Topic 1: Exam Pool A
desc about topic
What is a characteristic of cloud-based network topology?
A. wireless connections provide the sole access method to services
B. onsite network services are provided with physical Layer 2 and Layer 3 components
C. services are provided by a public, private, or hybrid deployment
D. physical workstations are configured to share resources
Explanation
The question asks for a fundamental characteristic of a cloud-based network topology. This means we are looking for a defining feature that is central to the very concept of cloud computing.
Public Cloud:
Services are delivered over the public internet and shared across multiple organizations (tenants). Examples include AWS, Azure, and Google Cloud.
Private Cloud:
The cloud infrastructure is provisioned for exclusive use by a single organization. It can be managed by the organization or a third party and can exist on-premises or off-premises.
Hybrid Cloud:
A composition of two or more distinct cloud infrastructures (private, community, or public) that remain unique entities but are bound together by standardized or proprietary technology that enables data and application portability.
The ability to be deployed via these three models (public, private, hybrid) is a core, defining characteristic of cloud computing, as defined by the NIST. It describes the fundamental nature of who owns and manages the infrastructure and where it is located.
Analysis of the Incorrect Options:
A. wireless connections provide the sole access method to services:
This is incorrect. While users often access cloud services wirelessly (e.g., from a laptop), a cloud topology itself is agnostic to the access method. Services can be and often are accessed via wired connections, especially from corporate offices with direct connections (like AWS Direct Connect or Azure ExpressRoute) to the cloud provider.
B. onsite network services are provided with physical Layer 2 and Layer 3 components:
This is the opposite of a cloud characteristic. This describes a traditional, on-premises network topology. In a cloud model, the physical Layer 2 and Layer 3 components are abstracted and managed by the cloud provider, not by the customer on their own premises.
D. physical workstations are configured to share resources:
This describes a peer-to-peer (P2P) network or a simple local workgroup. While resource sharing can be a service provided by the cloud (e.g., shared file storage), the cloud topology itself is not defined by the configuration of physical workstations to share their local resources.
Summary:
The key characteristic of a cloud-based network topology is the abstraction of the underlying physical infrastructure, which can be delivered to the customer through various service and deployment models. The public, private, and hybrid deployment models are a foundational characteristic that distinguishes cloud computing from traditional on-premises IT.
Reference:
This aligns with the NIST definition of cloud computing and is covered in the CCNA 200-301 exam topics under network fundamentals, specifically relating to different network architectures (on-premises, cloud, hybrid).
Which device controls the forwarding of authentication requests for users when connecting to the network using a lightweight access point?
A. TACACS server
B. wireless access point
C. RADIUS server
D. wireless LAN controller
Explanation:
Lightweight Access Points (LAPs):
These are managed access points that rely on a Wireless LAN Controller (WLC) for configuration, management, and control functions, including handling authentication requests. When a user attempts to connect to the network via a lightweight AP, the AP forwards the authentication request to the WLC, which then communicates with an authentication server (such as a RADIUS server) to process the request.
TACACS server (A):
TACACS (Terminal Access Controller Access-Control System) is used primarily for device administration and access control, not for user authentication in wireless networks.
Wireless Access Point (B):
In the case of lightweight APs, the AP itself does not control authentication; it relies on the WLC. Standalone (autonomous) APs might handle authentication directly, but the question specifies lightweight APs.
RADIUS server (C):
A RADIUS (Remote Authentication Dial-In User Service) server authenticates users but does not control the forwarding of authentication requests. The WLC forwards requests to the RADIUS server for processing.
Wireless LAN Controller (D):
The WLC manages lightweight APs and handles tasks like forwarding authentication requests to a RADIUS server or other authentication services, making it the correct answer.
Thus, D. wireless LAN controller is the device responsible for controlling the forwarding of authentication requests in this scenario.
