A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and
writes to a new PHP file on the webserver. Which event category is described?
A.
reconnaissance
B.
action on objectives
C.
installation
D.
exploitation
installation
Which type of attack occurs when an attacker is successful in eavesdropping on a
conversation between two
IP phones?
A.
known-plaintext
B.
replay
C.
dictionary
D.
man-in-the-middle
man-in-the-middle
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A.
The RST flag confirms the beginning of the TCP connection, and the ACK flag responds
when the data for the payload is complete
B.
BT
C.
The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D.
The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
A.
least privilege
B.
need to know
C.
integrity validation
D.
due diligence
least privilege
An analyst discovers that a legitimate security alert has been dismissed.
Which signature caused this impact on network traffic?
A.
true negative
B.
false negative
C.
false positive
D.
true positive
false negative
In a SOC environment, what is a vulnerability management metric?
A.
code signing enforcement
B.
full assets scan
C.
internet exposed devices
D.
single factor authentication
single factor authentication
An investigator is examining a copy of an ISO file that is stored in CDFS format.
What type of evidence is this file?
A.
data from a CD copied using Mac-based system
B.
data from a CD copied using Linux system
C.
data from a DVD copied using Windows system
D.
data from a CD copied using Windows
data from a CD copied using Linux system
Which type of evidence supports a theory or an assumption that results from initial
evidence?
A.
probabilistic
B.
indirect
C.
best
D.
corroborative
corroborative
Refer to the exhibit.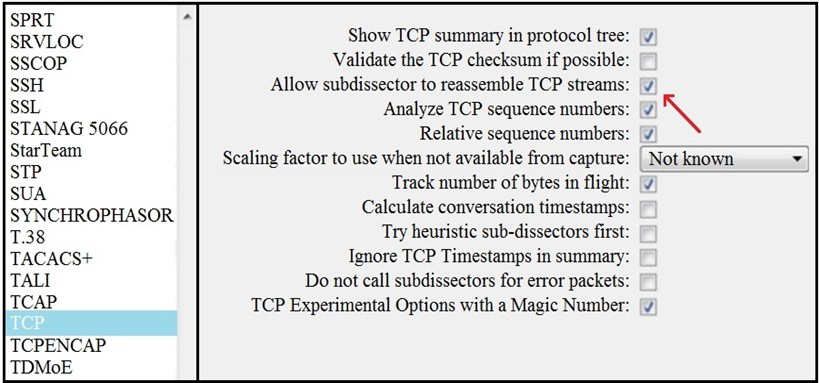 What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
A.
insert TCP subdissectors
B.
extract a file from a packet capture
C.
disable TCP streams
D.
unfragment TCP
unfragment TCP
Refer to the exhibit.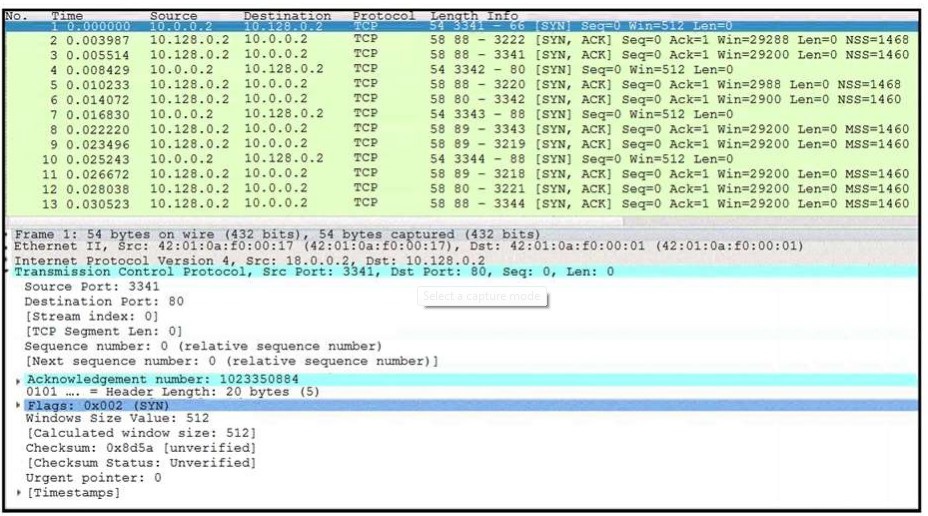 What is occurring in this network traffic?
What is occurring in this network traffic?
A.
high rate of SYN packets being sent from a multiple source towards a single destination IP
B.
high rate of SYN packets being sent from a single source IP towards multiple destination IPs
C.
flood of ACK packets coming from a single source IP to multiple destination IPs
D.
flood of SYN packets coming from a single source IP to a single destination IP
flood of SYN packets coming from a single source IP to a single destination IP
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
A.
confidentiality, identity, and authorization
B.
confidentiality, integrity, and authorization
C.
confidentiality, identity, and availability
D.
confidentiality, integrity, and availability
confidentiality, integrity, and availability
Which HTTP header field is used in forensics to identify the type of browser used?
A.
referrer
B.
host
C.
user-agent
D.
accept-language
user-agent
| Page 4 out of 34 Pages |
| Previous |