The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
A. Isolate the infected endpoint from the network.
B. Perform forensics analysis on the infected endpoint.
C. Collect public information on the malware behavior.
D. Prioritize incident handling based on the impact.
Explanation: According to the NIST Computer Security Incident Handling Guide, the next step in handling an event after confirming a potential indicator of compromise on an endpoint is to collect public information on the malware behavior. This step involves searching for information from various sources, such as antivirus vendors, security blogs, threat intelligence feeds, and online forums, to learn more about the characteristics, capabilities, and impact of the malware. This information can help the SOC team to identify the type, severity, and scope of the incident, as well as to determine the appropriate response actions and mitigation strategies. Isolating the infected endpoint, performing forensics analysis, and prioritizing incident handling are subsequent steps that follow after collecting public information on the malware behavior.
Refer to the exhibit.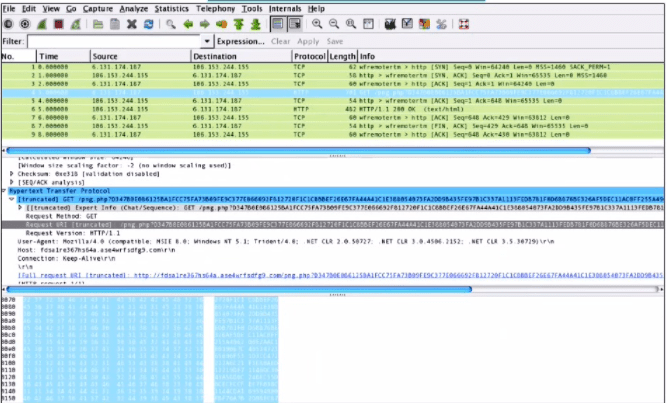
What is shown in this PCAP file?
A. Timestamps are indicated with error.
B. The protocol is TCP.
C. The User-Agent is Mozilla/5.0.
D. The HTTP GET is encoded
Explanation: The PCAP file shows a network packet capture of an HTTP GET request from a client to a server. The User-Agent header field identifies the type and version of the client software that generated the request. In this case, the User-Agent is Mozilla/5.0, which indicates that the client is using a Mozilla-based browser or application. The User- Agent can help the server to customize the response based on the client’s capabilities and preferences.
An engineer must configure network systems to detect command-and-control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology must be used to accomplish this task?
A. static IP addresses
B. signatures
C. digital certificates
D. cipher suite
Explanation: Digital certificates are essential for decrypting ingress and egress perimeter traffic, as they provide the necessary encryption keys for secure communications. By using digital certificates, network security devices can inspect the decrypted traffic to detect any malicious outbound communications that may indicate command-and-control activity.
What are the two differences between vulnerability and exploit? (Choose two.)
A. Known vulnerabilities are assigned special CVE numbers, and exploits are using process to take advantage of vulnerabilities.
B. Vulnerabilities can be found in hardware and software, and exploits can be used only for software-based vulnerabilities.
C. Zero-day exploit can be used to take advantage of a vulnerability until the vulnerable software or hardware is patched.
D. Vulnerabilities are usually populated in the dark web, and exploit tools and methods can be found in the public web.
E. Zero-day exploit can be used for taking advantage of a known vulnerability, and cyberattack can be performed on company assets.
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
A. management and reporting
B. traffic filtering
C. adaptive AVC
D. metrics collection and exporting
E. application recognition
Explanation: Cisco Application Visibility and Control (AVC) provides features like metrics collection and exporting (D) for visibility on TCP bandwidth usage, response time, and latency. Application recognition (E) combined with deep packet inspection helps in identifying unknown software by its network traffic flow.
What is a difference between SI EM and SOAR security systems?
A. SOAR ingests numerous types of logs and event data infrastructure components and SIEM can fetch data from endpoint security software and external threat intelligence feeds
B. SOAR collects and stores security data at a central point and then converts it into actionable intelligence, and SIEM enables SOC teams to automate and orchestrate manual tasks
C. SIEM raises alerts in the event of detecting any suspicious activity, and SOAR automates investigation path workflows and reduces time spent on alerts
D. SIEM combines data collecting, standardization, case management, and analytics for a defense-in-depth concept, and SOAR collects security data antivirus logs, firewall logs, and hashes of downloaded files
Explanation: SIEM (Security Information and Event Management) systems are designed to collect, correlate, and analyze security event data from various sources to provide insights into potential security issues. They raise alerts when detecting suspicious activities. SOAR (Security Orchestration, Automation, and Response) systems, on the other hand, focus on automating and orchestrating incident response processes. They automate investigation path workflows and reduce the time spent on alerts by executing predefined actions and workflows in response to security events or incidents. References: The differences between SIEM and SOAR are highlighted in various cybersecurity resources, including those provided by Palo Alto Networks and Exabeam, which explain that while SIEM primarily focuses on collecting and analyzing security event data, SOAR extends these capabilities through automation, orchestration, and predefined incident response playbooks.
