of 0 and no root port. Here, it has a path to the root with a cost of 19 via port Fa2/1. This definitively proves this switch is not the root bridge.
Therefore, B. This is a root bridge is incorrect.
3. Identify the Root Port and Designated Port (Options A and E)
The Root Port is the port on a non-root bridge that has the best path to the root bridge. The output explicitly states this under the Root ID section: Port 1 (FastEthernet 2/1). This means Fa2/1 is the root port for VLAN 30 on this switch.
Therefore, E. The root port is FastEthernet 2/1 is correct.
A Designated Port is the port on a segment that is responsible for forwarding traffic towards the root bridge. Each network segment has one designated port. Since Fa2/1 on this switch is a root port (receiving the best BPDU), it cannot be the designated port for its segment. The designated port for the segment connected to Fa2/1 must be on the other end of that link (the upstream switch).
Therefore, A. The designated port is FastEthernet 2/1 is incorrect.
Summary of Correct Answers:
C. The protocol is rstp, which means the mode is Rapid PVST+.
E. The output lists Fa2/1 as the port leading to the root, making it the root port.
Reference:
Cisco IOS Command Reference: The show spanning-tree command output is interpreted as described. The "Root ID" section describes the root bridge, not the local switch. The port listed there is the local switch's root port.
Which state does the switch port move to when PortFast is enabled?
A. learning
B. forwarding
C. blocking
D. listening
In which situation is private IPv4 addressing appropriate for a new subnet on the network of an organization?
A. There is limited unique address space, and traffic on the new subnet will stay local within the organization
B. The network has multiple endpoint listeners, and it is desired to limit the number of broadcasts.
C. Traffic on the subnet must traverse a site-to-site VPN to an outside organization.
D. The ISP requires the new subnet to be advertised to the internet for web services.
Aside from discarding, which two states does the switch port transition through while using RSTP (802.1w)? (Choose two)
A. listening
B. blocking
C. forwarding
D. learning
E. speaking
How will Link Aggregation be Implemented on a Cisco Wireless LAN Controller?
A. One functional physical port is needed to pass client traffic
B. The EthernetChannel must be configured in "mode active".
C. When enabled, the WLC bandwidth drops to 500 Mbps.
D. To pass client traffic, two or more ports must be configured.
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-5/configurationguide/ b_cg75/b_cg75_chapter_0100010.html
| Page 2 out of 72 Pages |
| Previous |