Which type of data collection requires the largest amount of storage space?
A.
alert data
B.
transaction data
C.
session data
D.
full packet capture
full packet capture
Which action prevents buffer overflow attacks?
A.
variable randomization
B.
using web based applications
C.
input sanitization
D.
using a Linux operating system
input sanitization
Refer to the exhibit
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been
downloaded from an email. What is the state of this file?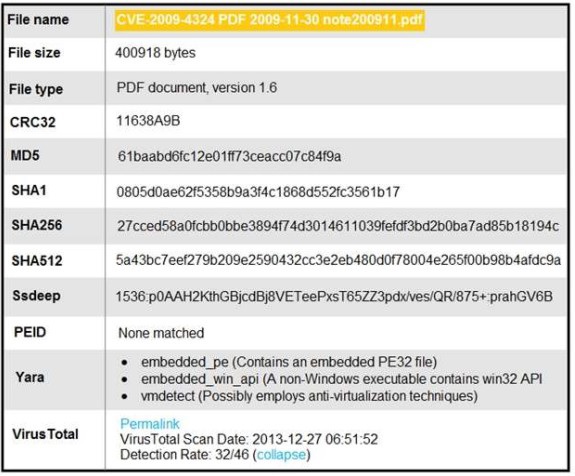
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
file has an embedded Windows 32 executable and the Yara field lists suspicious
features for further
analysis.
How does an attacker observe network traffic exchanged between two users?
A.
port scanning
B.
man-in-the-middle
C.
command injection
D.
denial of service
man-in-the-middle
What makes HTTPS traffic difficult to monitor?
A.
SSL interception
B.
packet header size
C.
Cs
D.
encryption
encryption
Refer to the exhibit.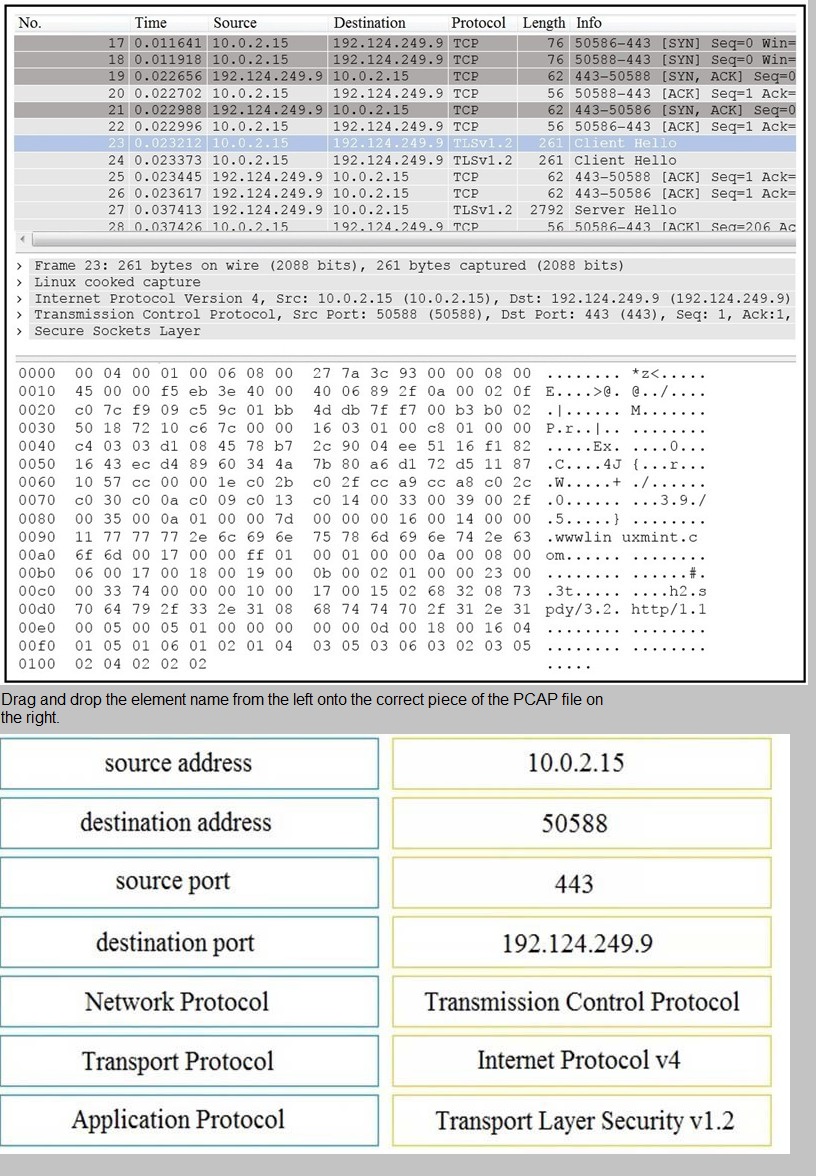
Which regex matches only on all lowercase letters?
