An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.
Which obfuscation technique is the attacker using?
A.
Base64 encoding
B.
transport layer security encryption
C.
SHA-256 hashing
D.
ROT13 encryption
transport layer security encryption
Which event artifact is used to identify HTTP GET requests for a specific file?
A.
destination IP address
B.
URI
C.
HTTP status code
D.
TCP ACK
URI
Refer to the exhibit.
Which application protocol is in this PCAP file?
A.
SSH
B.
TCP
C.
TLS
D.
HTTP
TCP
Refer to the exhibit.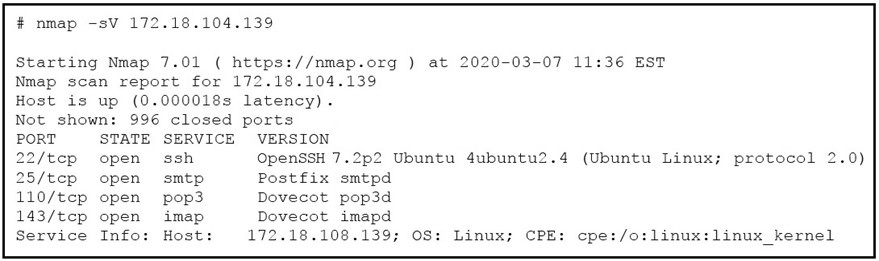 What does the output indicate about the server with the IP address 172.18.104.139?
What does the output indicate about the server with the IP address 172.18.104.139?
A.
open ports of a web server
B.
open port of an FTP server
C.
open ports of an email server
D.
running processes of the server
open ports of an email server
Refer to the exhibit.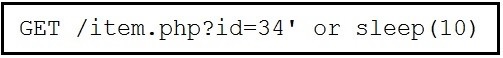
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
A.
parameter manipulation
B.
heap memory corruption
C.
command injection
D.
blind SQL injection
blind SQL injection
Which system monitors local system operation and local network access for violations of a
security policy?
A.
host-based intrusion detection
B.
systems-based sandboxing
C.
host-based firewall
D.
antivirus
host-based firewall
Which step in the incident response process researches an attacking host through logs in a SIEM?
A.
detection and analysis
B.
preparation
C.
eradication
D.
containment
detection and analysis
What are two social engineering techniques? (Choose two.)
A.
privilege escalation
B.
DDoS attack
C.
phishing
D.
man-in-the-middle
E.
pharming
phishing
pharming
What is an attack surface as compared to a vulnerability?
A.
any potential danger to an asset
B.
the sum of all paths for data into and out of the application
C.
an exploitable weakness in a system or its design
D.
the individuals who perform an attack
the sum of all paths for data into and out of the application
An intruder attempted malicious activity and exchanged emails with a user and received
corporate information, including email distribution lists. The intruder asked the user to
engage with a link in an email. When the fink launched, it infected machines and the
intruder was able to access the corporate network.
Which testing method did the intruder use?
A.
social engineering
B.
eavesdropping
C.
piggybacking
D.
tailgating
social engineering
Which signature impacts network traffic by causing legitimate traffic to be blocked?
A.
false negative
B.
true positive
C.
true negative
D.
false positive
false positive
Which type of data consists of connection level, application-specific records generated from network traffic?
A.
transaction data
B.
location data
C.
statistical data
D.
alert data
transaction data
| Page 8 out of 34 Pages |
| Previous |