What is a purpose of a vulnerability management framework?
A.
identifies, removes, and mitigates system vulnerabilities
B.
detects and removes vulnerabilities in source code
C.
conducts vulnerability scans on the network
D.
manages a list of reported vulnerabilities
identifies, removes, and mitigates system vulnerabilities
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
A.
UDP port to which the traffic is destined
B.
TCP port from which the traffic was sourced
C.
source IP address of the packet
D.
IP address of the packet
E.
UDP port from which the traffic is sourced
source IP address of the packet
IP address of the packet
What is a difference between SOAR and SIEM?
A.
SOAR platforms are used for threat and vulnerability management, but SIEM
applications are not
B.
SIEM applications are used for threat and vulnerability management, but SOAR
platforms are not
C.
SOAR receives information from a single platform and delivers it to a SIEM
D.
SIEM receives information from a single platform and delivers it to a SOAR
SOAR platforms are used for threat and vulnerability management, but SIEM
applications are not
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
A.
installation
B.
reconnaissance
C.
weaponization
D.
delivery
installation
What is the difference between the rule-based detection when compared to behavioral detection?
A.
Rule-Based detection is searching for patterns linked to specific types of attacks, while behavioral is identifying per signature.
B.
Rule-Based systems have established patterns that do not change with new data, while behavioral changes.
C.
Behavioral systems are predefined patterns from hundreds of users, while Rule-Based only flags potentially abnormal patterns using signatures.
D.
Behavioral systems find sequences that match a particular attack signature, while Rule- Based identifies potential attacks
Behavioral systems find sequences that match a particular attack signature, while Rule- Based identifies potential attacks
Refer to the exhibit.
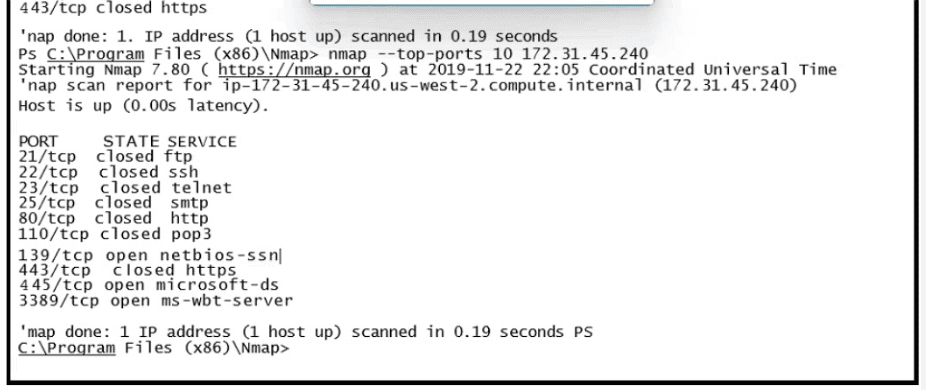
A.
HTTPS ports are open on the server.
B.
SMB ports are closed on the server.
C.
FTP ports are open on the server.
D.
Email ports are closed on the server.
HTTPS ports are open on the server.
Which regular expression is needed to capture the IP address 192.168.20.232?
A.
^ (?:[0-9]{1,3}\.){3}[0-9]{1,3}
B.
^ (?:[0-9]f1,3}\.){1,4}
C.
^ (?:[0-9]{1,3}\.)'
D.
^ ([0-9]-{3})
^ (?:[0-9]{1,3}\.){3}[0-9]{1,3}
Why is encryption challenging to security monitoring?
A.
Encryption analysis is used by attackers to monitor VPN tunnels.
B.
Encryption is used by threat actors as a method of evasion and obfuscation.
C.
Encryption introduces additional processing requirements by the CPU.
D.
Encryption introduces larger packet sizes to analyze and store.
Encryption is used by threat actors as a method of evasion and obfuscation.
What is vulnerability management?
A.
A security practice focused on clarifying and narrowing intrusion points.
B.
A security practice of performing actions rather than acknowledging the threats.
C.
A process to identify and remediate existing weaknesses.
D.
A process to recover from service interruptions and restore business-critical applications
A process to identify and remediate existing weaknesses.
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
A.
server name, trusted subordinate CA, and private key
B.
trusted subordinate CA, public key, and cipher suites
C.
trusted CA name, cipher suites, and private key
D.
server name, trusted CA, and public key
server name, trusted CA, and public key
A security incident occurred with the potential of impacting business services. Who performs the attack?
A.
malware author
B.
threat actor
C.
bug bounty hunter
D.
direct competitor
malware author
What is a sandbox interprocess communication service?
A.
A collection of rules within the sandbox that prevent the communication between sandboxes.
B.
A collection of network services that are activated on an interface, allowing for inter-port communication.
C.
A collection of interfaces that allow for coordination of activities among processes.
D.
A collection of host services that allow for communication between sandboxes.
A collection of rules within the sandbox that prevent the communication between sandboxes.
| Page 10 out of 34 Pages |
| Previous |