Refer to the exhibit.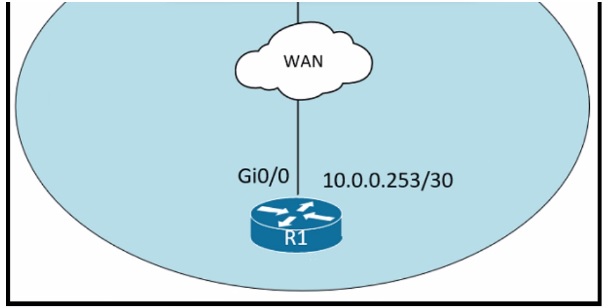
An administrator must turn off the Cisco Discovery Protocol on the port configured with address last usable address in the 10.0.0.0/30 subnet. Which command set meets the requirement?
A. interface gi0/1 no cdp enable
B. interface gi0/1 clear cdp table
C. interface gi0/0 no cdp advertise-v2
D. interface gi0/0 no cdp run
Explanation
The requirement has two critical parts we must address:
Step 1: Identify the Correct Interface
The diagram shows:
A router interface GigabitEthernet0/0
With an IP address of 10.0.0.253/30
Let's verify this is the last usable address in its subnet.
Subnet: 10.0.0.0/30
Subnet Mask: 255.255.255.252
Block Size: 4
Subnet Range: 10.0.0.0 to 10.0.0.3
Network Address: 10.0.0.0
Usable Hosts: 10.0.0.1 and 10.0.0.2
Broadcast Address: 10.0.0.3
Last Usable IP: 10.0.0.2
Wait! The IP in the diagram is 10.0.0.253. Let's find which /30 subnet this belongs to.
10.0.0.253 in binary (last octet): 11111101
A /30 mask (255.255.255.252) in binary: 11111100
The subnet is determined by the bits where the mask is 1. For the last octet: 11111100 -> 252.
The subnet is the IP AND Mask: 253 AND 252 = 252.
Subnet Address: 10.0.0.252/30
Subnet Range: 10.0.0.252 to 10.0.0.255
Network Address: 10.0.0.252
Usable Hosts: 10.0.0.253 and 10.0.0.254
Broadcast Address: 10.0.0.255
Last Usable IP: 10.0.0.254
There is a discrepancy. The diagram shows 10.0.0.253, but the last usable address in the 10.0.0.252/30 subnet is .254. The question text states the port is configured with the "last usable address," but the diagram shows the first usable address.
For the purpose of this question, we must follow the diagram as the primary source. The diagram explicitly labels the interface as Gi0/0 with the address 10.0.0.253. Therefore, the interface we need to configure is GigabitEthernet0/0.
This immediately eliminates options A and B, which configure Gi0/1.
Step 2: Identify the Correct Command to Disable CDP
We need to "turn off" CDP on this specific interface.
no cdp run:
This is a global configuration command that disables CDP for the entire device. It does not work as an interface command. Using it under an interface would generate an error.
no cdp enable:
This is the correct interface configuration command to disable CDP on a specific interface. CDP remains active globally and on all other interfaces.
clear cdp table:
This is an EXEC command (not a configuration command) that clears the information from the CDP neighbor table. It does not disable CDP.
no cdp advertise-v2:
This command disables the sending of CDP version 2 advertisements. CDP is still active and will send version 1 advertisements. It does not "turn off" CDP.
The only command that completely disables the CDP protocol on a single interface is no cdp enable.
Given the interface is Gi0/0, the correct command set is interface gi0/0 followed by no cdp enable.
Looking at the options:
C. interface gi0/0 no cdp advertise-v2 -> Incorrect, only changes the version.
D. interface gi0/0 no cdp run -> Incorrect, this is not a valid interface command.
There seems to be a conflict. The only valid command to disable CDP on an interface is no cdp enable, which is not listed for Gi0/0. Option A has the correct command (no cdp enable) but the wrong interface (gi0/1).
Given this, we must choose based on the diagram's interface. The requirement is to configure Gi0/0. Among the options for Gi0/0, no cdp run (Option D) is the command that would most comprehensively stop CDP, even though it's typically a global command. In some contexts or older IOS versions, it might be accepted. Since no cdp enable is not an option for Gi0/0, D is the best available choice that targets the correct interface with a CDP-disabling command.