Refer to the exhibit.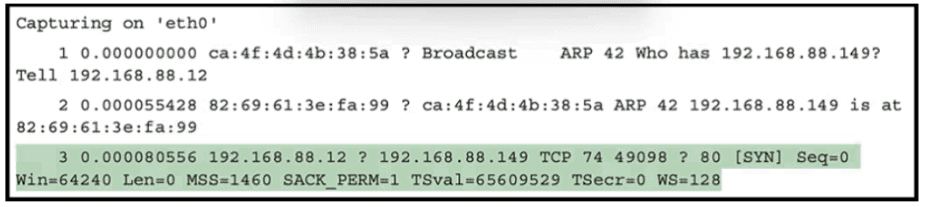
What must be interpreted from this packet capture?
A. IP address 192.168.88 12 is communicating with 192 168 88 149 with a source port 74 to destination port 49098 using TCP protocol
B. IP address 192.168.88.12 is communicating with 192 168 88 149 with a source port 49098 to destination port 80 using TCP protocol.
C. IP address 192.168.88.149 is communicating with 192.168 88.12 with a source port 80 to destination port 49098 using TCP protocol.
D. IP address 192.168.88.149 is communicating with 192.168.88.12 with a source port 49098 to destination port 80 using TCP protocol.
Explanation: The packet capture shows that IP address 192.168.88.149, using source port
80 (common for HTTP traffic), initiated communication with IP address 192.168.88.12 at
destination port 49098, using the TCP protocol, indicating a typical client-server interaction
over the web.
:= These explanations are based on general cybersecurity principles as outlined in Cisco’s
training and certification content, such as the Understanding Cisco Cybersecurity
Operations Fundamentals (CBROPS) and other related Cisco resources.
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
A. File: Clean
B. ^Parent File Clean$
C. File: Clean (.*)
D. ^File: Clean$
Explanation: A regular expression (regex) is a sequence of characters that defines a search pattern for text. A regex can be used to extract custom properties from log messages or events in a SIEM platform. In this case, the regex that matches the phrase “File: Clean” exactly is ^File: Clean$. The ^ symbol indicates the beginning of the line and the $ symbol indicates the end of the line. The regex ensures that no other characters are before or after the phrase.
Refer to the exhibit.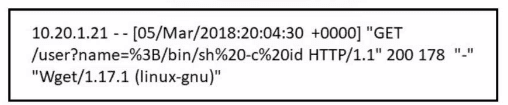
Which attack is being attempted against a web application?
A. SQL injection
B. man-in-the-middle
C. command injection
D. denial of service
Explanation:
Refer to the exhibit.
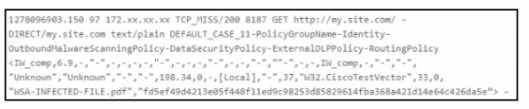
A. antivirus
B. IPS/IDS
C. proxy
D. firewall
Explanation: The log in the exhibit is generated by an Intrusion Prevention System (IPS) or Intrusion Detection System (IDS). It contains information about a TCP connection attempt, including the source IP address, destination IP address, and other details related to the connection. The presence of “TCP MISS” indicates that the system detected an anomaly or potential threat during the connection attempt.
What is the key difference between mandatory access control (MAC) and discretionary access control (DAC)?
A. DAC is controlled by the OS, and MAC is controlled by the owner of the access list.
B. DAC is the most strict access control, and MAC is object-based access.
C. MAC is controlled by the OS, and DAC is controlled by the owner of the access list.
D. MAC is the most strict access control, and DAC is object-based access.
How does an attack surface differ from an attack vector?
A. An attack vector recognizes the potential outcomes of an attack, and the attack surface is choosing a method of an attack.
B. An attack surface identifies vulnerable parts for an attack, and an attack vector specifies which attacks are feasible to those parts.
C. An attack surface mitigates external vulnerabilities, and an attack vector identifies mitigation techniques and possible workarounds.
D. An attack vector matches components that can be exploited, and an attack surface classifies the potential path for exploitation
Explanation: An attack surface is the sum of all the points where an attacker can try to enter or extract data from an environment. It includes all the hardware, software, network, and human components that are exposed to potential threats. An attack vector is the path or means by which an attacker can exploit a vulnerability in the attack surface. It describes the type, source, and technique of an attack, such as phishing, malware, denial-of-service, etc.
| Page 15 out of 34 Pages |
| Previous |