Topic 1: Exam Pool A
desc about topic
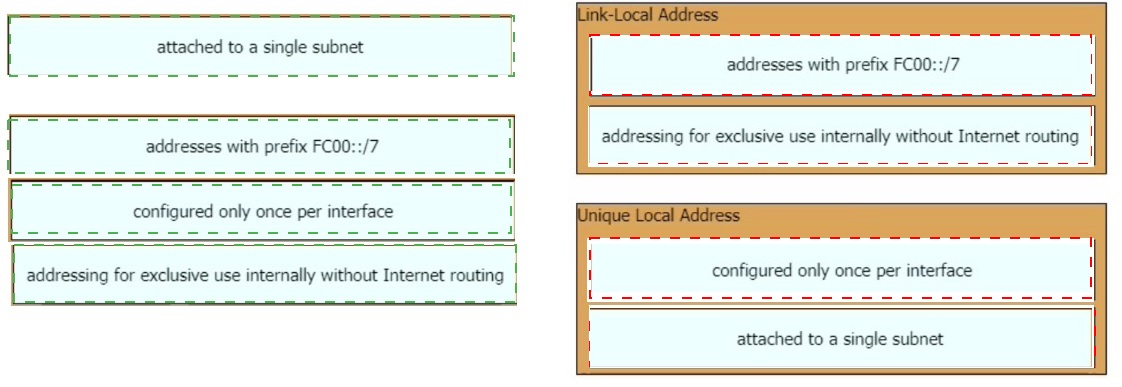
Drag and drop the IPv6 address type characteristics from the left to the right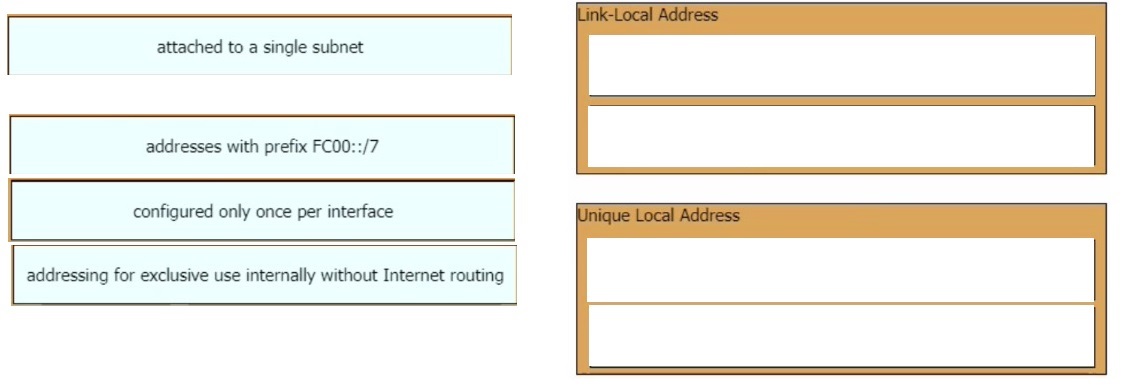
What is the difference in data transmission delivery and reliability between TCP and UDP?
A. TCP transmits data at a higher rate and ensures packet delivery. UDP retransmits lost data to ensure applications receive the data on the remote end.
B. UDP sets up a connection between both devices before transmitting data. TCP uses the three-way handshake to transmit data with a reliable connection.
C. UDP is used for multicast and broadcast communication. TCP is used for unicast communication and transmits data at a higher rate with error checking.
D. TCP requires the connection to be established before transmitting data. UDP transmits data at a higher rate without ensuring packet delivery
Which two components are needed to create an Ansible script that configures a VLAN on a switch? (Choose two.)
A. cookbook
B. task
C. playbook
D. model
E. recipe
How do TCP and UDP differ in the way they provide reliability for delivery of packets?
A. TCP is a connectionless protocol that does not provide reliable delivery of data, UDP is a connection-oriented protocol that uses sequencing to provide reliable delivery.
B. TCP does not guarantee delivery or error checking to ensure that there is no corruption of data UDP provides message acknowledgement and retransmits data if lost.
C. TCP provides flow control to avoid overwhelming a receiver by sending too many packets at once, UDP sends packets to the receiver in a continuous stream without checking for sequencing
D. TCP uses windowing to deliver packets reliably; UDP provides reliable message transfer between hosts by establishing a three-way handshake
What does physical access control regulate?
A. access to spec fie networks based on business function
B. access to servers to prevent malicious activity
C. access :o computer networks and file systems
D. access to networking equipment and facilities
Refer to the exhibit.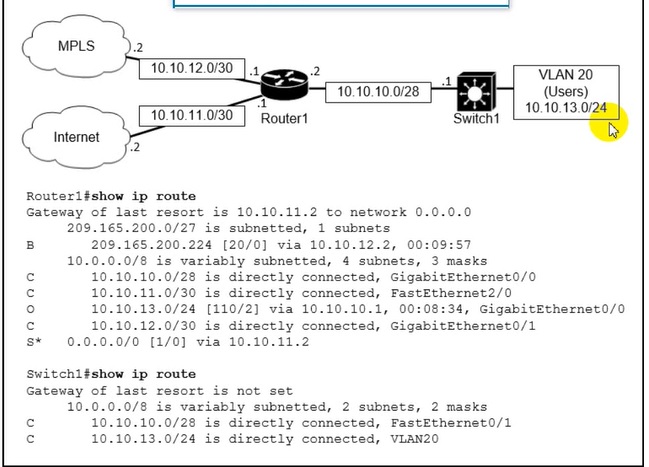
which path is used by the router for internet traffic ?
A. 209.165.200.0/27
B. 10.10.10.0/28
C. 0.0.0.0/0
D. 10.10.13.0/24
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
A. platform-as-a-service
B. software-as-a-service
C. network-as-a-service
D. infrastructure-as-a-service
Which level of severity must be set to get informational syslogs?
A. alert
B. critical
C. notice
D. debug
What are two characteristics of the distribution layer in a three-tier network architecture? (Choose two.)
A. serves as the network aggregation point
B. provides a boundary between Layer 2 and Layer 3 communications
C. designed to meet continuous, redundant uptime requirements
D. is the backbone for the network topology
E. physical connection point for a LAN printer
A network analyst is tasked with configured the date and time on a router using EXEC mode. The date must be set to 12:00am. Which command should be used?
A. Clock timezone
B. Clock summer-time-recurring
C. Clock summer-time date
D. Clock set
Which network allows devices to communicate without the need to access the Internet?
A. 1729.0.0/16
B. 172.28.0.0/16
C. 192.0.0.0/8
D. 209.165.201.0/24
Explanation:
The private ranges of each class of IPv4 are listed below:
Class A private IP address ranges from 10.0.0.0 to 10.255.255.255 Class B private IP address ranges from 172.16.0.0 to 172.31.255.255 Class C private IP address ranges from 192.168.0.0 to 192.168.255.255 Only the network 172.28.0.0/16 belongs to the private IP address (of class B)
What mechanism carries multicast traffic between remote sites and supports encryption?
A. ISATAP
B. GRE over iPsec
C. iPsec over ISATAP
D. GRE
| Page 16 out of 72 Pages |
| Previous |