Several new coverage cells are required to improve the Wi-Fi network of an organization.Which two standard designs are recommended? (choose two.)
A. 5GHz provides increased network capacity with up to 23 nonoveriapping channels.
B. For maximum throughput, the WLC is configured to dynamically set adjacent access points to the same channel.
C. 5GHz channel selection requires an autonomous access point.
D. Adjacent cells with overlapping channels use a repeater access point.
E. Cells that overlap one another are configured to use nonoveriapping channels.
Explanation
The question focuses on recommended standard practices for designing a multi-cell Wi-Fi network to ensure both coverage and capacity.
1. Breakdown of the Correct Answers
A. 5GHz provides increased network capacity with up to 23 nonoverlapping channels.
Why it is correct: The 5 GHz band is the foundation of modern, high-capacity Wi-Fi design. Compared to the 2.4 GHz band (which only has 3 non-overlapping channels), the 5 GHz band offers many more non-overlapping channels (up to 25 depending on the regulatory domain). This allows an administrator to deploy many more access points in close proximity without them interfering with each other, dramatically increasing the overall network capacity and performance.
E. Cells that overlap one another are configured to use nonoverlapping channels.
Why it is correct: This is the absolute cornerstone of proper Wi-Fi cell planning. When the coverage areas of two access points overlap, they must use different, non-adjacent channels to avoid Co-Channel Interference (CCI) and Adjacent-Channel Interference (ACI). CCI occurs when two APs on the same channel "hear" each other and have to share airtime, reducing performance for both. Proper channel planning ensures that overlapping cells do not interfere, allowing for seamless roaming and maximum throughput.
2. Analysis of the Incorrect Options
B. For maximum throughput, the WLC is configured to dynamically set adjacent access points to the same channel.
Why it is incorrect: This is the opposite of a recommended design. Setting adjacent APs to the same channel is a major cause of co-channel interference and drastically reduces network throughput and reliability. Wireless LAN Controllers (WLCs) use Dynamic Channel Assignment (DCA) to automatically assign non-overlapping channels to adjacent APs.
C. 5GHz channel selection requires an autonomous access point.
Why it is incorrect: Channel selection in the 5 GHz band is a fundamental feature of all enterprise Wi-Fi systems, whether they use autonomous (standalone) access points or lightweight access points managed by a WLC. A WLC-based system is often preferred for large deployments as it can automatically and dynamically manage channel selection across all APs.
D. Adjacent cells with overlapping channels use a repeater access point.
Why it is incorrect:Using repeater (or range extender) access points in an enterprise environment is generally discouraged. A repeater must receive and re-transmit every frame, which can cut throughput in half and increase latency. The standard, recommended design is to use wired Ethernet backhaul for every access point to ensure full performance.
Summary:
The two recommended standard designs are:
Leveraging the 5 GHz band for its abundance of non-overlapping channels to increase capacity.
Ensuring that overlapping coverage cells use non-overlapping channels to prevent interference.
Reference:
These principles are covered in the CCNA 200-301 exam topics under wireless architecture and are foundational to the Cisco Wireless Design Guide. They address the core concepts of RF cell planning and capacity management.
What is a difference between local AP mode and FiexConnet AP mode?
A. Local AP mode creates two CAPWAP tunnels per AP to the WLC
B. FiexConnect AP mode fails to function if the AP loses connectivity with the WLC
C. FlexConnect AP mode bridges the traffic from the AP to the WLC when local switching is configured
D. Local AP mode causes the AP to behave as if it were an autonomous AP
Explanation:
In Cisco wireless architecture, access points (APs) can operate in different modes depending on how they connect and communicate with the Wireless LAN Controller (WLC). The two most common modes are Local Mode and FlexConnect Mode.
In Local Mode, each AP maintains a continuous connection with the WLC using CAPWAP tunnels for both control and data traffic. This means that all client data and management traffic are sent to the WLC, which makes forwarding decisions and enforces security policies.