A.
[az]+
B.
[^az]+
C.
az+
D.
a*z+
[az]+
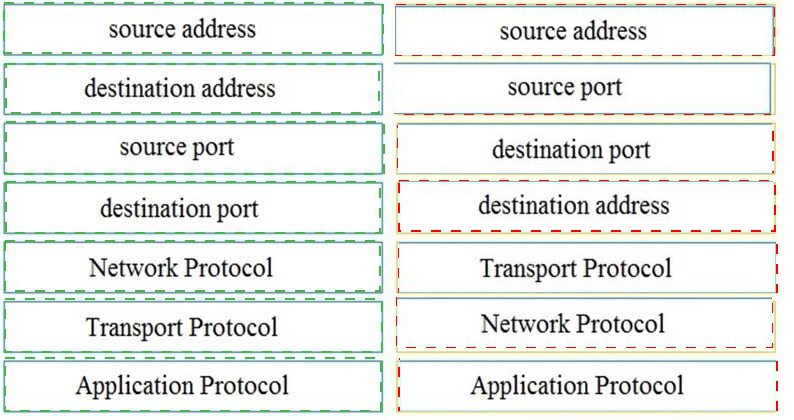
Drag and drop the technology on the left onto the data type the technology provides on the right.
At which layer is deep packet inspection investigated on a firewall?
A.
internet
B.
transport
C.
application
D.
data link
application
A security engineer deploys an enterprise-wide host/endpoint technology for all of the
company's corporate PCs. Management requests the engineer to block a selected set of
applications on all PCs.
Which technology should be used to accomplish this task?
A.
application whitelisting/blacklisting
B.
network NGFW
C.
host-based IDS
D.
antivirus/antispyware software
application whitelisting/blacklisting
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A.
ransomware communicating after infection
B.
users downloading copyrighted content
C.
data exfiltration
D.
user circumvention of the firewall
user circumvention of the firewall
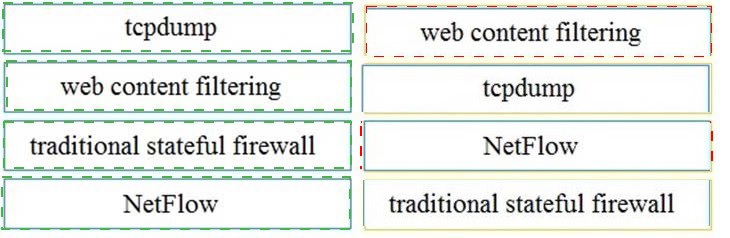
Refer to the exhibit.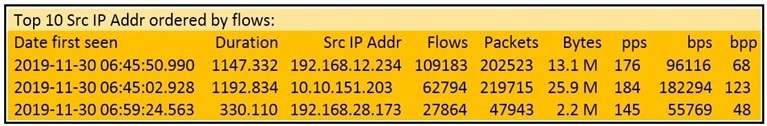
What information is depicted?
A.
IIS data
B.
NetFlow data
C.
network discovery event
D.
IPS event data
NetFlow data
| Page 7 out of 34 Pages |
| Previous |