Drag and drop the security concept on the left onto the example of that concept on the right.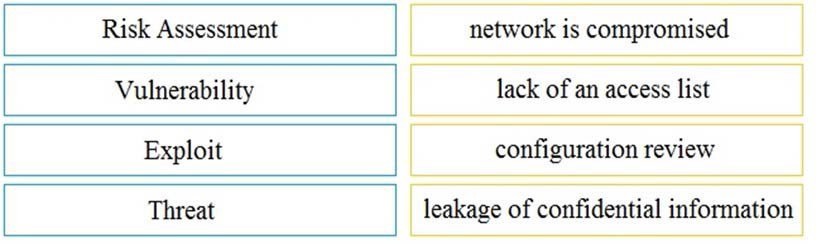
Refer to the exhibit.
What does the message indicate?
A.
an access attempt was made from the Mosaic web browser
B.
a successful access attempt was made to retrieve the password file
C.
a
D.
a denied access attempt was made to retrieve the password file
a
Which process is used when IPS events are removed to improve data integrity?
A.
data availability
B.
data normalization
C.
data signature
D.
data protection
data normalization
A user received a malicious attachment but did not run it.
Which category classifies the intrusion?
A.
weaponization
B.
reconnaissance
C.
installation
D.
delivery
delivery
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
A.
Tapping interrogation replicates signals to a separate port for analyzing traffic
B.
Tapping interrogations detect and block malicious traffic
C.
Inline interrogation enables viewing a copy of traffic to ensure traffic is in compliance with security policies
D.
Inline interrogation detects malicious traffic but does not block the traffic
Tapping interrogation replicates signals to a separate port for analyzing traffic
An offline audit log contains the source IP address of a session suspected to have
exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
A.
best evidence
B.
corroborative evidence
C.
indirect evidence
D.
forensic evidence
corroborative evidence
How does an SSL certificate impact security between the client and the server?
A.
by enabling an authenticated channel between the client and the server
B.
by creating an integrated channel between the client and the server
C.
by enabling an authorized channel between the client and the server
D.
by creating an encrypted channel between the client and the server
by creating an encrypted channel between the client and the server
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
What is the potential threat identified in this Stealthwatch dashboard?
A.
Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
B.
Host 152.46.6.91 is being identified as a watchlist country for data transfer.
C.
Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
D.
Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Which piece of information is needed for attribution in an investigation?
A.
proxy logs showing the source RFC 1918 IP addresses
B.
RDP allowed from the Internet
C.
known threat actor behavior
D.
802.1x RADIUS authentication pass arid fail logs
known threat actor behavior
What is a difference between inline traffic interrogation and traffic mirroring?
A.
Inline inspection acts on the original traffic data flow
B.
Traffic mirroring passes live traffic to a tool for blocking
C.
Traffic mirroring inspects live traffic for analysis and mitigation
D.
Inline traffic copies packets for analysis and security
Traffic mirroring passes live traffic to a tool for blocking
What specific type of analysis is assigning values to the scenario to see expected
outcomes?
A.
deterministic
B.
exploratory
C.
probabilistic
D.
descriptive
deterministic
Which category relates to improper use or disclosure of PII data?
A.
legal
B.
compliance
C.
regulated
D.
contractual
regulated
| Page 6 out of 34 Pages |
| Previous |