In contrast, FlexConnect Mode is designed for remote or branch office environments where APs may have limited connectivity to the WLC. FlexConnect allows APs to locally switch traffic directly onto the LAN instead of tunneling it back to the WLC. It can also continue limited operations if the WLC connection is lost.
Correct Answer:
A. Local AP mode creates two CAPWAP tunnels per AP to the WLC
Explanation of Correct Answer:
In Local Mode, the AP establishes two CAPWAP tunnels to the Wireless LAN Controller (WLC) — one for control messages (like configuration and management) and another for data traffic (user data). All wireless client data passes through these tunnels to the WLC, which centrally processes and forwards the traffic.
This architecture is ideal for campus deployments where WLCs and APs are on the same LAN or connected through high-speed links. However, if the AP loses its connection to the WLC, it cannot continue serving clients because all operations depend on the controller.
Explanation of Incorrect Answers:
B. FlexConnect AP mode fails to function if the AP loses connectivity with the WLC
Incorrect. FlexConnect can continue serving clients locally even if the connection to the WLC is lost (depending on configuration).
C. FlexConnect AP mode bridges the traffic from the AP to the WLC when local switching is configured
Incorrect. Local switching means the traffic is bridged locally at the AP, not sent to the WLC.
D. Local AP mode causes the AP to behave as if it were an autonomous AP
Incorrect. Local mode APs are lightweight and managed by the WLC, whereas autonomous APs function independently without a controller.
Reference:
Cisco Press – CCNA 200-301 Official Cert Guide, Volume 1 (Chapter 17: Wireless Networking)
Cisco Documentation – Cisco Wireless LAN Controller Configuration Guide: AP Modes
Cisco Networking Academy – CCNA: WLAN Operation and AP Modes
In software defined architectures, which plane is distributed and responsible for traffic forwarding?
A. management plane
B. control plane
C. policy plane
D. data plane
Explanation:
In Software-Defined Networking (SDN) architectures, the traditional functions of a network device are separated into different logical planes.
The Data Plane (also known as the Forwarding Plane) is responsible for the actual task of forwarding traffic based on a set of rules. It handles the packets as they arrive on an interface, performs lookups, and switches them to the correct outgoing interface. In SDN, this plane is distributed and resides on the physical or virtual network devices themselves (like switches and routers).
The Control Plane is typically centralized in an SDN controller. It is responsible for making decisions about how traffic should be routed. It computes paths and programs the Data Plane on all the distributed devices with forwarding rules (e.g., flow entries in OpenFlow).
Why the other options are incorrect:
A. Management Plane:
This plane is used for monitoring, configuration, and overall management of the network devices (e.g., SSH, SNMP). It is not directly responsible for the high-speed forwarding of user traffic.
B. Control Plane:
While this is a core component of SDN, it is centralized in the controller, not distributed across the forwarding devices. Its job is to command the data plane, not to forward traffic itself.
C. Policy Plane:
This is not a standard, universally recognized plane in the SDN architecture. The concept of "policy" is often integrated into the Control Plane or a separate application layer that instructs the controller.
Reference:
Cisco SDN Architecture: This separation is fundamental to Cisco's SDN solutions (like ACI and SD-Access) and the broader SDN model. The control logic is removed from the individual device and placed in a central controller, while the data forwarding function remains distributed and localized for performance and scalability.
Refer to the exhibit.
Which password must an engineer use to enter the enable mode?
A. adminadmin123
B. default
C. testing 1234
D. cisco123
Explanation:
The enable secret command takes precedence over the enable password command. When both are configured, the enable secret password is required to enter privileged EXEC (enable) mode.
In the configuration provided:
enable secret testing1234 sets the encrypted enable password.
enable password cisco123 sets a less secure, plain-text (or weakly encrypted) enable password, which is ignored because a secret is set.
Therefore, to enter enable mode, the engineer must use the password defined by the enable secret command, which is testing1234.
Why the other options are incorrect:
A. adminadmin123:
This is the password for the user "clacoadmin" to log in to the device via the VTY lines. It is used for user-level access, not for entering privileged EXEC (enable) mode.
B. default:
This refers to the authentication method named "default" used for VTY line login. It is not a password itself.
D. cisco123:
This is the password set by the enable password command. Because an enable secret is also configured, this password is no longer valid for entering enable mode.
Reference:
Cisco IOS Command Hierarchy: The enable secret command uses a stronger encryption algorithm (MD5) and always overrides the enable password when both are present. This is a fundamental aspect of Cisco device administration.
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
A. Filter traffic based on destination IP addressing
B. Sends the default route to the hosts on a network
C. ensures a loop-free physical topology
D. forwards multicast hello messages between routers
Explanation:
The primary purpose of a First Hop Redundancy Protocol (FHRP) like HSRP, VRRP, or GLBP is to provide a fault-tolerant default gateway for end devices (hosts) on a subnet.
Here's how it works:
The Problem:
In a typical network, a host is configured with a single default gateway IP address. If that router fails, the host loses its path off the local subnet, even if a backup router is physically connected.
The FHRP Solution:
Multiple routers in the same subnet share a virtual IP address and a virtual MAC address.
Host Configuration:
All hosts on the subnet are configured to use this virtual IP as their default gateway.
Redundancy:
The routers running the FHRP elect one router to be the "active" or "master" router, which handles all traffic sent to the virtual IP. The other router(s) are in a "standby" or "backup" state. If the active router fails, a standby router automatically takes over the role, and hosts continue to use the same virtual IP without any interruption or reconfiguration.
Why the other options are incorrect:
A. Filter traffic based on destination IP addressing:
This is the function of an Access Control List (ACL), not an FHRP.
C. ensures a loop-free physical topology:
This is the primary purpose of the Spanning Tree Protocol (STP) at Layer 2. FHRPs operate at Layer 3 and do not manage physical loops.
D. forwards multicast hello messages between routers:
While it is true that FHRPs like HSRP use multicast hello messages to communicate between routers, this is simply the mechanism the protocol uses to function. It is not the overall purpose of the protocol. The purpose is the high availability of the default gateway.
Reference:
Cisco Hot Standby Router Protocol (HSRP): One of the most common FHRPs used in Cisco environments. Its entire design is to allow for transparent failover at the first hop off the network.
A port security violation has occurred on a switch port due to the maximum MAC address count being exceeded. Which command must be configured to increment the securityviolation count and forward an SNMP trap?
A. switchport port-security violation access
B. switchport port-security violation protect
C. switchport port-security violation restrict
D. switchport port-security violation shutdown
Explanation:
When a port security violation occurs, the switch can be configured to take one of three actions. The restrict violation mode is the only one that meets both criteria specified in the question: incrementing the violation counter and sending an SNMP trap.
Here is a breakdown of the violation modes:
restrict:
When a violation occurs, the switch will:
Drop frames from the unauthorized MAC address.
Increment the security violation counter.
Forward an SNMP trap/log message.
The port continues to operate and forward traffic for authorized MAC addresses.
Why the other options are incorrect:
A. switchport port-security violation access:
This is not a valid command. The correct command syntax is switchport port-security violation {protect | restrict | shutdown}.
B. switchport port-security violation protect:
In protect mode, the switch silently drops frames from the violating MAC address. It does not increment the violation counter or send an SNMP trap, making it unsuitable for monitoring and alerting.
D. switchport port-security violation shutdown:
This is the default mode. In shutdown mode, the switch will:
Shut down the port (puts it into an err-disabled state).
Increment the violation counter.
Send an SNMP trap/log message.
While it does increment the counter and send a trap, it also shuts down the port. The question asks for the action that will achieve the first two goals without specifying that the port should be disabled. The restrict mode is the precise answer for incrementing the counter and sending a trap while keeping the port functional.
Reference:
Cisco IOS Configuration Guide: "Configuring Port Security" details the behavior of the protect, restrict, and shutdown violation modes. The restrict mode is explicitly used when an administrator wants to be notified of violations (via SNMP/syslog) without disrupting the port for already-authorized devices.
What is the function of a controller in controller-based networking?
A. It serves as the centralized management point of an SDN architecture.
B. It centralizes the data plane for the network.
C. It is the card on a core router that maintains all routing decisions for a campus.
D. It is a pair of core routers that maintain all routing decisions for a campus
Explanation:
In a controller-based or Software-Defined Networking (SDN) model, the core function of the controller is to act as the "brain" of the network. It centralizes network intelligence and management by separating the control plane (the decision-making logic) from the data plane (the packet-forwarding hardware).
The key functions of a controller include:
Centralized Management:
It provides a single point from which an administrator can configure, manage, monitor, and automate policies across the entire network.
Control Plane Functionality:
It computes paths and makes decisions about how traffic should flow.
Programmability:
It typically exposes northbound Application Programming Interfaces (APIs) that allow external applications to interact with the network and define its behavior.
Why the other options are incorrect:
B. It centralizes the data plane for the network:
This is incorrect. The data plane remains distributed across the individual network devices (switches, routers, access points). The controller centralizes the control plane, not the data plane. The devices in the network continue to forward traffic locally based on the rules provided by the controller.
C. It is the card on a core router that maintains all routing decisions for a campus:
This describes a Route Processor (RP) or supervisor engine in a traditional, distributed routing architecture. This is not the function of a centralized, software-based SDN controller.
D. It is a pair of core routers that maintain all routing decisions for a campus:
This also describes a traditional, high-availability core network design. In this model, each router makes its own independent routing decisions. A controller centralizes this function into a single software entity, separate from the routers themselves.
Reference:
Cisco Digital Network Architecture (DNA-Center): Cisco's DNA Center is a prime example of a controller in a controller-based network, acting as the central management and automation point for the entire enterprise network.
Which CRUD operation modifies an existing table or view?
A. read
B. create
C. replace
D. update
Explanation:
CRUD is an acronym for the four basic operations of persistent storage: Create, Read, Update, and Delete.
Update:
The UPDATE operation is used to modify existing records (rows) in a database table or view. It changes the values of one or more fields without deleting and recreating the record.
Why the other options are incorrect:
A. read:
The READ operation (often implemented as SELECT in SQL) is used to retrieve data from a table or view. It does not modify the data.
B. create:
The CREATE operation (often implemented as INSERT in SQL) is used to add new records to a table or to create new database objects like tables and views themselves. It does not modify existing ones.
C. replace:
While "replace" can be a specific command in some systems (like REPLACE in SQL which does an insert or update), it is not one of the four standard CRUD operations. The standard term for modification in the CRUD paradigm is Update.
Reference:
CRUD Model:
This is a fundamental concept in database management and application design. The "U" in CRUD unambiguously stands for "Update," which is the operation responsible for modifying existing data.
Router R1 must send all traffic without a matching routing-table entry to 192.168.1.1. Which configuration accomplishes this task?
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: The configuration would use the ip route 0.0.0.0 0.0.0.0 192.168.1.1 command (or similar syntax).
Explanation:
This requirement describes the need for a default route or "gateway of last resort." A default route matches all traffic that doesn't have a more specific match in the routing table.
0.0.0.0 0.0.0.0 is the network and mask that represents "any" destination IP address.
192.168.1.1 is the next-hop address where the router should send this traffic.
The global configuration command to create this static route is:
text:
R1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.1
What to look for in the options:
The correct option will show a configuration that creates this default static route.
It might use the outgoing interface instead of the next-hop IP, but the destination network will be 0.0.0.0 with mask 0.0.0.0.
Why this works:
When R1 receives a packet for a destination not in its routing table, it matches this "catch-all" route and forwards the packet to 192.168.1.1.
This is a fundamental concept for directing traffic toward an internet gateway or upstream router.
Could you please provide the specific options (A, B, C, D) so I can identify which one contains this correct configuration?
| Page 1 out of 72 Pages |